Griffin AI Exploit: Admin EOA Compromise Explained
Griffin AI lost $3.5M in a cross-chain exploit within 24 hours of its Binance Alpha launch. An admin wallet compromise let the attacker abuse LayerZero’s peer validation to mint 5B $GAIN tokens. This report breaks down the exploit, fund flow, root cause, and Griffin AI’s response, with key lessons for cross-chain security.

On September 24, 2024, less than 24 hours after its launch on Binance Alpha, the Griffin AI protocol suffered a devastating cross-chain exploit, resulting in a loss of $3.5 million. The attack exploited LayerZero's peer trust system by convincing the bridge infrastructure that a malicious Ethereum contract was legitimate, enabling the unauthorized minting of 5 billion $GAIN tokens, inflating the total supply from 1 billion to 5.2985 billion tokens.
Griffin AI operates as a Web3 AI project that has recently launched with carefully planned tokenomics featuring a maximum supply of 1 billion tokens. The protocol utilized LayerZero for cross-chain functionality, which became the attack vector when an administrator's access was compromised, allowing the attacker to manipulate the peer validation system.
Hack Analysis
The exploit was executed through a carefully orchestrated sequence of steps exploiting a compromised admin address and LayerZero's cross-chain peer configuration. Below is a detailed breakdown of the attack:
The attacker likely gained control of an admin EOA on the BNB Chain (0x54a978238984d581edd3a9359dda9be53a930a7e), possibly through a phishing attack. This is evidenced by the transaction 0xf867a8e0b73cc279075cc760747b2a6a552bfa4623ad302f78d5516cb3062d88, where the attacker used the compromised admin to call the setPeer function on the legitimate GriffinAI token contract, an OmniFungible Token (OFT) on LayerZero. The function designated a fraudulent OFT token on Ethereum (0xba159054636E69080Ae7C756319e5C85498EFEb0) as a trusted peer, falsely legitimizing it for cross-chain interactions.
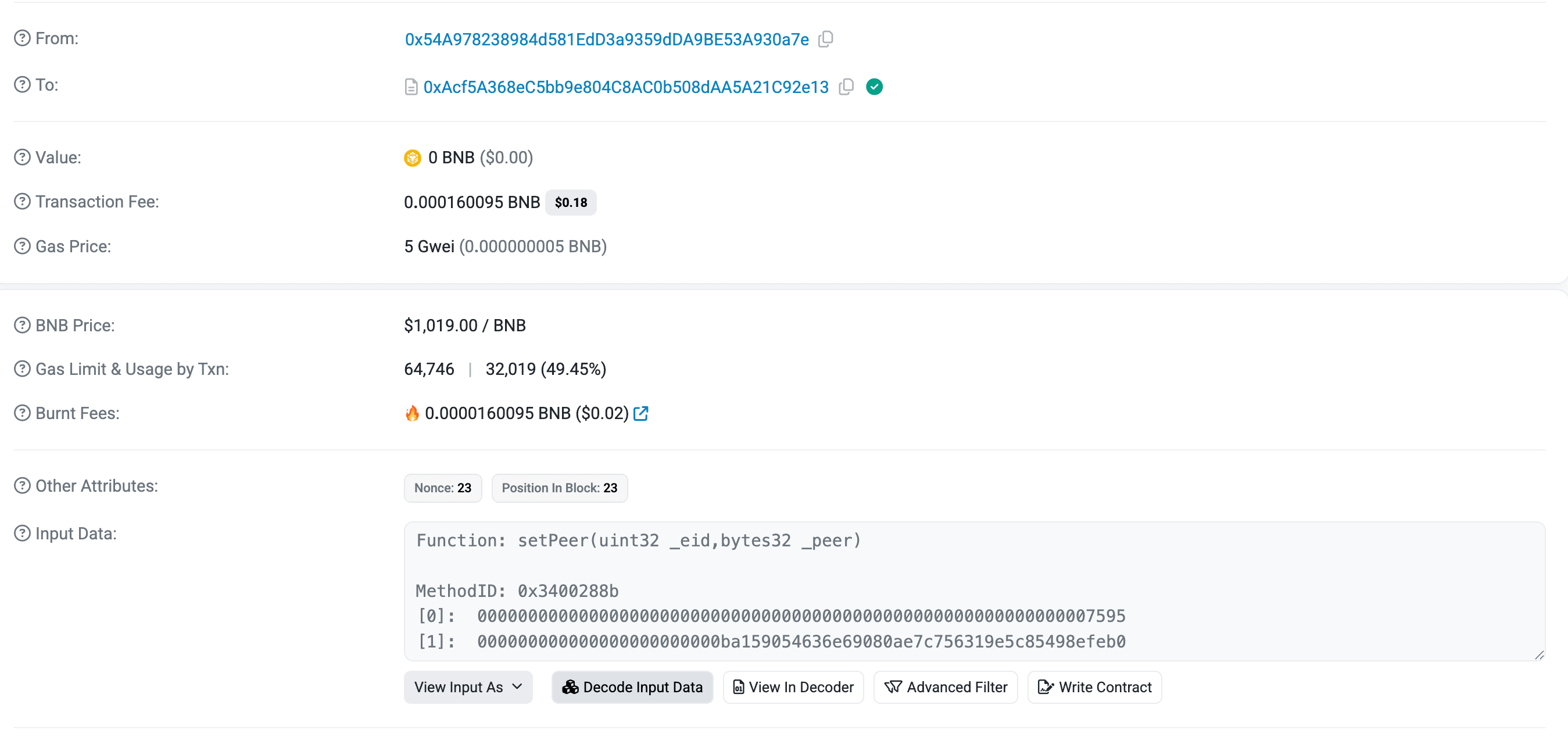
