Decoding Azuki DAO Hack
Learn about the details of the Azuki DAO hack and how it affected decentralized finance. Understand what happened during the hack and its consequences.

Summary
On the 30th of June, Azuki DAO suffered an exploit of it’s governance token contract. The attack was made possible by a signature replay vulnerability. And around 17,937,50 BEAN was stolen by the hackers from the exploit.
About Project
Azuki DAO was a group that was formed last week in response to the controversial launch of Azuki Elementals, an NFT project spin-off from the creators of the original Azuki NFT collection. The DAO created a governance token, $BEAN, which was distributed to NFT owners.
To learn more about the Project, check out the official website.
Vulnerability Analysis & Impact
On-Chain Details
Attacker Address:
1. 0x85D231C204B82915c909A05847CCa8557164c75e
2. 0x8Eadc7Cc0a77594e3fA999e80e1cCb7F4e1c04E0
Victim Contract: 0x8189AFBE7b0e81daE735EF027cd31371b3974FeB
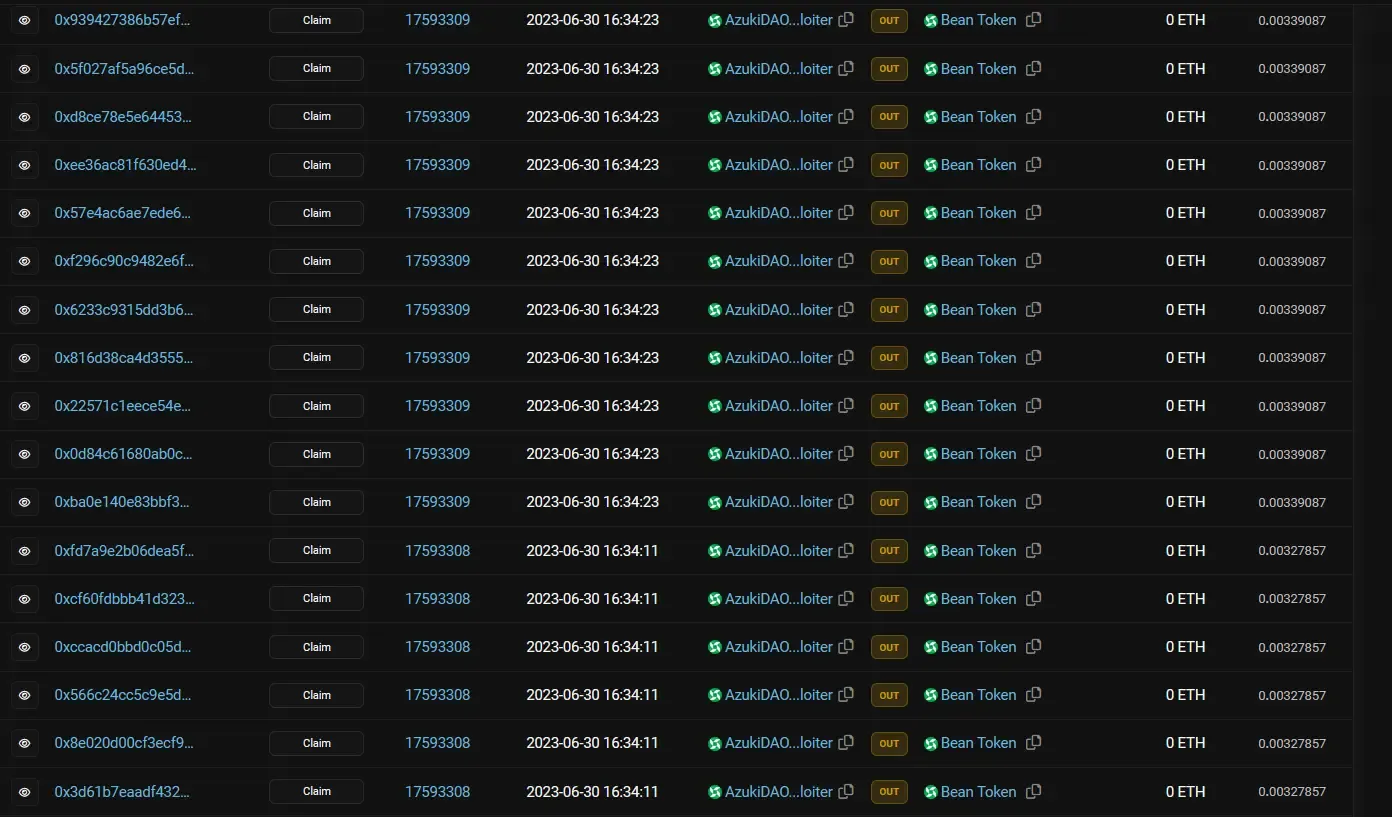
Attack Transactions:
The Root Cause
Upon analysis of BEAN token contract
- There is no check on whether the signature is already claimed or not in the ‘claim’ function.
- Although variable _signature checks if the address is eligible and signatureClaimed[_signature] is set, so user cant claim again.
- But that is never checked anywhere in the function.
