Tokenized Real World Assets (RWAs) need compliance features that work smoothly with existing DeFi standards. Older approaches made developers handle too many rigid requirements like identity registries, metadata formats, and custom enforcement modules. ERC-7943, called the Universal RWA (uRWA) Interface, fixes this with a clean, minimal design. It provides three interfaces (for fungible, non-fungible, and multi-token assets) that plug directly into ERC-20, ERC-721, and ERC-1155 flows. These interfaces use simple view functions to check if a transfer is allowed, functions to freeze or enforce rules, and ERC-165 for compatibility checks. This post explains the ABI, how the hooks work, tricky edge cases, and what auditors should look out for, helping smart contract developers and security researchers understand and build secure uRWA contracts.
What is ERC-7943 & What Problems Does It Solve?
ERC-7943 formalizes a compliance-minimal interface suite for RWA tokens, extending base ERCs with hooks for regulatory enforcement. canTransact for account gating, canTransfer for pre-flight validations, getFrozenTokens for balance introspection, setFrozenTokens for administrative freezes, and forcedTransfer for unilateral seizures. Unlike monolithic standards, uRWA enforces no on-chain identity or metadata, implementers supply the logic (e.g., Chainlink oracles for KYC, Merkle proofs for allowlists) while exposing uniform ABIs.
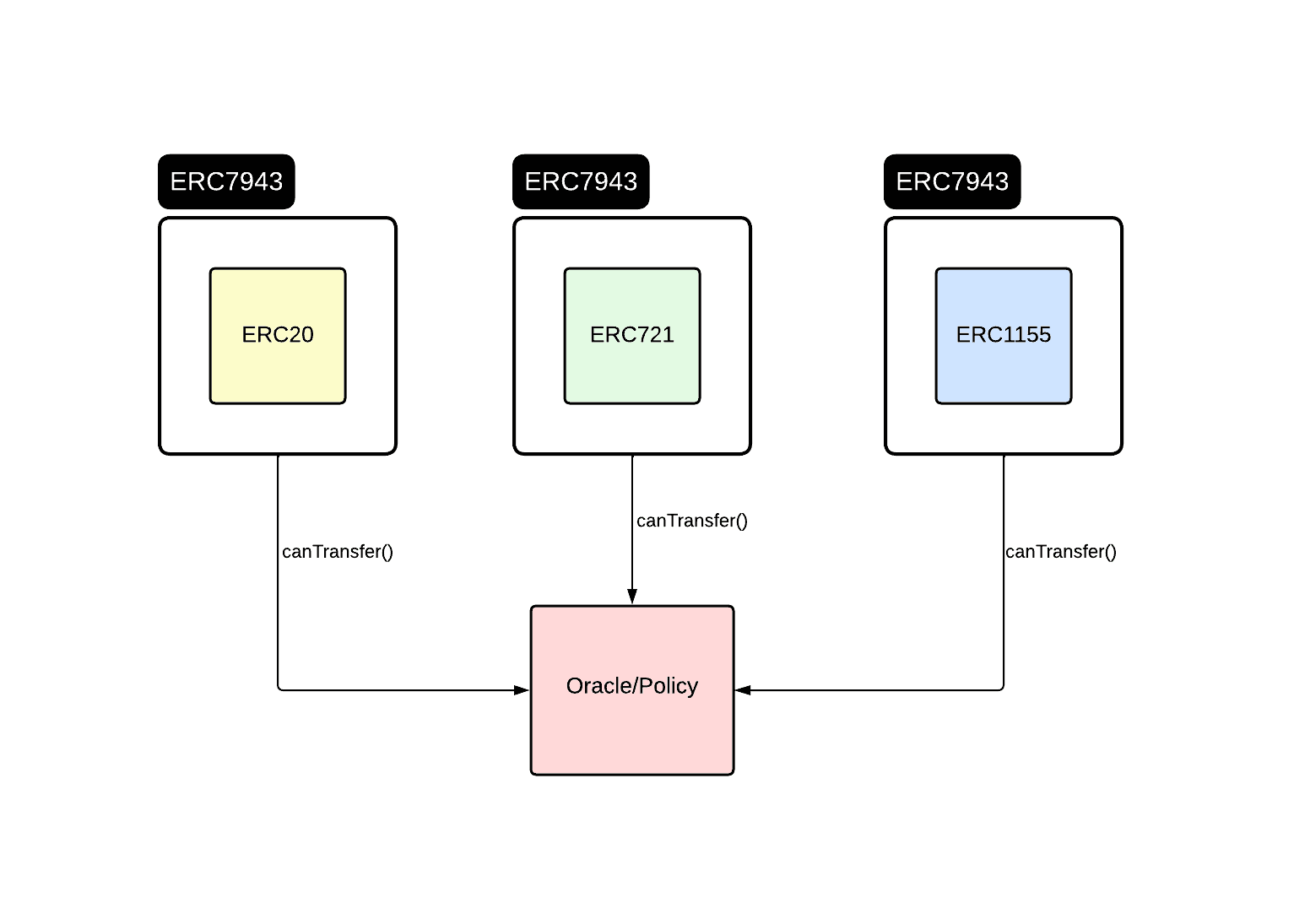
Core problems resolved:
- Regulatory Polymorphism: uRWA abstracts jurisdiction-specific rules (e.g., SEC Reg S exemptions, EU MiCA transfer caps) into pluggable view functions, enabling cross-chain routers to query without asset-type awareness.
- Transfer Integrity: Intercepts
_beforeTokenTransferto revert on frozen excesses or ineligible parties, preventing AML violations at the protocol layer.
- Enforcement Primitives:
forcedTransferenables custodians to execute court-mandated reallocations without proxy upgrades, returningboolfor idempotency.
- Gas-Optimized Modularity: Pure/view functions minimize on-chain compute, off-chain indexers cache
Frozenevents for sub-second queries.
- Composability Barriers: ERC-165 selectors (e.g.,
0x...forIERC7943Fungible) allow DeFi aggregators to dispatch to the correct variant dynamically.
uRWA’s philosophy is to require only the necessary compliance touchpoints, not the full implementation depth, resulting in roughly 5–10k gas per canTransfer call instead of the 50k-plus costs of older modular systems.
How ERC-7943 Improves Existing EIPs for RWAs
ERC-7943 sharpens the RWA token space by prioritizing clean ABIs, universal variants, and flexible implementations instead of heavy modular systems or rigid frameworks, addressing gaps in ERC-1400 (securities-focused partitioning), ERC-1404 (basic restrictions without deep enforcement), ERC-3643 (registry-bound modularity), and ERC-7518 (partitioned multi-asset with dynamic vouchers) by removing excess complexity while strengthening core primitives, followed by a feature-by-feature breakdown of the improvements:
| Feature | Problems in Existing EIPs | How ERC-7943 Improves It |
|---|---|---|
| Core Interfaces | ERC-1400/1404 use rigid, securities-style hooks, ERC-3643 forces registry-based compliance, ERC-7518 stores heavy TokenPartition metadata. | Three lightweight variants (Fungible, NonFungible, MultiToken) using hook-only logic, no modules, no partitions, ~30% less storage vs. ERC-7518. |
| Compliance Hooks | ERC-1400 uses partition checks, ERC-1404 only provides a basic restriction flag, ERC-3643 depends on identity lookups; ERC-7518 requires EIP-712 voucher signatures. | Simple canTransact / canTransfer bool checks, no identity requirements, no signatures, supports off-chain or proof-based rules with ~70% gas savings. |
| Freeze Logic | ERC-1400/1404 use implicit lists, ERC-3643 depends on modules, ERC-7518 freezes entire addresses or partitions, causing unnecessary lockups. | Clear Frozen events + per-token freeze mapping, O(1) lookups, supports over-balance freezes for preemptive actions. |
| Forced Transfers | ERC-1404 is basic, ERC-1400/3643 are tied to partitions/modules, ERC-7518 risks cross-tranche mistakes. | Unified forcedTransfer that bypasses hooks safely and returns a bool for relayers, no partition pitfalls. |
| Gas Costs | ERC-1400: ~100k gas; ERC-3643: 30–80k, ERC-7518: 40–90k due to signature recovery and partition reads. | ~5k gas per check using pure/view, ideal for high-throughput DeFi and cheaper than all prior RWA standards. |
| Extensibility | ERC-1400/1404 are hard to extend, ERC-3643 is flexible but registry-bound, ERC-7518 relies on oracles and is vulnerable to batch DoS. | Maximum flexibility, devs define logic (even ZK checks), compliance stays separate, works smoothly with systems like EIP-2535. |
| Introspection | Limited ERC-165 support, many standards focus only on fungibles, ERC-7518 metadata adds bloat. | Full ERC-165 for all variants, cleaner and lighter than ERC-7518. |
| Cross-Chain Use | Weak native support, ERC-7518’s wrapper can break atomicity and enable replays. | Uniform hooks propagate cleanly through CCIP/LayerZero, bool returns simplify idempotent cross-chain relays. |
| Motivation | Older standards are too prescriptive, expensive, and tied to securities workflows, ERC-7518 introduces partition risks and high gas overhead. | Minimal, general-purpose design without identity bloat, cuts deployment gas by 50%+ and fits real estate, commodities, bonds, and simple RWAs. |
By distilling to essential hooks, uRWA lowers barriers for RWA issuers (e.g., Centrifuge pools) while supercharging DeFi integrations query once, enforce everywhere.