The attacker’s deployed counterfeit OFT token on Ethereum and configured the legitimate GriffinAI OFT token on the BNB Chain (0xAcf5A368eC5bb9e804C8AC0b508dAA5A21C92e13) as its peer. Using this setup, the attacker minted 5 billion fake tokens (referred to as $TTTTT) on Ethereum.
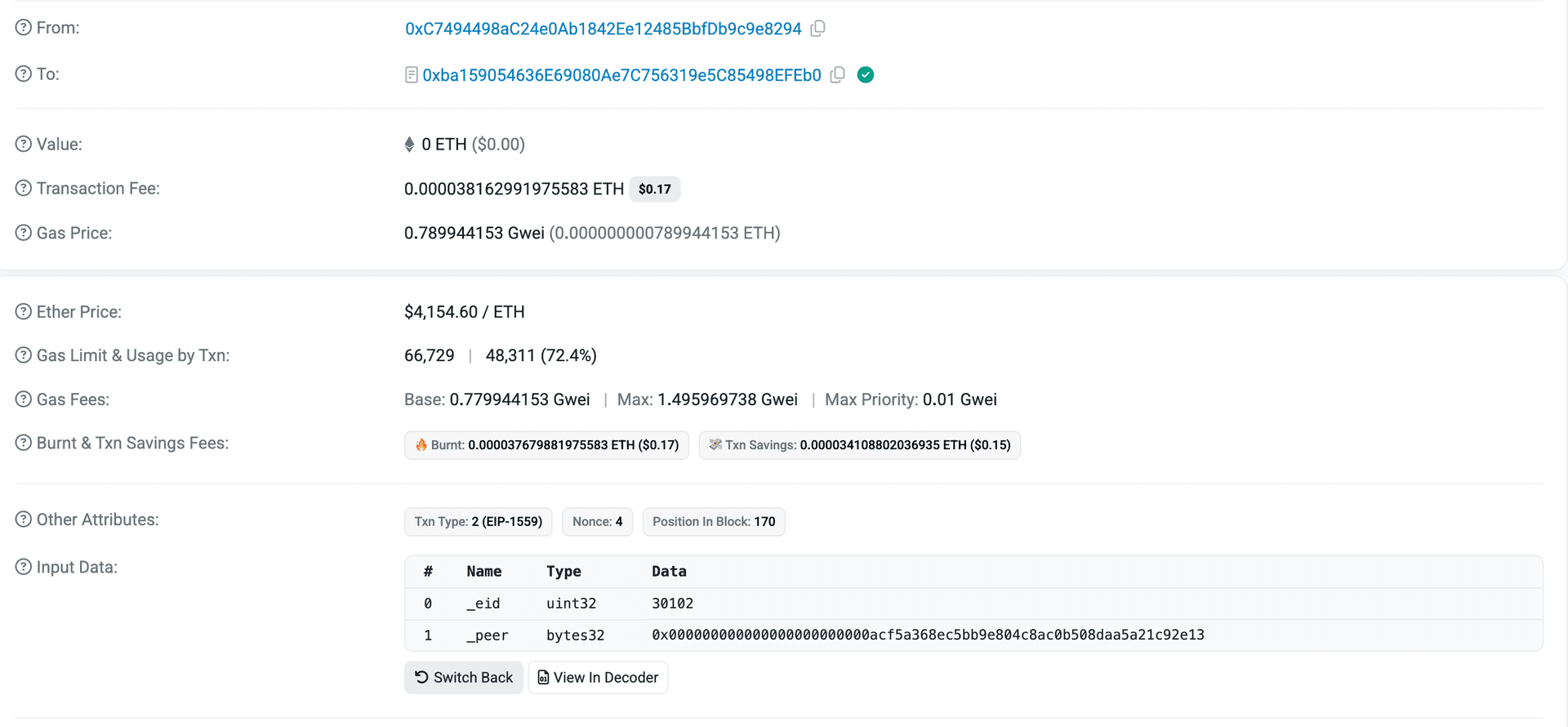
The attacker bridged the 5 billion $TTTTT tokens from Ethereum to the BNB Chain via LayerZero. Due to the manipulated peer configuration, this action triggered the minting of 5 billion legitimate $GAIN tokens on the BNB Chain, exploiting the trust relationship established in the setPeer call.
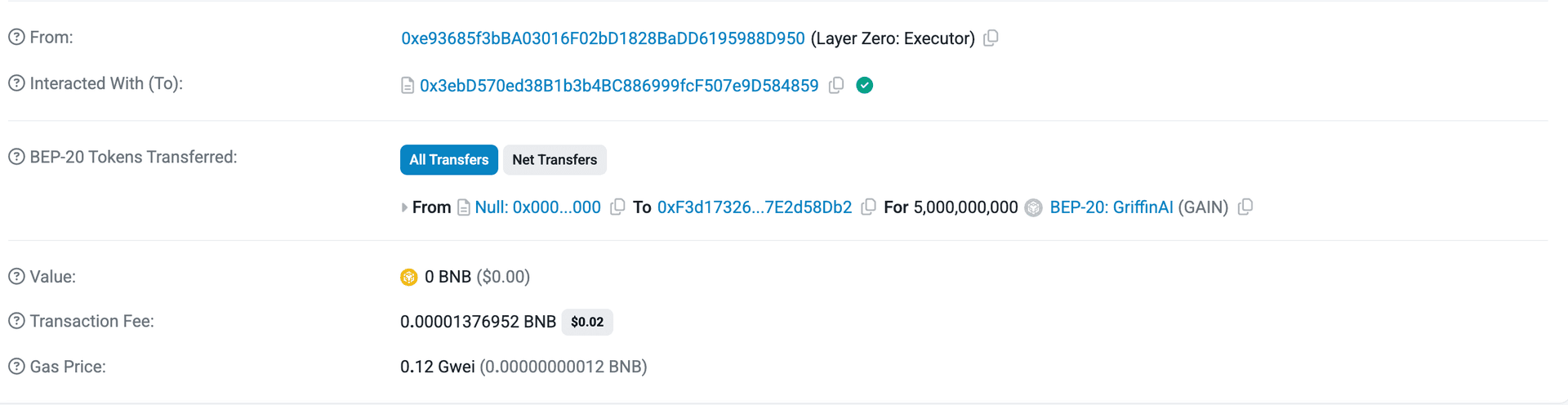
The attacker swapped the 5 billion $GAIN tokens for stablecoins on PancakeSwap, executing multiple transactions.
The attacker converted the stablecoins to ~876 ETH using deBridge to transfer the funds to Ethereum. The majority of these funds were laundered through Tornado Cash to obscure their trail, with approximately 29 ETH remaining in the address 0x469CF0E22403E1af404926a25eadB34a7Bd85F4d.

