BetterBank Exploit: $5M Lost in Reward Hack
A major exploit hit BetterBank, resulting in a $5M loss from a reward hack. Learn how this security breach unfolded and its impact on users.

On August 27, 2025, BetterBank, a decentralized lending protocol on PulseChain, suffered a liquidity manipulation and reward minting exploit, leading to losses of roughly $5 million. The attacker abused the protocol’s bonus minting mechanism for its native tokens FAVOR and ESTEEM, exploiting flaws in the reward distribution logic.
The vulnerability stemmed from BetterBank’s automated bonus distribution system, which minted ESTEEM tokens whenever liquidity was provided for FAVOR. Any trading activity involving FAVOR triggered additional ESTEEM rewards, creating a design flaw that could be manipulated through fake liquidity pools and wash trading.
Importantly, Zokyo had highlighted a similar risk during a prior audit, flagging the potential for fake liquidity pools and reward farming as an attack vector. However, the issue was later classified as “Low” severity and left unresolved.
In the executed exploit, the attacker ultimately drained approximately 891M DAI, 9.05B PLSX, and 7.40B WPLS.
Hack Analysis
Attacker deploys a malicious contract and initiates a flash loan from BetterBank, borrowing 50M DAI and 7.14B PLP tokens for the DAI–PDAIF pair.
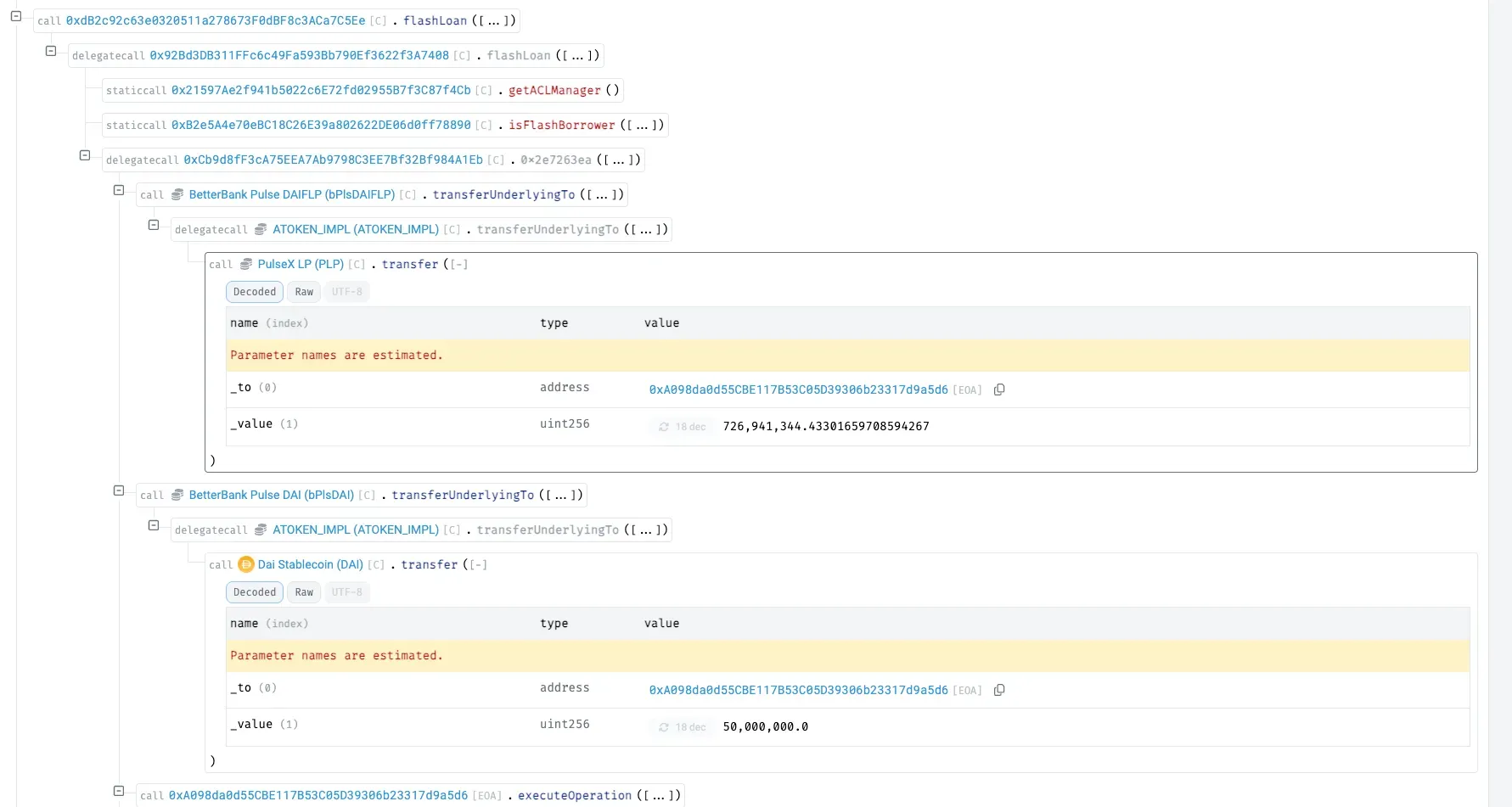
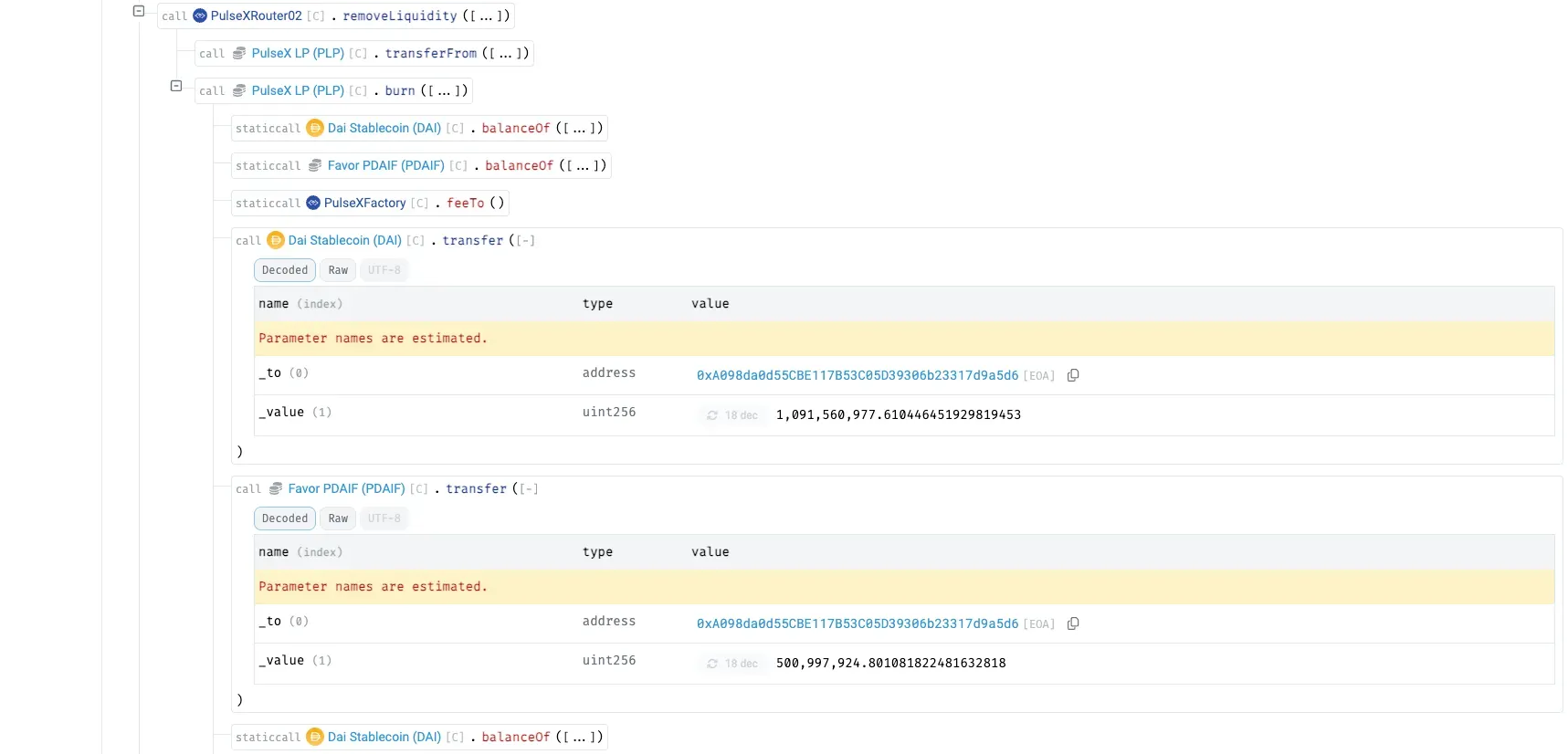
Using the borrowed PLP, the attacker invokes removeLiquidity on PulseXRouter02 , draining the real DAI–PDAIF pool and extracting ~1.09B DAI and 500M PDAIF from reserves.
