How Arcadia Finance lost $3.5m due to Lack of Input Validation
Discover how Arcadia Finance lost $3.5M to a smart contract exploit caused by missing input validation. Key insights and security lessons inside.

Arcadia Finance is an automated liquidity management protocol that enables users to rebalance their CLAMM positions seamlessly and efficiently.
On July 15, 2025, Arcadia was hit with an exploit that resulted in a loss of $3.5 million on the base chain, where the protocol was deployed. The attacker made multiple attack attempts, targeting the lack of validation in the protocol contracts.
Hack Analysis and Its Impact
Flow of Attack
- Initial Flashloan of 5623 WETH and 9968 cbBTC
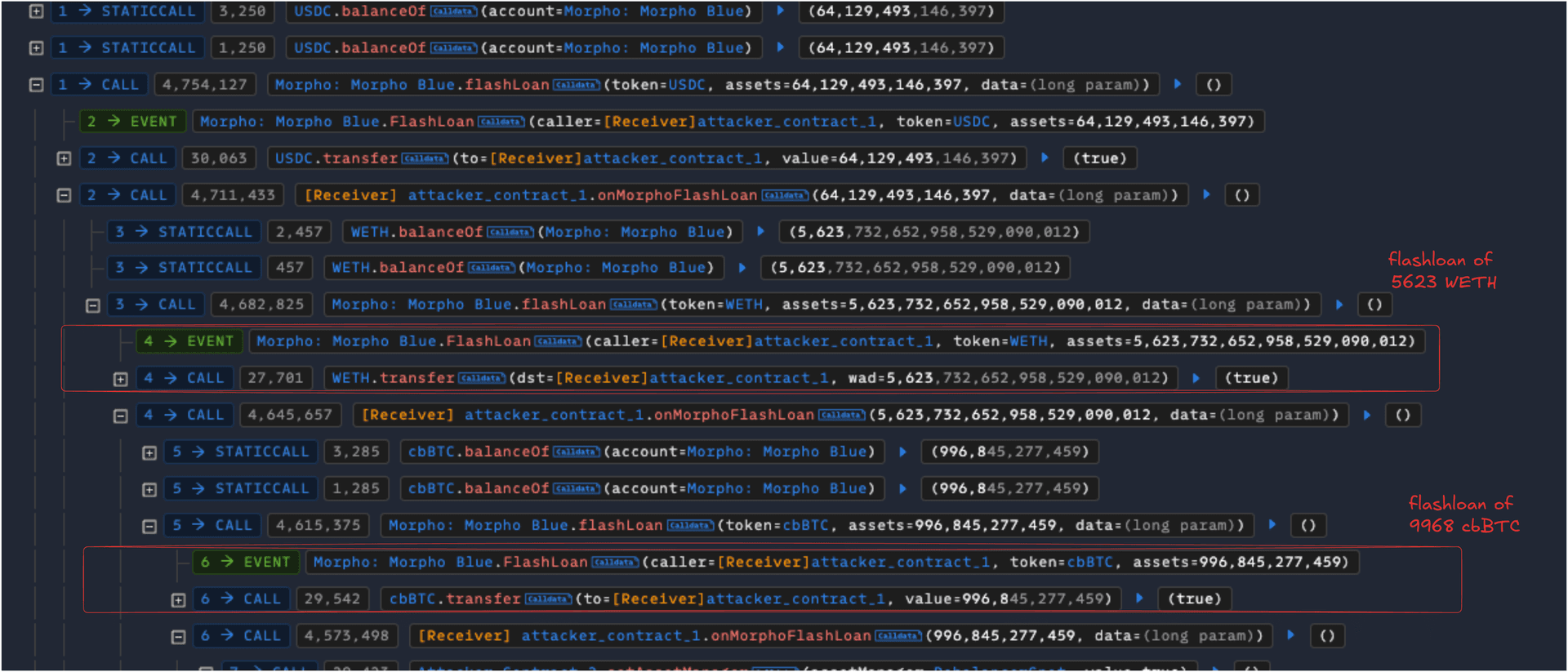
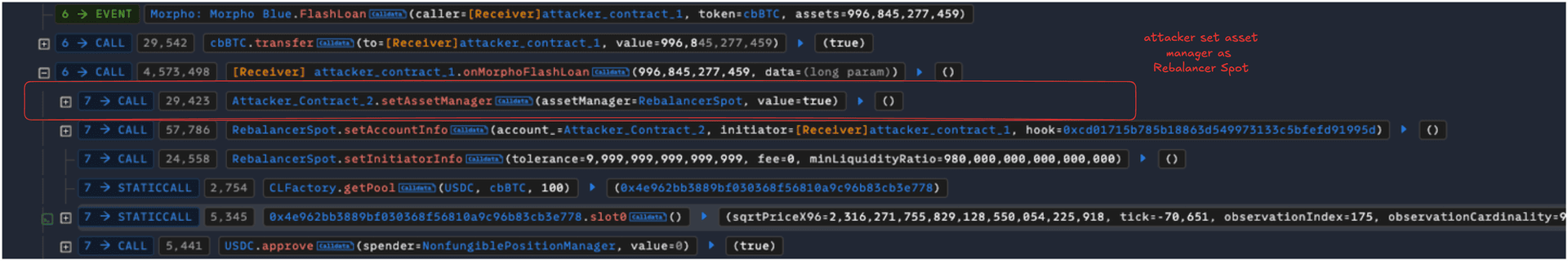
- The attacker set the asset manager as Rebalancer Spot, which is a normal user operation by calling setAssetManager function.