Root Cause
The primary vulnerability stemmed from the unauthorized configuration of a LayerZero peer using a compromised admin address 0x54a978238984d581edd3a9359dda9be53a930a7e. By invoking the setPeer The attacker established trust with a malicious contract, effectively bypassing LayerZero's cross-chain security protocols. This allowed arbitrary minting without proper verification.
Funds Flow After Attack
Following the minting and dumping, the attacker bridged the proceeds to Ethereum via deBridge, obtaining ~876 ETH. The full amount was subsequently laundered through Tornado Cash to obscure the trail. Approximately 29 ETH remains in the address 0x469CF0E22403E1af404926a25eadB34a7Bd85F4d, with recent inflows indicating ongoing activity.

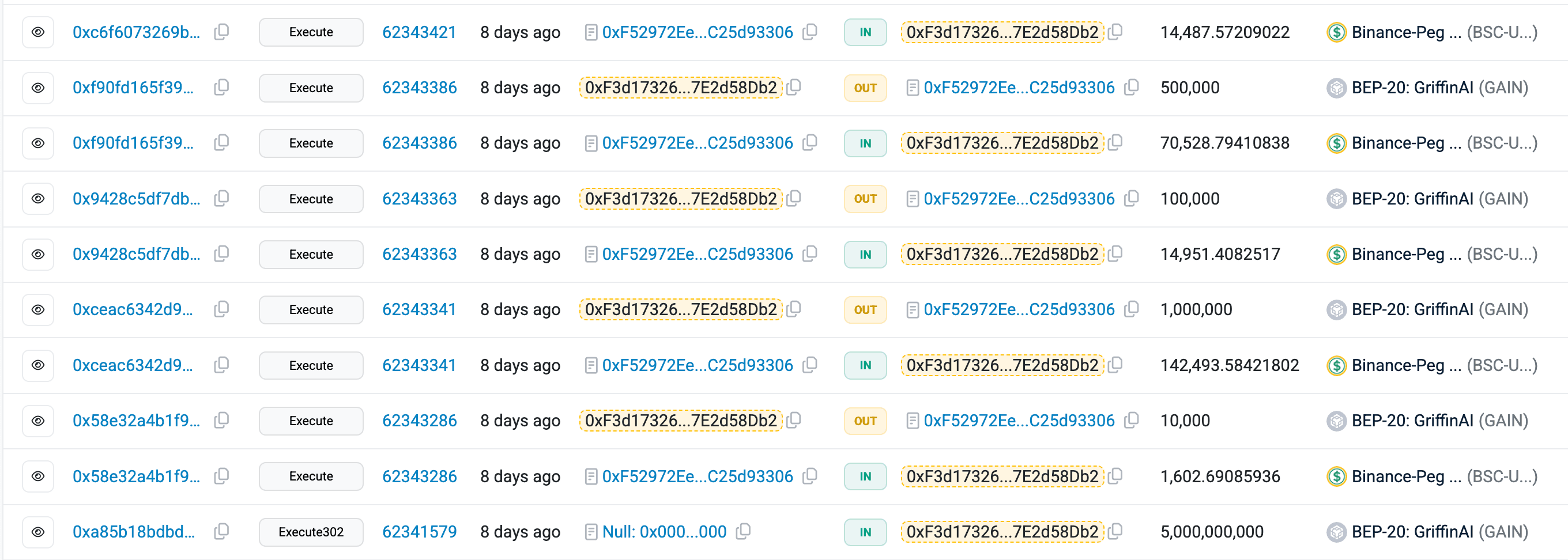
The attacker’s wallet on BNB Chain (0xf3d17326130f90c1900bc0b69323c4c7e2d58db2) currently holds the 800,000,000 excess minted $GAIN tokens. These funds remain in the attacker's control, with no recoveries noted.

Fortify Your Protocol Against Admin Key Exploits
Fortify Your Protocol Against Admin Key Exploits
The Griffin AI hack shows how a single compromised admin wallet can trigger millions in losses. Don’t wait for a breach! Secure your cross-chain protocols with QuillAudits.
