Yearn's $9M Invariant Solver Exploit (Explained)
Learn how Yearn lost $9M in an invariant solver exploit, with a clear explanation of the bug, attacker method & defensive takeaways for DeFi security.

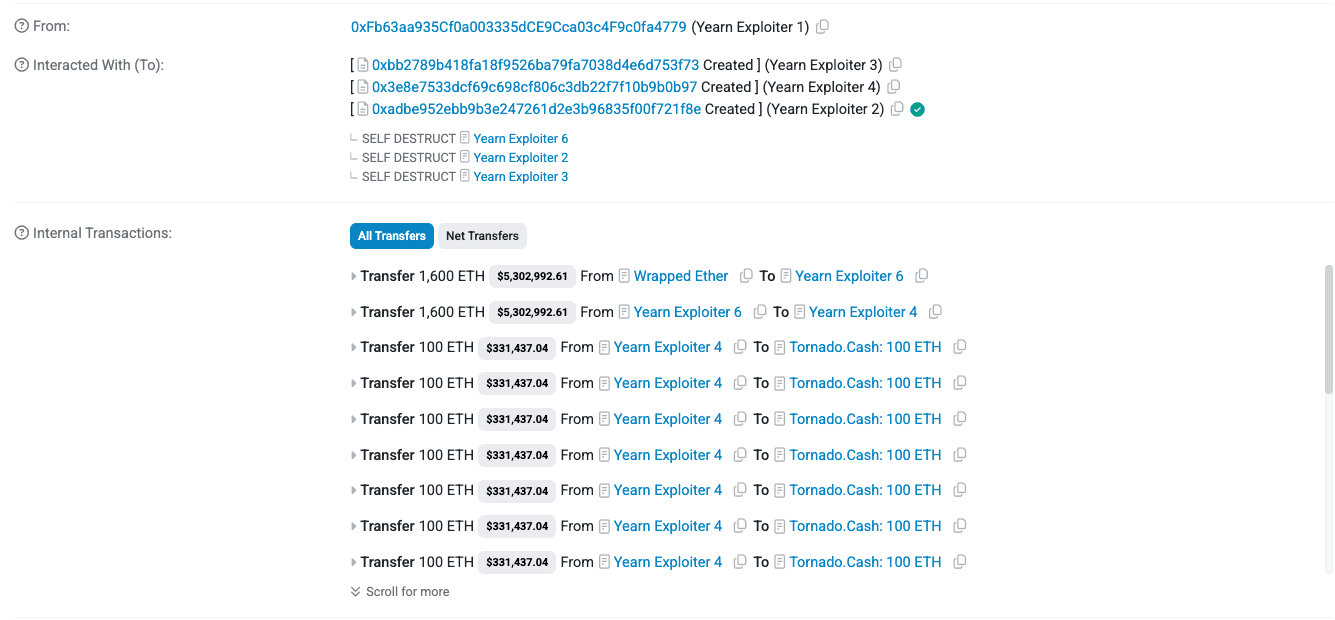
On November 30, 2025, the yETH weighted stableswap pool, an autonomous LST aggregator supporting assets such as apxETH, sfrxETH, and wstETH, was exploited. The attacker manipulated the pool’s iterative fixed-point solver, resulting in excess yETH LP token minting, invariant breakdown, and an arithmetic underflow. Roughly $9 million in LSTs and WETH were drained.
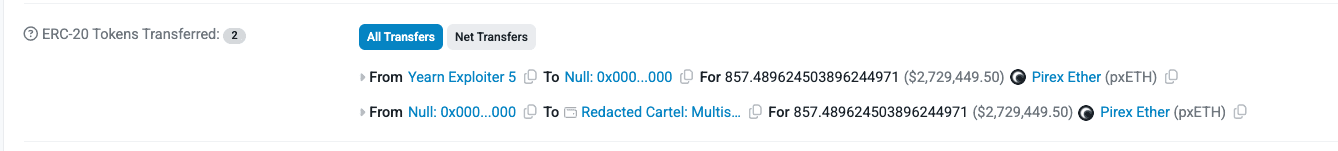
The impact was limited to the yETH ecosystem and its Curve integration, with Yearn’s v2/v3 vaults and other products remaining unaffected. Yearn immediately activated a war room and successfully recovered 857.49 pxETH (~$2.33 million), while the remaining funds were funneled through Tornado Cash.