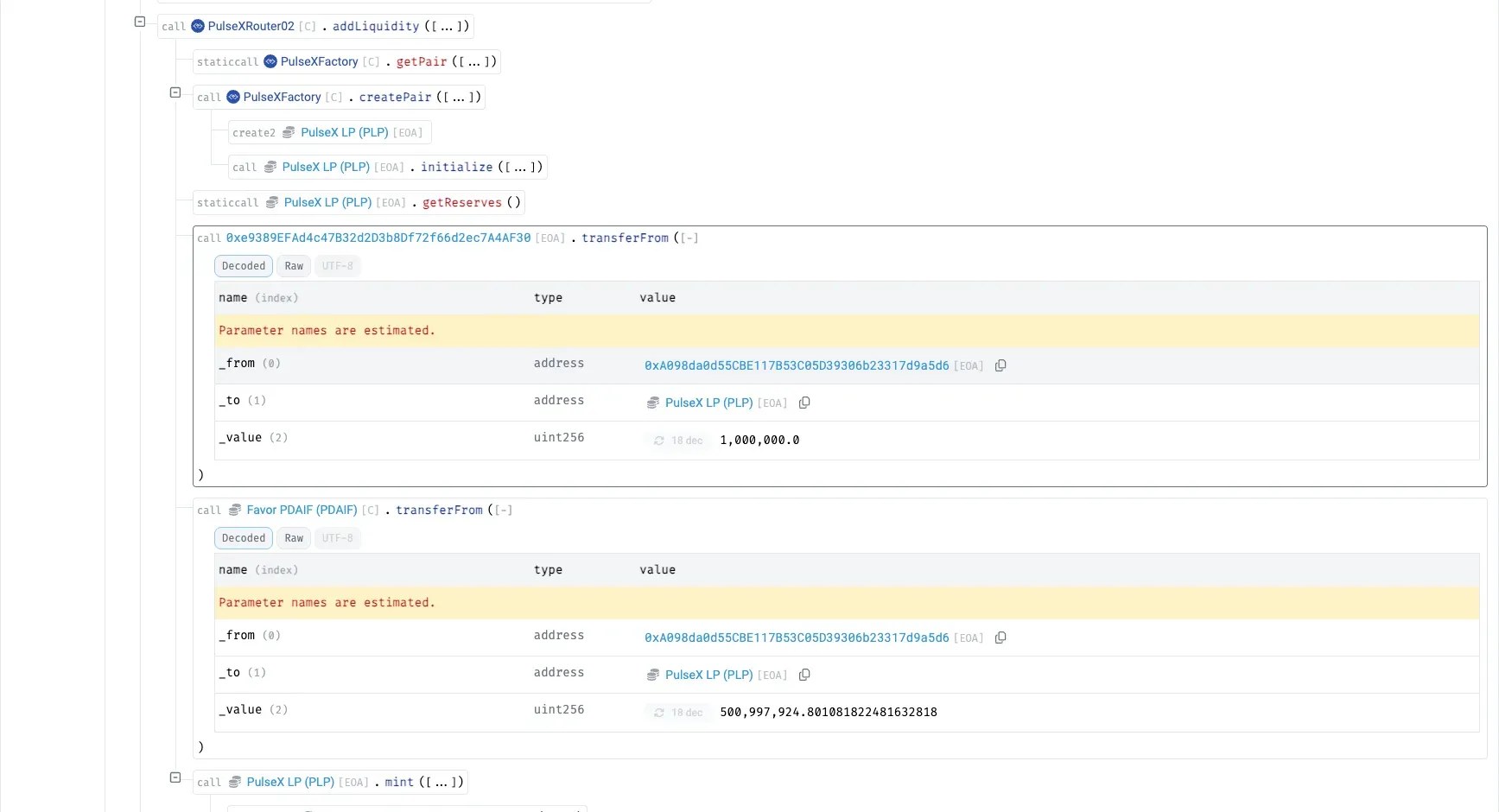
Attacker deploys a bogus ERC20 token and creates a fake bogus–PDAIF pool on PulseXFactory , adding minimal liquidity with the bogus token and draining PDAIF.
Through ~20 iterations of swapping the PDAIF ⇆ bogus token in the fake pool, the attacker manipulates PDAIF’s logBuy events and oracle consult function to simulate high buy volume, minting ESTEEM rewards.
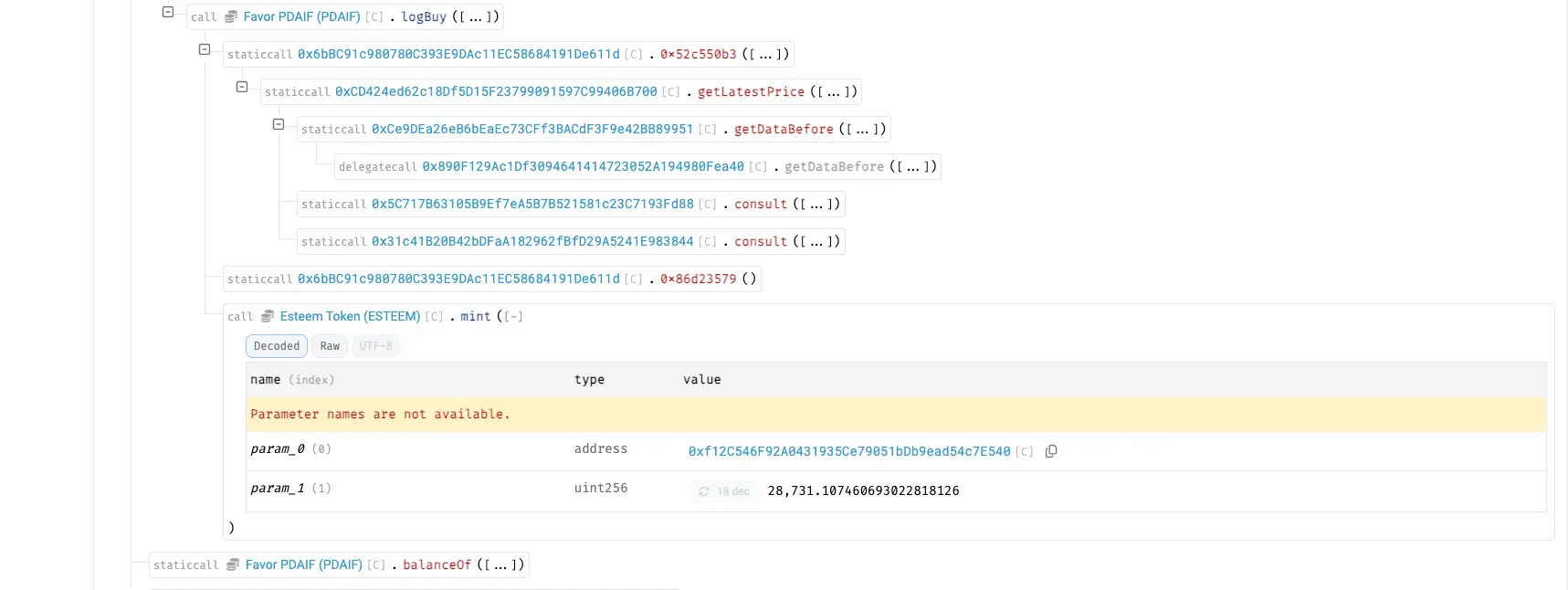
The attacker claims the Esteem rewards and uses burnFrom to convert them into ~3.8B additional PDAIF, inflating their token supply.