Once set, the Asset Manager can perform actions using the flashAction() function.
- The attacker minted an LP NFT with 1773 USDC and 0.123 cbBTC. They also repaid 14.4 cbBTC debt on behalf of the victim contract by the attacker to make the account bypass the health check.


- The attacker called
rebalancefunction onRebalancerSpotwith a maliciousswapData. Rebalance further calls theflashAction()function that enables Asset Managers to execute complex operations. It allows the chaining of multiple actions in a single transaction, including withdraw, direct transfers, executing any external logic, and depositing any resultant tokens back to the Arcadia Account.
Note: At the end of the flash action, a health check ensures the margin account remains solvent (collateral value > liabilities). If the check fails, the transaction reverts. This is why the debt needed to be repaid during the above steps.
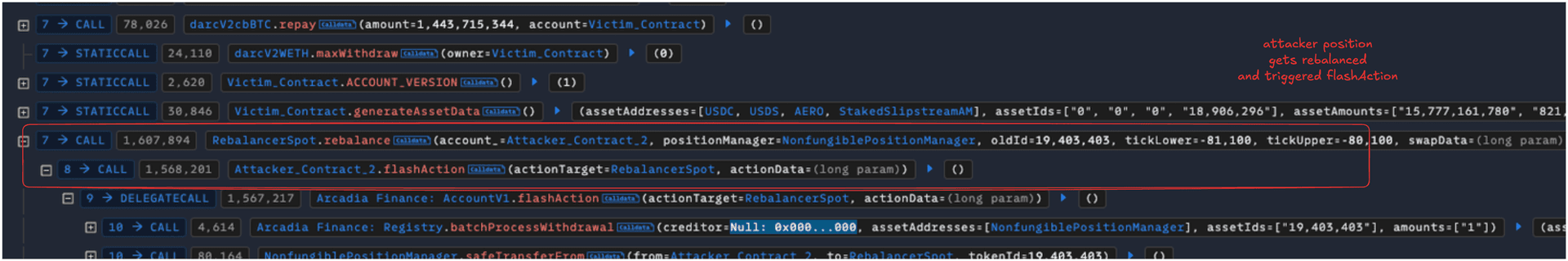
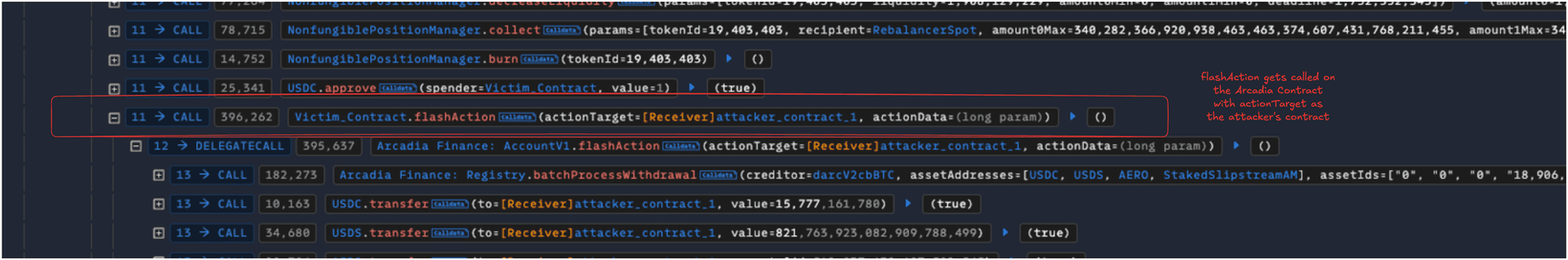
- The flawed swap data in the above step led the flashAction to withdraw various NFT LP positions to the attacker, where they removed the liquidity and made a profit.