How ERC-7943 Works?
ERC-7943 (uRWA) adds compliance checks directly into the standard token flow by tapping into the usual lifecycle hooks. A simplified flow for a fungible token transfer looks like this:
Eligibility Check
The caller triggers
transfer(to, amount)→_beforeTokenTransfer(...), which verifies:require(canTransact(from) && canTransact(to), ERC7943CannotTransact(account)).
Freeze Check
Calculate
unfrozen = balanceOf(from) - getFrozenTokens(from)and ensure the sender has enough unblocked tokens:require(unfrozen >= amount, ERC7943InsufficientUnfrozenBalance(...)).
Policy Check
Validate transfer rules via:
require(canTransfer(from, to, amount), ERC7943CannotTransfer(...)), which can combine allowlists, blocklists, velocity limits, or oracle-driven rules.
Execution
If all checks pass,
_transferexecutes; otherwise, the transaction reverts with compact errors (saving ~200 gas compared to string errors).
For non-fungible tokens, amount is replaced with tokenIdand freezes become boolean statuses. For multi-token setups, both parameters are included.
Administrative Mutations
Write operations require elevated permissions (e.g., onlyOwner, hasRole):
setFrozenTokens(account, amount)Replaces the previous freeze level and emitsFrozen(account, amount). The freeze amount may exceed the current balance to support preemptive locks.
forcedTransfer(from, to, amount)Skips all hooks and approvals, performs a direct transfer, and emitsForcedTransfer, and returnstrueon success for safe relayer retries.
ERC-165 Integration
Implementations expose their variant with: supportsInterface(type(IERC7943Fungible).interfaceId), allowing routers and aggregators to detect and route calls polymorphically.
Working Diagrams
Fungible Transfer Flow
Forced Transfer Flow (Admin Path)
Implementation with Code Blocks
Match your implementation to the spec’s ABIs. Below are the three interfaces and a sample ERC-20 extension using OpenZeppelin v5.x.
Core Interfaces (From Spec)
IERC7943Fungible
1/// @notice Interface for ERC-20 based implementations.
2interface IERC7943Fungible is IERC165 {
3 event ForcedTransfer(address indexed from, address indexed to, uint256 amount);
4 event Frozen(address indexed account, uint256 amount);
5
6 error ERC7943CannotTransact(address account);
7 error ERC7943CannotTransfer(address from, address to, uint256 amount);
8 error ERC7943InsufficientUnfrozenBalance(address account, uint256 amount, uint256 unfrozen);
9
10 function forcedTransfer(address from, address to, uint256 amount) external returns(bool result);
11 function setFrozenTokens(address account, uint256 amount) external returns(bool result);
12 function canTransact(address account) external view returns (bool allowed);
13 function getFrozenTokens(address account) external view returns (uint256 amount);
14 function canTransfer(address from, address to, uint256 amount) external view returns (bool allowed);
15}IERC7943NonFungible
1/// @notice Interface for ERC-721 based implementations.