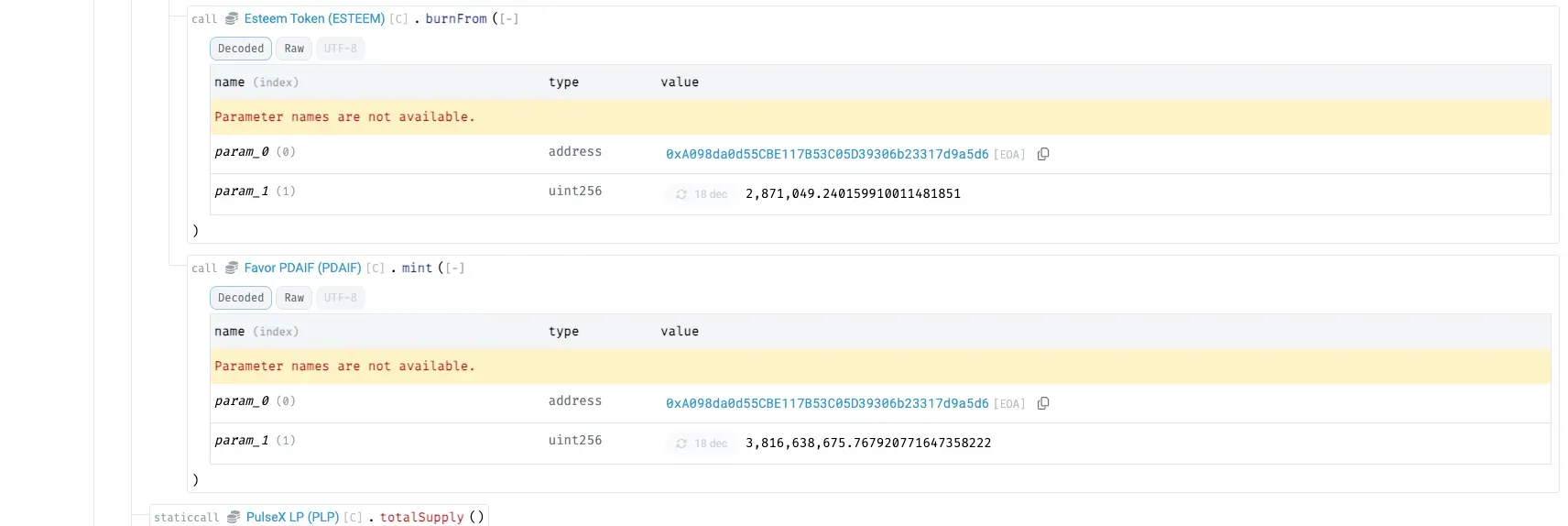
Liquidity is re-added into the real DAI–PDAIF pool via PulseXRouter02 with ~1.09B DAI and ~501M PDAIF, rebuilding the pool with an intentional imbalance (excess PDAIF) and yielding new LP tokens.