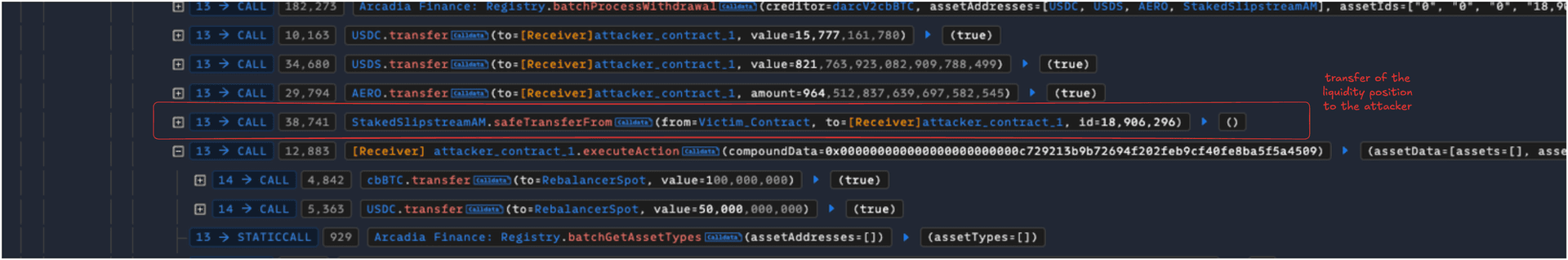
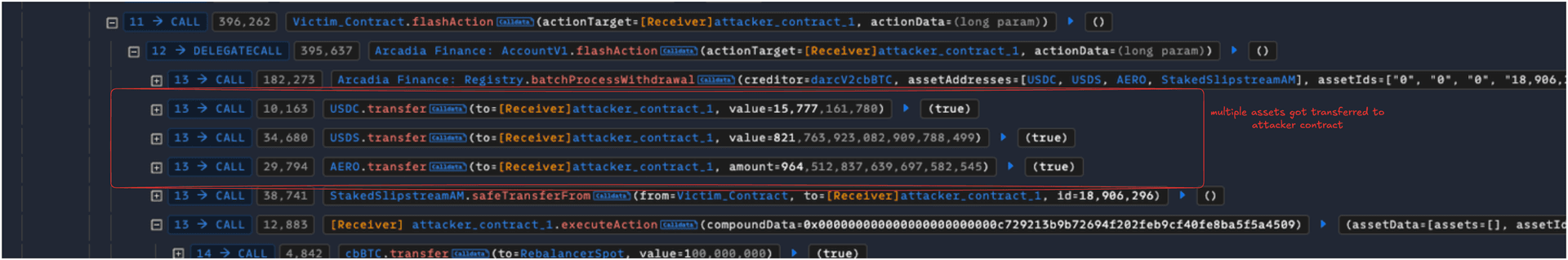
Root Cause Analysis
While calling the rebalance function, the account_ parameter is set to one of the attacker’s contracts at 0xa6c64. During this function call, the actionData is executed, which is encoded through the malicious swap data provided by the attacker, which led to a series of actions:
- The attacker removed their initially minted LP position from
RebalancerSpotcontract. - Rebalance’s contract
executeActionfunction which then executed_swap()function, which led to the calling of the swap router within the_swapfunction. - The router in the decoded malicious
swapDatawas the victim contract at 0x9529E. - From the victim's contract, the
flashActionis executed where NFT positions were transferred to the attacker’s contract. - The transferred NFT positions were then drained by removing the liquidity within it.
Don't Let Input Validation Flaws Drain Your Protocol!
Don't Let Input Validation Flaws Drain Your Protocol!
Arcadia’s $3.5M exploit proves how unchecked inputs can trigger huge losses. QuillAudits helps you detect and fix such flaws before attackers do.
1/**
2 * @notice Rebalances a UniswapV3 or Slipstream Liquidity Position, owned by an Arcadia Account.
3 * @param account_ The Arcadia Account owning the position.
4 * @param positionManager The contract address of the Position Manager.
5 * @param oldId The oldId of the Liquidity Position to rebalance.
6 * @param tickLower The new lower tick to rebalance to.
7 * @param tickUpper The new upper tick to rebalance to.
8 * @dev When tickLower and tickUpper are equal, ticks will be updated with same tick-spacing as current position
9 * and with a balanced, 50/50 ratio around current tick.