2interface IERC7943NonFungible is IERC165 {
3 event ForcedTransfer(address indexed from, address indexed to, uint256 indexed tokenId);
4 event Frozen(address indexed account, uint256 indexed tokenId, bool indexed frozenStatus);
5
6 error ERC7943CannotTransact(address account);
7 error ERC7943CannotTransfer(address from, address to, uint256 tokenId);
8 error ERC7943InsufficientUnfrozenBalance(address account, uint256 tokenId);
9
10 function forcedTransfer(address from, address to, uint256 tokenId) external returns(bool result);
11 function setFrozenTokens(address account, uint256 tokenId, bool frozenStatus) external returns(bool result);
12 function canTransact(address account) external view returns (bool allowed);
13 function getFrozenTokens(address account, uint256 tokenId) external view returns (bool frozenStatus);
14 function canTransfer(address from, address to, uint256 tokenId) external view returns (bool allowed);
15}IERC7943MultiToken
1/// @notice Interface for ERC-1155 based implementations.
2interface IERC7943MultiToken is IERC165 {
3 event ForcedTransfer(address indexed from, address indexed to, uint256 indexed tokenId, uint256 amount);
4 event Frozen(address indexed account, uint256 indexed tokenId, uint256 amount);
5
6 error ERC7943CannotTransact(address account);
7 error ERC7943CannotTransfer(address from, address to, uint256 tokenId, uint256 amount);
8 error ERC7943InsufficientUnfrozenBalance(address account, uint256 tokenId, uint256 amount, uint256 unfrozen);
9
10 function forcedTransfer(address from, address to, uint256 tokenId, uint256 amount) external returns(bool result);
11 function setFrozenTokens(address account, uint256 tokenId, uint256 amount) external returns(bool result);
12 function canTransact(address account) external view returns (bool allowed);
13 function getFrozenTokens(address account, uint256 tokenId) external view returns (uint256 amount);
14 function canTransfer(address from, address to, uint256 tokenId, uint256 amount) external view returns (bool allowed);
15}Reference Implementation: Fungible uRWA Token
A lightweight extension that uses a Merkle-root allowlist and an oracle hook. For NFTs, adapt it to ERC-721 using mapping(address => mapping(uint256 => bool)) _frozenTokens. For multi-token setups, rely on ERC-1155’s balanceOf and per-ID freeze tracking.
1// NOTE: NOT RECOMMENDED TO BE USED IN PRODUCTION
2
3// SPDX-License-Identifier: MIT
4pragma solidity ^0.8.20;
5
6import {ERC20} from "@openzeppelin/contracts/token/ERC20/ERC20.sol";
7import {Ownable} from "@openzeppelin/contracts/access/Ownable.sol";
8import {MerkleProof} from "@openzeppelin/contracts/utils/cryptography/MerkleProof.sol";
9import {IERC7943Fungible} from "./interfaces/IERC7943Fungible.sol";
10
11contract URWAToken is ERC20, Ownable, IERC7943Fungible {
12 bytes32 public immutable ALLOWLIST_ROOT; // Merkle root for off-chain updates
13 mapping(address => uint256) private _frozenBalances;
14 mapping(address => bool) private _blacklisted; // Blocklist for sanctions
15 IComplianceOracle public oracle; // Stub: External KYC feed
16
17 constructor(
18 string memory name,
19 string memory symbol,
20 bytes32 allowlistRoot,
21 address complianceOracle
22 ) ERC20(name, symbol) Ownable(msg.sender) {
23 ALLOWLIST_ROOT = allowlistRoot;
24 oracle = IComplianceOracle(complianceOracle);
25 }
26
27 function canTransact(address account) public view override returns (bool) {
28 if (_blacklisted[account]) return false;
29 // Stub: Verify Merkle proof (in prod: pass proof from caller)
30 bool inAllowlist = MerkleProof.verify(bytes32[](0), ALLOWLIST_ROOT, keccak256(abi.encodePacked(account)));
31 if (!inAllowlist) return false;
32 try oracle.isCompliant(account) returns (bool compliant) { return compliant; } catch { return false; }
33 }
34
35 function canTransfer(address from, address to, uint256 amount) public view override returns (bool) {
36 if (!canTransact(from) || !canTransact(to)) return false;
37 uint256 unfrozen = balanceOf(from) - _frozenBalances[from];
38 if (unfrozen < amount) return false;
39 // Additional policy: e.g., daily limit via oracle