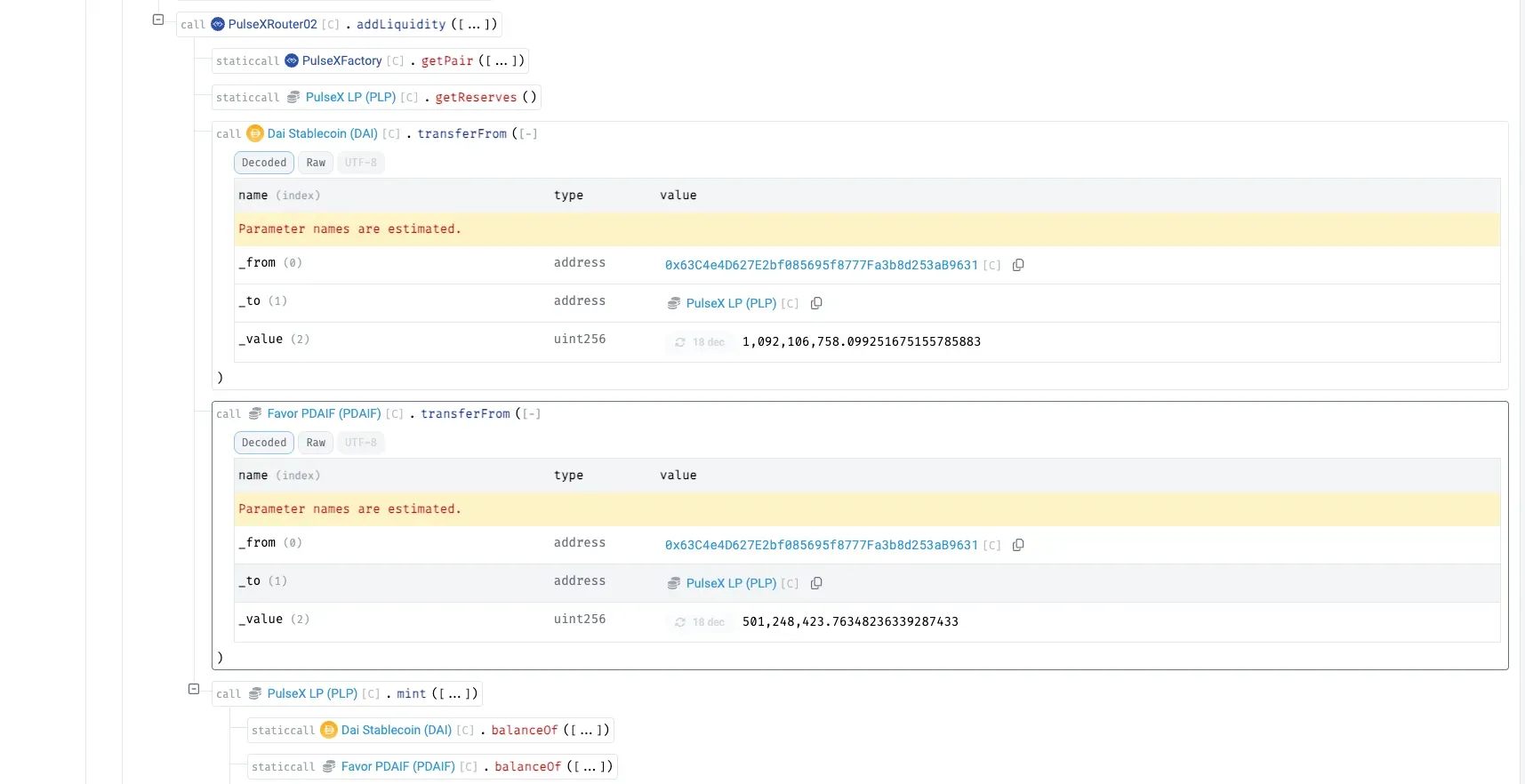
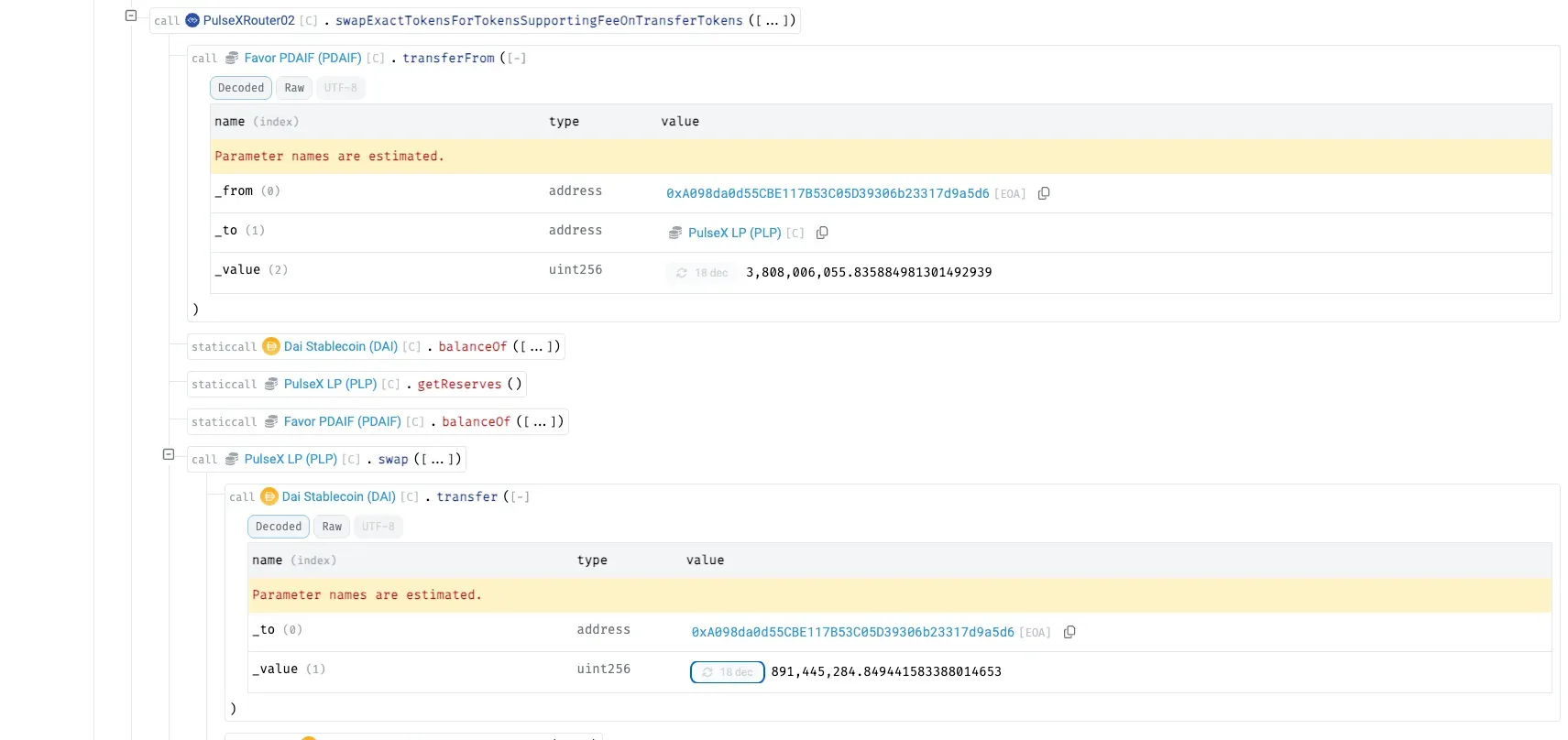
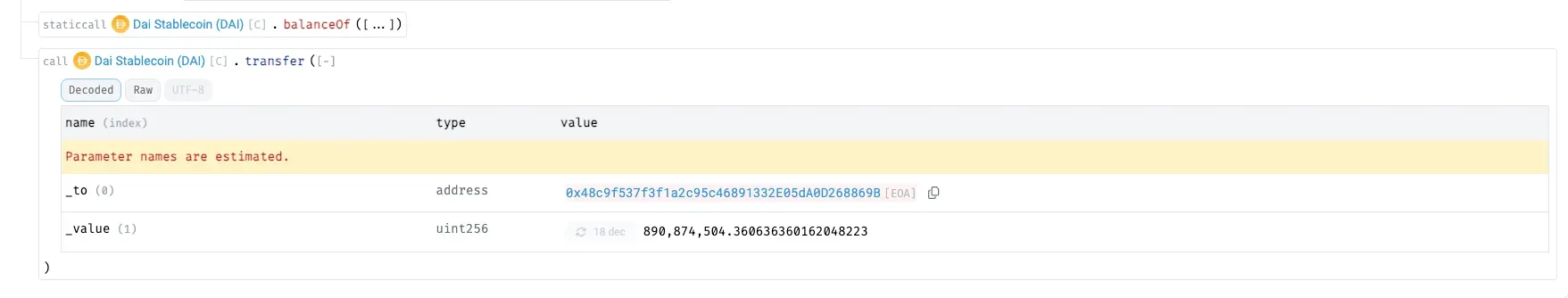
Exploiting the imbalance, the attacker swaps the surplus PDAIF for ~891M DAI at an above-market rate.