Hack Analysis
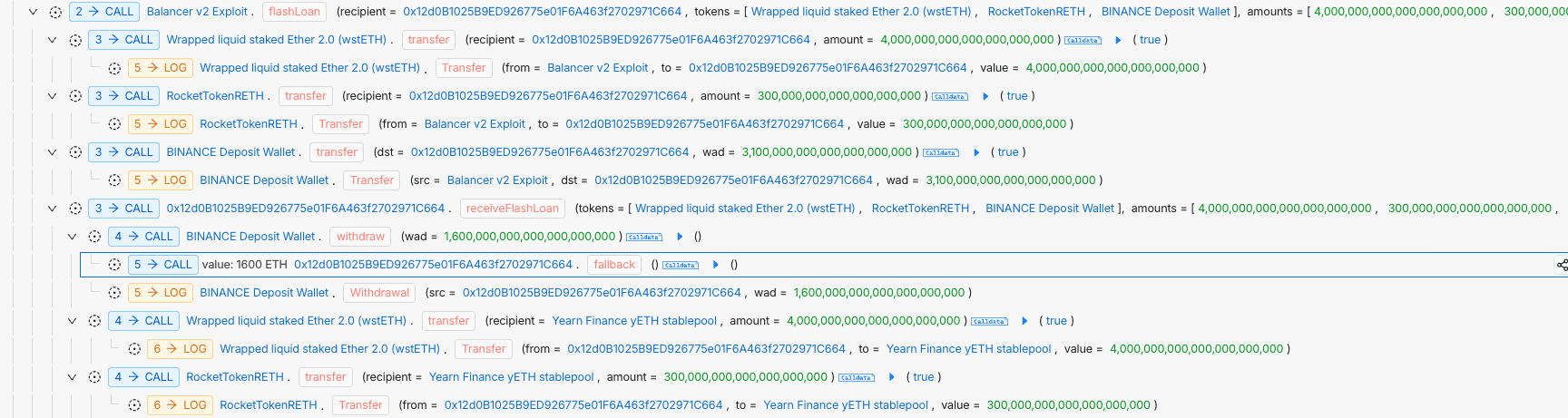
The attacker executed the exploit in a single transaction at block 23,914,086, orchestrating a three-stage sequence that manipulated the pool’s invariant, drained its liquidity, and ultimately abused the bootstrap initialization path to mint an astronomically large amount of yETH.
The attack began with a series of highly imbalanced add_liquidity calls. By depositing extreme quantities of LSTs relative to the pool’s existing balances, the attacker forced the custom stableswap invariant into unstable territory. The Newton–Raphson solver, receiving distorted inputs, began producing inconsistent supply values that allowed the attacker to mint far more LP tokens than should have been possible.
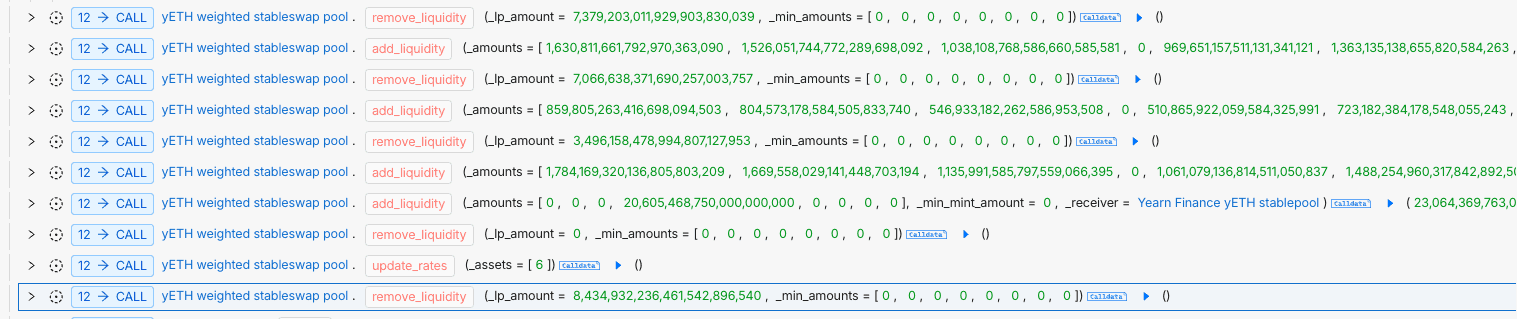
With over-minted LP tokens secured, the attacker moved into a controlled withdrawal phase. Repeated calls to remove_liquidity(0) recomputed Π from actual balances, temporarily restoring the pool to a superficially valid state without correcting the inflated internal supply D. Leveraging this mismatch, the attacker performed a series of single-asset withdrawals, systematically draining the pool’s LST holdings across multiple assets.