40 try oracle.transferAllowed(from, to, amount) returns (bool allowed) { return allowed; } catch { return false; }
41 }
42
43 function getFrozenTokens(address account) public view override returns (uint256) {
44 return _frozenBalances[account];
45 }
46
47 function setFrozenTokens(address account, uint256 amount) external override onlyOwner returns (bool) {
48 _frozenBalances[account] = amount;
49 emit Frozen(account, amount);
50 return true;
51 }
52
53 function forcedTransfer(address from, address to, uint256 amount) external override onlyOwner returns (bool) {
54 if (amount == 0 || balanceOf(from) < amount) return false;
55 _transfer(from, to, amount);
56 emit ForcedTransfer(from, to, amount);
57 return true;
58 }
59
60 function _beforeTokenTransfer(address from, address to, uint256 amount) internal override {
61 super._beforeTokenTransfer(from, to, amount);
62 if (from != address(0) && to != address(0)) { // Skip mint/burn
63 require(canTransfer(from, to, amount), "ERC7943: cannot transfer");
64 }
65 }
66
67 function blacklist(address account, bool status) external onlyOwner {
68 _blacklisted[account] = status;
69 }
70
71 function supportsInterface(bytes4 interfaceId) public view override(ERC20, IERC165) returns (bool) {
72 return super.supportsInterface(interfaceId) || (interfaceId == type(IERC7943Fungible).interfaceId);
73 }
74}
75
76interface IComplianceOracle {
77 function isCompliant(address account) external view returns (bool);
78 function transferAllowed(address from, address to, uint256 amount) external view returns (bool);
79}Build Secure & Compliant RWA Tokens with QuillAudits
Build Secure & Compliant RWA Tokens with QuillAudits
Ensure your ERC-7943 uRWA contracts meet compliance, freeze logic and transfer-rule requirements. Get them audited to prevent costly vulnerabilities.
Security Considerations
The minimal nature of ERC-7943 shifts most security responsibility to the implementer. The following are the key risks to consider in real-world uRWA deployments:
- Admin Power Abuse:
forcedTransferand freeze functions introduce a centralized control surface. Compromised or mismanaged admin keys can seize or lock assets. Strong multisig governance and role separation are essential.
- Oracle & Off-Chain Dependency Risks: Implementers commonly use oracles, allowlists, or Merkle roots in
canTransactandcanTransfer. Compromised feeds, stale data, or outages can allow unauthorized transactions or block legitimate users.
- Faulty Compliance Logic: Since ERC-7943 does not prescribe rules, bugs in custom logic (missing checks, incorrect freeze math, bypass paths) can break compliance guarantees. These view functions must be audited as critical components.
- Front-Running Risk in
setFrozenTokens: If freezes are capped at the holder’s current balance, a user can escape a pending freeze by moving tokens out in a front-run. Allowing over-balance freezes or updating freeze levels incrementally reduces this window and prevents users from evading enforcement.
- Incorrect Variant Signaling: Misconfigured ERC-165 interface IDs can cause aggregators or bridges to skip required compliance checks. Variant detection should be validated during audits.
- Upgrade Risks: If the contract is upgradeable, malicious governance changes can weaken enforcement or whitelist attacker accounts. Use timelocks and transparent upgrade processes.
Conclusion
ERC-7943 shows that compliance for tokenized RWAs doesn’t need to be heavy or prescriptive. By reducing enforcement to a small set of predictable hooks, the standard lets issuers plug in their own policy engines while keeping tokens fully compatible with existing ERC-20/721/1155 ecosystems. The result is a lean, uniform interface that lowers integration friction, simplifies audits, and makes RWA deployments more practical for DeFi protocols.
As real-world assets continue moving on-chain, uRWA offers a flexible foundation suited for diverse regulatory environments. To ensure your implementation is secure, compliant, and audit-ready, consider a comprehensive RWA Security Audit before deployment.
Contents