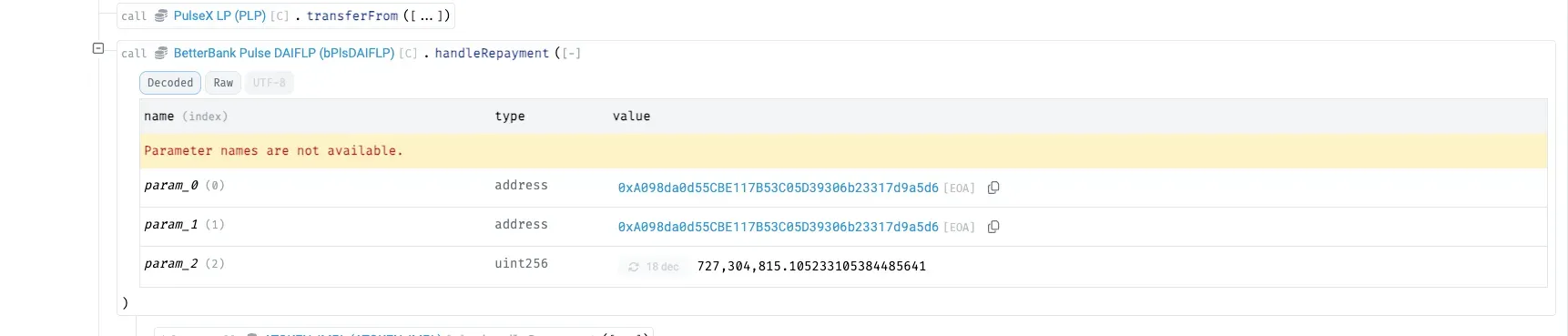
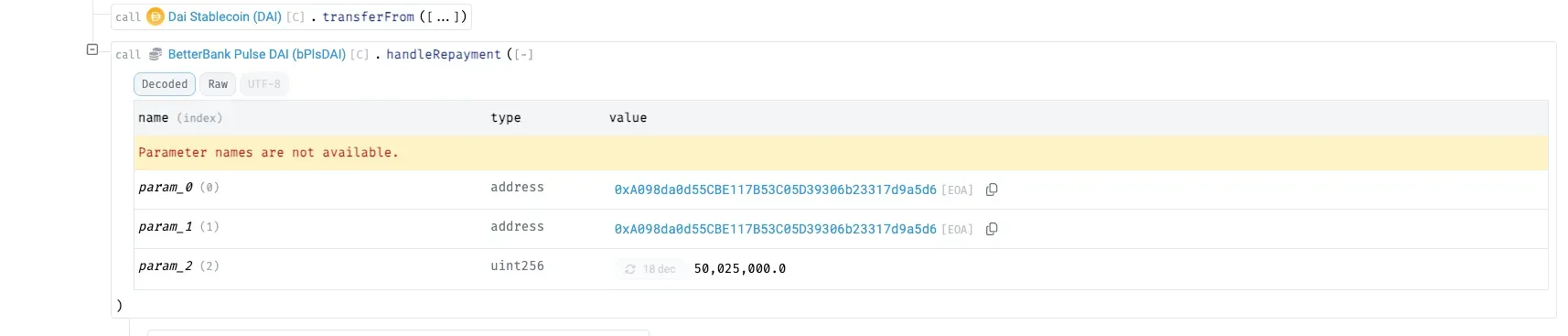
Borrowed amounts are repaid via handleRepayment , with the attacker returning the flash-loaned DAI and LP tokens to BetterBank while retaining ~891M DAI as profit.