10 */
11 function rebalance(
12 address account_,
13 address positionManager,
14 uint256 oldId,
15 int24 tickLower,
16 int24 tickUpper,
17 bytes calldata swapData
18 ) external {
19 // If the initiator is set, account_ is an actual Arcadia Account.
20 if (account != address(0)) revert Reentered();
21 if (accountToInitiator[account_] != msg.sender) revert InitiatorNotValid();
22
23 // Store Account address, used to validate the caller of the executeAction() callback and serves as a reentrancy guard.
24 account = account_;
25
26 // Encode data for the flash-action.
27 bytes memory actionData =
28 ArcadiaLogic._encodeAction(positionManager, oldId, msg.sender, tickLower, tickUpper, swapData);
29
30 // Call flashAction() with this contract as actionTarget.
31 IAccount(account_).flashAction(address(this), actionData);
32
33 // Reset account.
34 account = address(0);
35 }Relevant Addresses and Transaction
Attacker Contract: 0x6250DFD35ca9eee5Ea21b5837F6F21425BEe4553
Attacker Wallet: 0x0fa54E967a9CC5DF2af38BAbC376c91a29878615
Victim Contract: 0x9529E5988ceD568898566782e88012cf11C3Ec99
Rebalancer Spot: 0xC729213B9b72694F202FeB9cf40FE8ba5F5A4509
Exploit Transaction: https://basescan.org/tx/0x06ce76eae6c12073df4aaf0b4231f951e4153a67f3abc1c1a547eb57d1218150
Fund Flow Post Attack
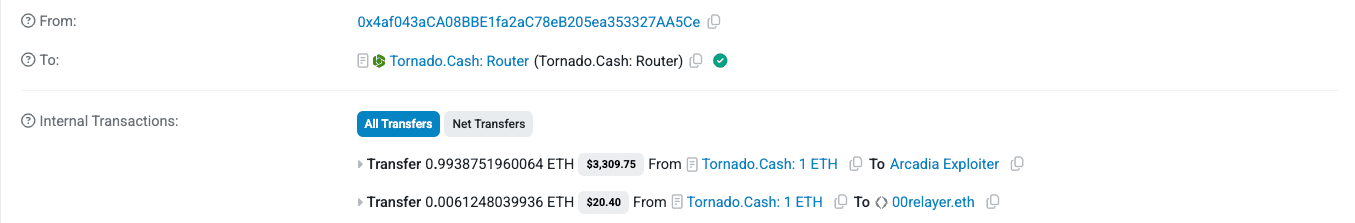
The attacker was funded with 1ETH through Tornado Cash on July 14th in the transaction: https://etherscan.io/tx/0xf5300504d25e930bd0e11e968d2d77a3c8effe1c56e583150226be084375ee3c
The stolen 1203 ETH is still in the attacker’s wallet at 0x0fa54, which was bridged from Base to Ethereum via Across Protocol.
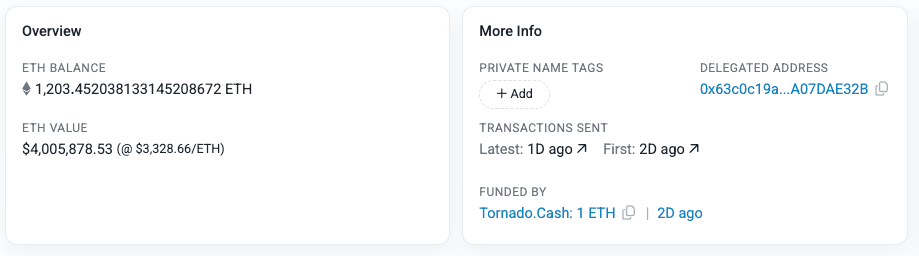
Arcadia team reached out to the attacker in the transaction with no signs of recovery: https://etherscan.io/tx/0xb1025d7313de0283b1a9cae514e207541d4f45bbc1cf2800f6e3aba0a35b878b
How the Hack Could Have Been Prevented?
The lack of validation of the swapData from the entry point in the rebalance function that also led to the calling of other functions. The corresponding function calls also lacked validation of the data that led to the transfer of the liquidity positions from the victim contract to the attacker’s contract.
Conclusion
Arcadia Finance was exploited for $3.5 million, with the root cause being a lack of validation of the input data, which attacked one of the contracts. The attacker carefully crafted the data input in one of the contract’s functions rebalance and executed the attack.
At QuillAudits, with our 7+ years of experience and 1M+ lines audited, we aim to identify bugs like this and give suggestion to improve it. We follow a multi-layered auditing framework, which comprises our core team and an external team of researchers reviewing the contracts, adding an extra layer of scrutiny for the protocols.
Contents