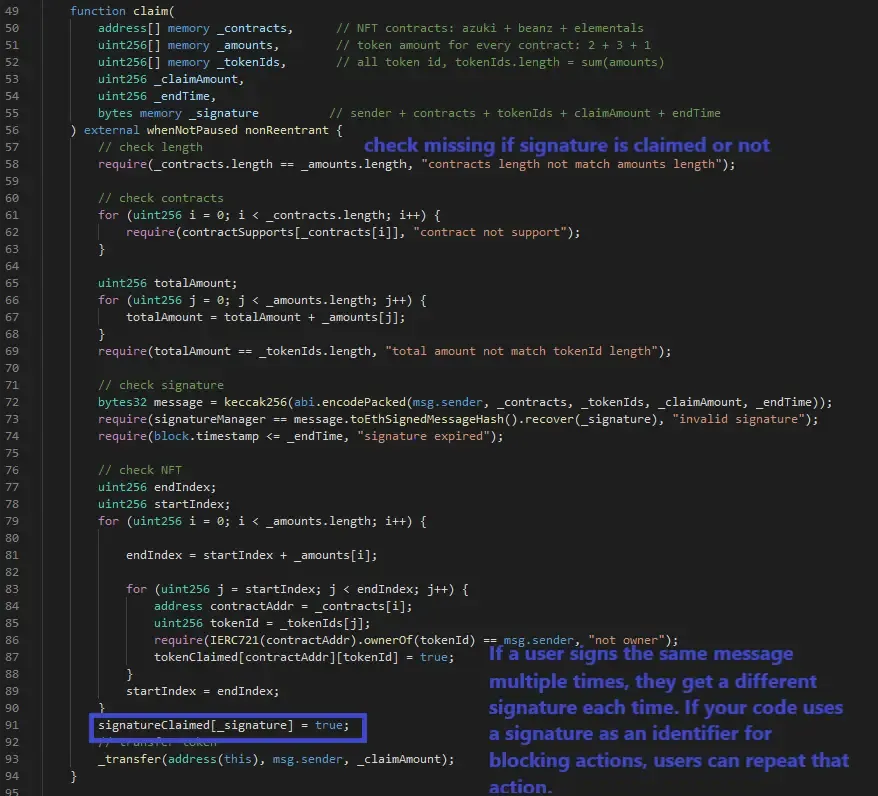
This allowed attacker to repeatedly call the claim function with the same signature across different invocations of the claim function.

Although the attack was carried through a replay attack, the inherent signature malleability of ECDSA signature scheme could also be exploited.
This is because the line signatureClaimed[_signature] is storing signature as a key to hash . An attacker can take one valid signature , and make another valid signature
Attack Process
- The attacker claimed token with the signature – 0xb0c7a8994624f4187fa28019f1ed169887d814cc72a7c6e5a9afe78a0cc825e55f7fca08df0c2dc16ce05f2a39bc15949d6bb07c5283cf9e131ae51251e719e61b
- The same signature was used to repeatedly claim BEAN tokens until 1.79 Million Tokens were claimed
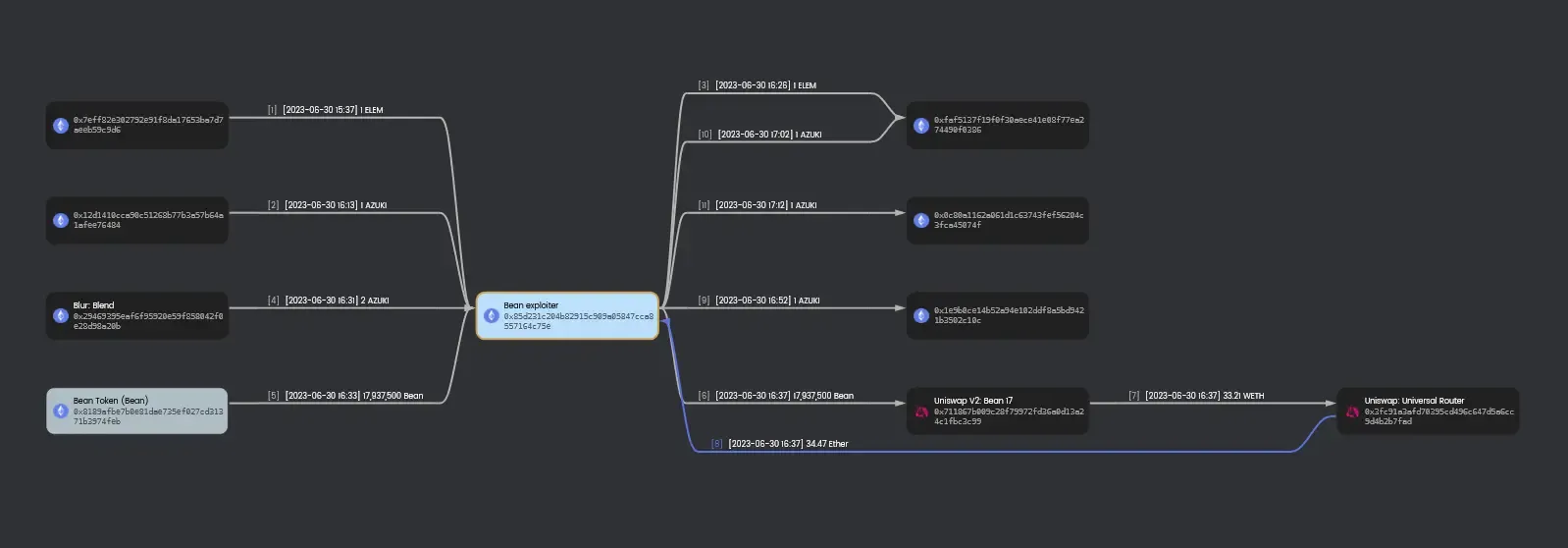
Flow of Funds
The attacker 0x85d231c204b82915c909a05847cca8557164c75e has made a profit of 34.47ETH
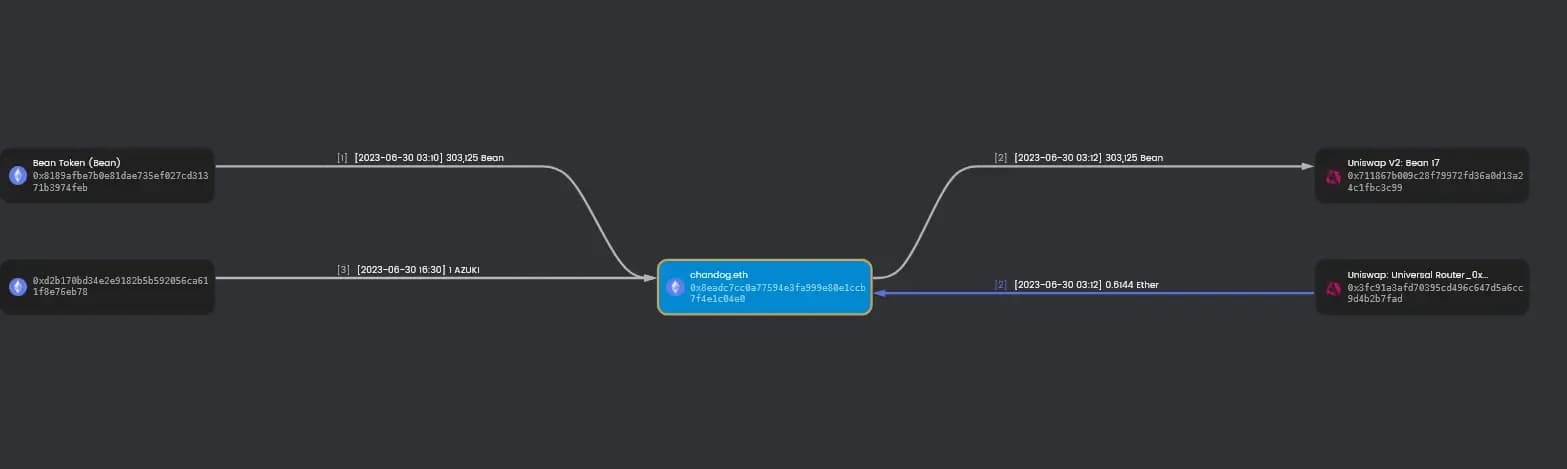
The attacker 0x8Eadc7Cc0a77594e3fA999e80e1cCb7F4e1c04E0 has made a profit of 0.614ETH
After the Exploit
Incident Timelines
June 30th, 2023, at 3:54:47 PM +UTC, the attacker claimed 6,250 BEANZ tokens. The series of transactions lasted around 3:56:23 PM +UTC.
June 30th, 2023, at 4:15 PM UTC, the attacker claimed 31,250 Bean tokens from contract. The series of transactions lasted around 4:34 PM UTC.
July 4th, 2023 – MetaSleuth informed about the attack via Twitter.
How could they have prevented the exploit?
The Exploit could have been prevented if a like this was placed at the start of the claim, function
require(!signatureClaimed[_signature], “Not Authorized”);
A simple solution would be to modify the “claimed” mapping to be based on the user’s address instead of using the signature as the key. This way, each user would only be able to receive tokens once.
Why QuillAudits For Web3 Security?
- QuillAudits is well-equipped with tools and expertise to provide cybersecurity solutions saving the loss of hundreds of protocols in funds.
- Our team of highly skilled auditors have secured over 1M lines of code and $3B in amount.
- Over the course of multiple years, QuillAudits has been proven to be one of the top choices for protocols to get their codebases audited.
Partner with QuillAudits
- OG Program (Opportunities for Listing Managers, KOLs, Top Advisors and Investors with access to early stage Web3 projects)
- QuillAudits Partnership Programme (Venture funds, launchpads, development companies, marketing firms, web2 cybersecurity firms, web3 products)
- WAGSI Program(Claim audit credits to avail exclusive discounts on our auditing package, and additional credits for our automated web3 security infra- QuillShield)
Contents