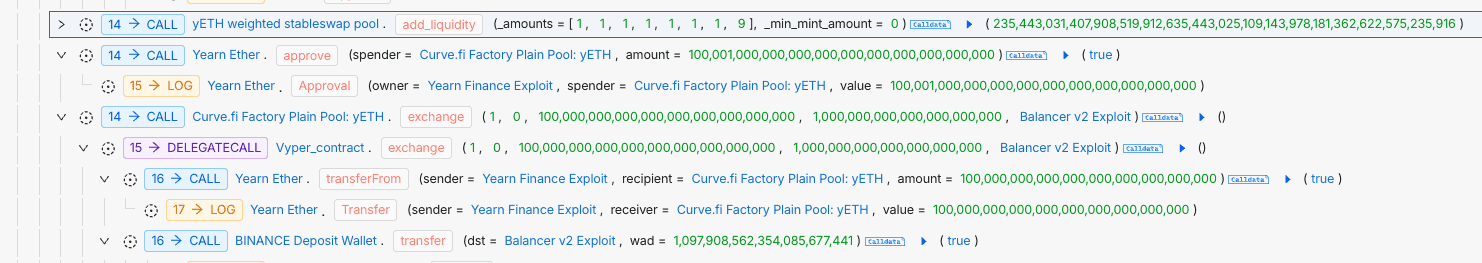
After the pool’s reserves were nearly exhausted and the previous supply had dropped to zero, the attacker triggered the contract’s bootstrap initialization logic using only dust-level deposits. This pathway, intended solely for deployment, became reachable due to the drained state. During supply calculation, an underflow occurred, causing the solver to wrap a negative value into a massive positive number, minting over 2.3 × 10⁵⁶ yETH. These counterfeit tokens were immediately swapped in the yETH/WETH Curve pool for roughly 298 WETH before being laundered.
Root Cause
The exploit originated from a combination of unresolved numerical weaknesses and architectural oversights in the legacy yETH implementation. Extreme imbalance during deposits caused the solver’s pow_up path to produce extremely small vb_prod values, leading the Newton iteration to diverge and truncate π to zero without enforcing the required domain condition A⋅σ ≥ D⋅π. This broke the invariant, and asymmetric handling of π, incremental updates during add_liquidity versus full recomputation during remove_liquidity(0) , allowed the attacker to restore a valid π while keeping an inflated D. The separation between internal supply D and the ERC-20 supply enabled the pool to reach a prev_supply == 0 state despite POL still existing, unintentionally reopening the initialization path. Because the bootstrap logic was never permanently gated after deployment, the attacker could re-enter it under adversarial conditions, where unsafe arithmetic such as unsafe_sub converted domain violations into underflows, enabling effectively infinite mints instead of reverting. Collectively, these flaws in an unmaintained, self-governed pool underscore the inherent risks of high-amplification LST AMMs that lack strict numerical bounds, domain checks, and lifecycle gating.
Don’t Let Hidden Math Bugs Put Your Protocol at Risk
Don’t Let Hidden Math Bugs Put Your Protocol at Risk
Invariant violations, underflows and mis-gated initialization paths shouldn’t ever reach mainnet. Our auditors identify these risks long before attackers do.
Funds Flow Post Attack
Most of the stolen funds were laundered through Tornado Cash.
Meanwhile, the recovery process resulted in 857.49 pxETH (~$2.39M) being retrieved through collaboration with the Plume and Dinero teams.
Post Attack Mitigation
The incident was immediately acknowledged, a war room was assembled to respond, and users were assured that Yearn v2/v3 were not affected.
On December 6th, the Yearn team released a full post-mortem report.
On December 6th, the Yearn team released a full post-mortem report.
Relevant Transactions and Addresses
- Attack Transaction: 0x53fe7ef190c34d810c50fb66f0fc65a1ceedc10309cf4b4013d64042a0331156
- Attacker EOA: 0xa80D3F2022F6Bfd0B260bF16D72CaD025440C822
- Attack Contract: 0xB8e0A4758Df2954063Ca4ba3d094f2d6EdA9B993
- yETH Weighted Stableswap Pool: 0xCcd04073f4BdC4510927ea9Ba350875C3c65BF81
- yETH/WETH Curve Pool: 0x69accb968b19a53790f43e57558f5e443a91af22
- pxETH Recovery: 0x0e83bb95bb9d05fb81213b2fad11c01ea671796752e8770b09935f7052691c35
Conclusion
The yETH exploit highlights how fragile DeFi becomes when fixed-point math, protocol-owned liquidity mechanics, and rollout gaps collide. A minor truncation issue cascaded into a $9 million drain. Yearn’s rapid response, detailed forensics, 26% fund recovery, and targeted fixes, including domain checks, safe-math enforcement, and expanded fuzzing, kept the incident isolated to a single product.
As LST pools continue to scale, the takeaway is clear, invariants need live enforcement, solvers must respect bounded domains, and bootstrap phases require airtight controls. In the EVM’s integer-bound environment, silent divergence isn’t a bug, it’s a systemic threat. More assets may still be traced and recovered, but the real victory lies in engineering architectures that fail fast instead of collapsing quietly. Preventing incidents like this in the future ultimately depends on prioritizing thorough security audit processes across every protocol layer.
Contents



