Breaking Down CloberDEX’s Costly $501K Exploit
Discover how a reentrancy flaw in CloberDEX's Rebalancer contract led to a $501k exploit. Learn the root cause, attack process, and prevention measures.

Overview:
The CloberDEX Liquidity Vault was exploited on December 10, 2024, through a reentrancy vulnerability in the _burnfunction of the Rebalancer contract on the Base network. The attacker leveraged a custom malicious strategy that exploited the absence of a reentrancy check, resulting in a loss of approximately 133.7 ETH (~$501,279). The vulnerability arose because the _burn function executed token transfers before updating critical state variables, violating the checks-effects-interactions pattern. By exploiting unmodified reserve values during reentrancy, the attacker manipulated withdrawal calculations to extract more tokens repeatedly.
About Project
Clober is a fully on-chain CLOB DEX protocol for Ethereum and its L2s. Clober presents a new algorithm for order book DEX “LOBSTER - Limit Order Book with Segment Tree for Efficient oRder-matching” that enables on-chain order matching and settlement on decentralized smart contract platforms. With Clober, market participants can place limit and market orders in a fully decentralized, trustless way at a manageable cost.
Exploit Details:
Attacker Address : 0x012Fc6377F1c5CCF6e29967Bce52e3629AaA6025
Vulnerable Contract : 0x6A0b87D6b74F7D5C92722F6a11714DBeDa9F3895
Attack Transaction : 0x8fcdfcded
Attacker Contract Address : 0x32Fb1BedD95BF78ca2c6943aE5AEaEAAFc0d97C1
Malicious Token Contract: 0xd3c8d0cd07Ade92df2d88752D36b80498cA12788
Attack Process:
Initially, the attacker took a flash loan of 267 WETH from the Morpho Blue.

- The attacker deployed a malicious token contract and created a liquidity pool using the CloberDEX
openfunction. The pool paired WETH with the attacker's custom token, and the attacker set the pool's strategy to point to their attack contract.

The _burn function in the vault’s Rebalancer contract was designed to call an external burnHook function. However, the _burn function lacked reentrancy protection, making it vulnerable to repeated calls.

- Within the
_burnfunction, token transfers are were executed before the state variablespool.reserveAandpool.reserveBwere updated. - This sequence allowed the attacker to exploit the unchanged reserve values to miscalculate withdrawal amounts.
- During the first execution of the
_burnfunction, the attacker's customburnHookfunction reentered the_burnfunction again before the reserves were updated. This reentrancy enabled the attacker to inflate the withdrawal amounts during the second
_burnexecution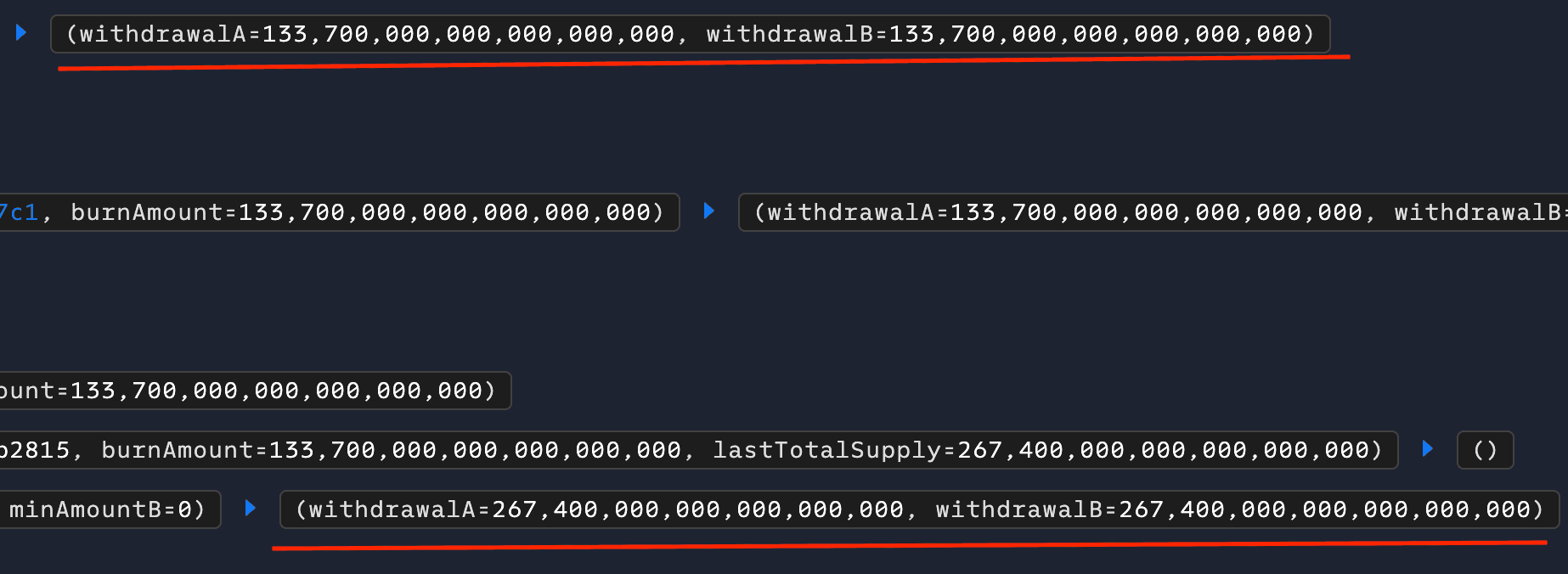
- By repeating this process in a single transaction, the attacker siphoned off significantly more tokens than they were entitled to, resulting in the loss of 133.7 ETH.
The Root Cause
The root cause of the CloberDEX Liquidity Vault exploit was the improper handling of external calls in the _burnfunction. Specifically, the _burn function executed token transfers to users before updating critical state variables like pool.reserveA and pool.reserveB. This sequence violated the checks-effects-interactions pattern, leaving the contract vulnerable to reentrancy attacks.
Flow of Funds
See the funds flow here:

Post Exploit Scenes
CloberDEX responded to the attack and offered the attacker 20% of the stolen funds if the remaining assets are returned.
How could they have prevented the Exploit?
- Adding a reentrancy guard, such as OpenZeppelin’s
ReentrancyGuardmodifier, would have ensured that the_burnfunction could not be called recursively within the same transaction. - The
_burnfunction should update state variables (e.g.,pool.reserveAandpool.reserveB) before making external calls like token transfers. This ensures that critical state data is modified before any potential reentrant code execution. - Collaborate with reputable auditors like QuillAudits to analyze smart contracts and identify vulnerabilities.
Why QuillAudits?
Choosing a reputable audit firm like QuillAudits ensures that your protocol undergoes rigorous scrutiny from experienced security professionals. QuillAudits specializes in uncovering critical vulnerabilities and providing actionable remediation strategies. Our expertise helps safeguard your project from attacks, ensuring that security issues are addressed proactively.
Contents