The attacker went on to repeat the exploit with other tokens as well, managing to pull out around 9.05B PLSX and about 7.40B WPLS.
Don’t Let “Low Severity” Risks Cost You Millions!
Don’t Let “Low Severity” Risks Cost You Millions!
A small audit miss can turn into a million-dollar exploit. QuillAudits makes sure no loophole is left unchecked secure your protocol before it’s too late.
Root Cause
- Flawed reward logic in
swapExactTokensForFavorAndTrackBonus: The function only verified that the swap output wasFAVOR, and triggered ESTEEM reward minting. It did not validate whether the swap occurred through a legitimate/whitelisted pool.
- Convertible rewards vulnerability in
favorPLS: The minted ESTEEM rewards could then be converted back into FAVOR, enabling the attacker to loop the process and inflate supply.
- Audit warning overlooked: Although Zokyo had previously highlighted the risk of fake liquidity pool reward farming, the issue was downgraded to Low severity and not remediated.
Relevant Address and Transactions
- Attacker EOAs:
- Attacker Helper Contracts on PulseChain:
- PulseXRouter02: 0x165C3410fC91EF562C50559f7d2289fEbed552d9
- WPLS: 0xA1077a294dDE1B09bB078844df40758a5D0f9a27
- PLSX: 0x95B303987A60C71504D99Aa1b13B4DA07b0790ab
- DAI: 0x6B175474E89094C44Da98b954EedeAC495271d0F
Funds Flow After Attack
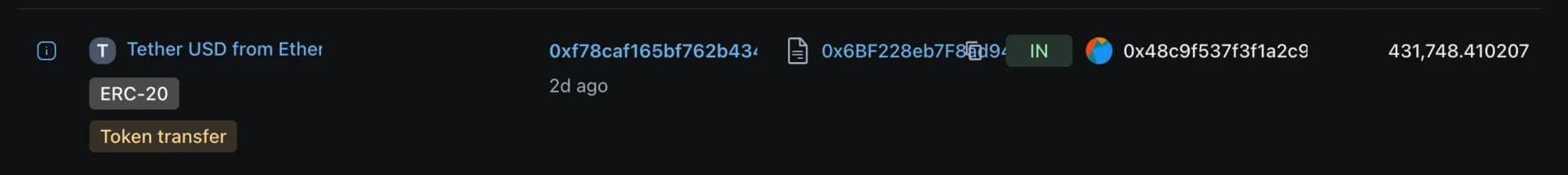
The attacker liquidated the stolen assets (~890M pDAI, 9B PulseX, and 7B Pulse, worth around $5M) by swapping them on PulseChain DEXes. The swaps were converted into Ethereum-based tokens, including USDC, USDT, DAI, and ETH.
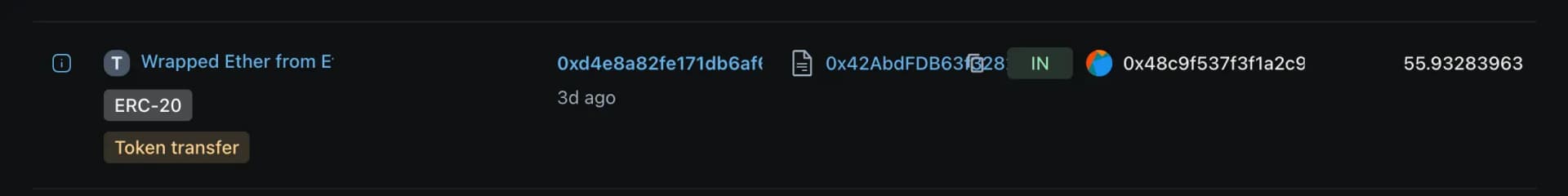
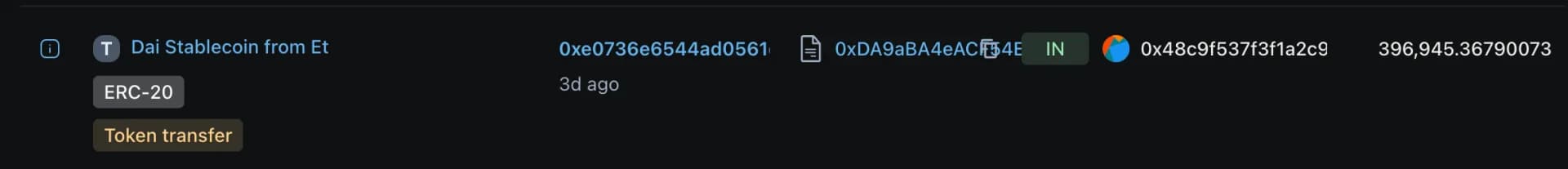