Post Attack Mitigation
Following the exploit, the GriffinAI team, led by CEO Oliver Feldmeier, took decisive steps to address the breach and restore community trust. The key actions include:
The team secured the compromised cross-chain connection to prevent further unauthorized minting. They notified all exchanges to halt $GAIN deposits, withdrawals, and trading, and shut down the PancakeSwap liquidity pool to limit further damage.
The team announced a migration to a new, fully audited $GAIN token. A snapshot of pre-hack token balances will be used to restore all legitimate holders balances on a 1:1 basis, ensuring no community member is left behind.
To support long-term token value and reduce circulating supply, CEO Oliver Feldmeier committed to personally funding a $500,000 USDT buyback of $GAIN over three months. Additionally, GriffinAI will execute a $2 million USDT buyback over the next 12 months. All repurchased tokens will be permanently burned to create deflationary pressure.
The team reported the incident to law enforcement to pursue the attacker and potentially recover the stolen funds, though no recoveries have been reported as of now.
Relevant Address and Transactions
- Set Peer Transaction: 0xf867a8e0b73cc279075cc760747b2a6a552bfa4623ad302f78d5516cb3062d88
- Minting Transaction: 0xa85b18bdbd32fbe5468de38032f7f2717faaad663d33991b2c71ce0b3892e866
- Dumping Transactions:
- 0xcfaf94a7d7e4b56bf0698f2cba88e46c2cc1c584a897e65f1a63ac88de290045
- 0x31661ffc5311cd13bf59cb3a5122198c2ce4d4420d221bedfba634fdda49fc58
- 0x22afbc0ecb066e7247a68919082d9bc1b3f59cb02582ee113f2d570cb446ea57
- 0x9be63ee5b0175328403ea0b9ecd55b676e528ee43beba065e83b0d25bc1fae2c
- 0x3a175487668f521e4aedf86aa2d96f059b50f08520c31c164fb16265fe2f8e0b
- 0x16fbdad32ad3f875918604a8f27edd1a22e0e23c6845a6d5b4e0a41741f2d5f2
- 0x9638338190ad3b068533d58398a68e7126c46503f357a59e1ef0defb713d05ea
- Key Addresses:
- Compromised Admin (BSC): 0x54a978238984d581edd3a9359dda9be53a930a7e
- Decoy Contract (ETH): 0x7a8caffeb11047e90affc9f7527103b0334572e6
- Legitimate GAIN Endpoint (ETH): 0xccdbb9c8e43f50407c58f81407a16549e2a475dd
- Legitimate GAIN Endpoint (BSC): 0xAcf5A368eC5bb9e804C8AC0b508dAA5A21C92e13
- Malicious Peer (ETH): 0xba159054636e69080ae7c756319e5c85498efeb0
- Attacker Wallet (BSC): 0xf3d17326130f90c1900bc0b69323c4c7e2d58db2
- Attacker Wallet (ETH): 0xC7494498aC24e0Ab1842Ee12485BbfDb9c9e8294
- Attacker Wallets (ETH):
- 0x1afc80d0e15cbcbfaab9ad5520b4ab843dfd648d (134 ETH)
- 0xd4d83c2bc58b97d6458a7ae7d5b417c5422dc04c (123 ETH)
- 0xb31bddb3d1c2b45e5c5fe149aa4c8304e9d1916c (122 ETH)
- 0xa6654f227eccf2f84476d2d51434081613f8baba (121 ETH)
- 0x107e83ebe677ddec253c440127f23310720177c2 (121 ETH)
- 0xf1755a2b7d0e418e9bab4f81ad674fa39fa7f23d (97 ETH)
- 0x3Bb8c1eA842bDA763b6a717BD2D739d4Bc85A70A (158 ETH)
Conclusion
The GriffinAI exploit serves as a stark reminder of the risks associated with cross-chain bridges like LayerZero, particularly when admin privileges are compromised. Projects must prioritize robust key management, thorough audits, and secure peer configurations to prevent similar incidents. This attack not only caused immediate financial damage but also eroded trust in emerging Web3 AI initiatives, emphasizing the need for enhanced security practices in the DeFi ecosystem.
Contents