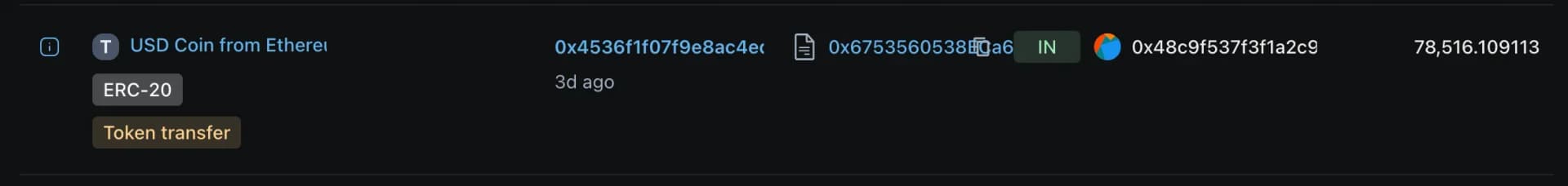
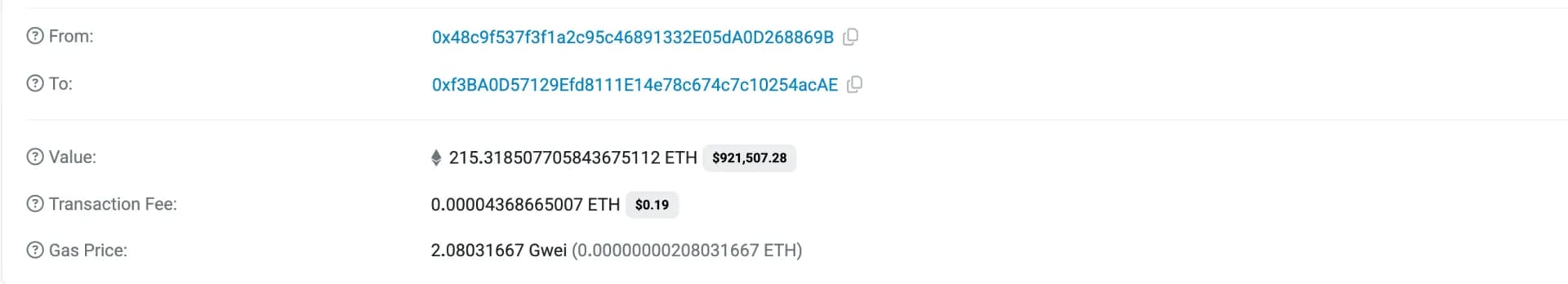
The attacker bridged approximately $922K worth of ETH from PulseChain to Ethereum, gaining easier access and higher liquidity.
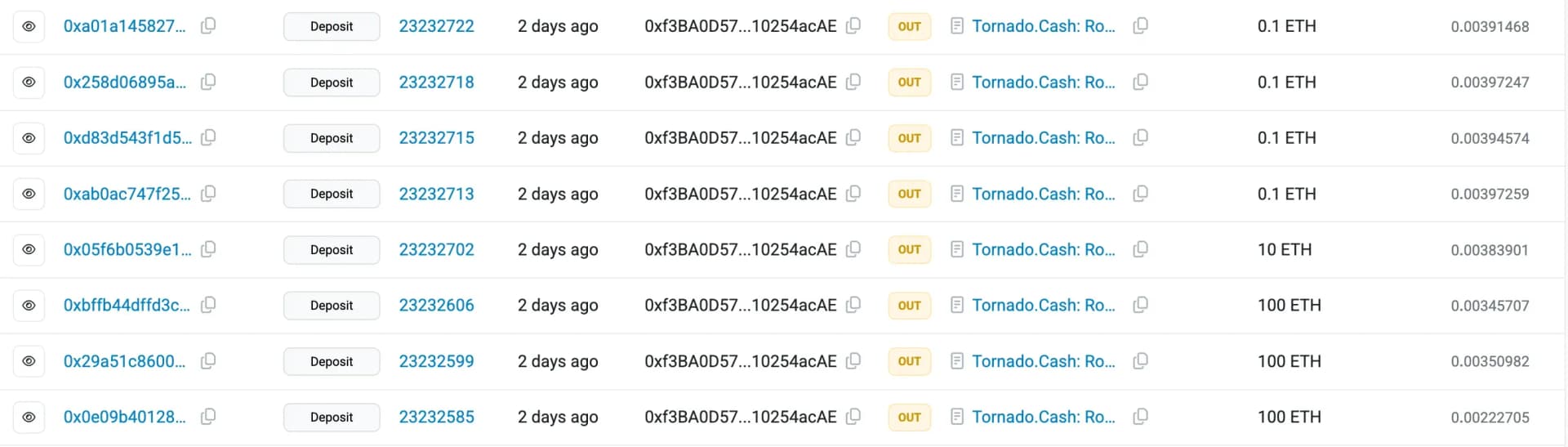
To launder the proceeds, the attacker routed the ETH through Tornado Cash, obscuring transaction traceability.
Post Attack Mitigation
Following the exploit, BetterBank drained all FAVOR pools to protect remaining assets, issued a 20% bounty for information on the attacker, and attempted on-chain negotiations for fund recovery. On August 27, 2025, the attacker returned 550M DAI (~$2.7M), reducing their net profit to about $1.4M. The team also announced plans to patch the vulnerability, relaunch updated ESTEEM and FAVOR contracts with airdrops to genuine holders, and use treasury and recovered LP assets to forgive debt and stabilize the protocol before reopening.
Conclusion
The BetterBank exploit highlights the inherent risks of poorly validated reward-based tokenomics. By abusing unchecked reward minting and fake liquidity pools, the attacker was able to inflate supply and drain protocol reserves. This case reinforces three key lessons:
- Reward minting must be restricted to whitelisted pools or registry contracts.
- Token-level validation is safer than pair-level enforcement.
- Audit findings, even low-severity, should not be dismissed without remediation.
Despite partial fund recovery, the incident shows that design flaws in incentive mechanisms can cause losses on par with major lending or oracle exploits, underscoring the need for a thorough security audit with QuillAudits.
Contents



