Why Access Control Failures Are Still the #1 Attack Vector?
Access control failures remain the top crypto attack vector in 2025. Discover why they persist and how projects can build stronger defenses.

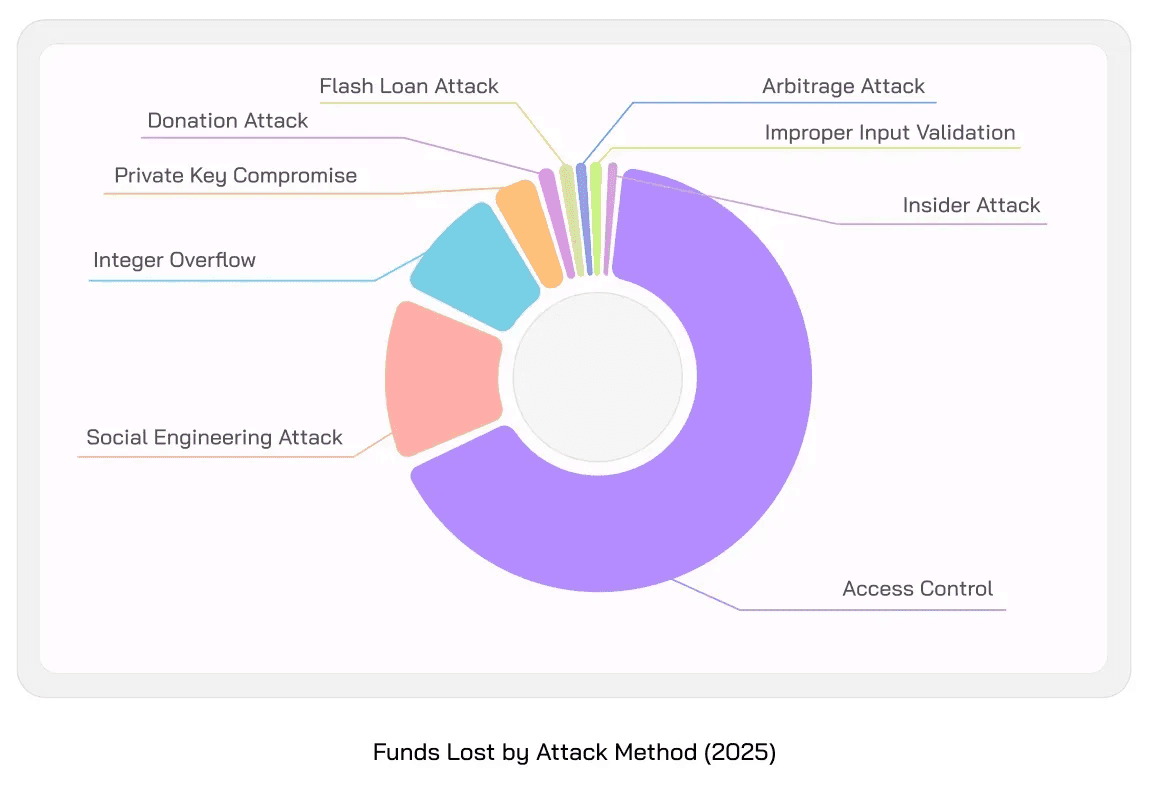
We recently published a report on the hacks that occurred in H1 2025. In H1, the total loss of funds exceeded $2.3 billion, with the top 3 attack vectors being Access Control, Social Engineering Attacks, and Integer Overflow, responsible for 95% of the funds lost.
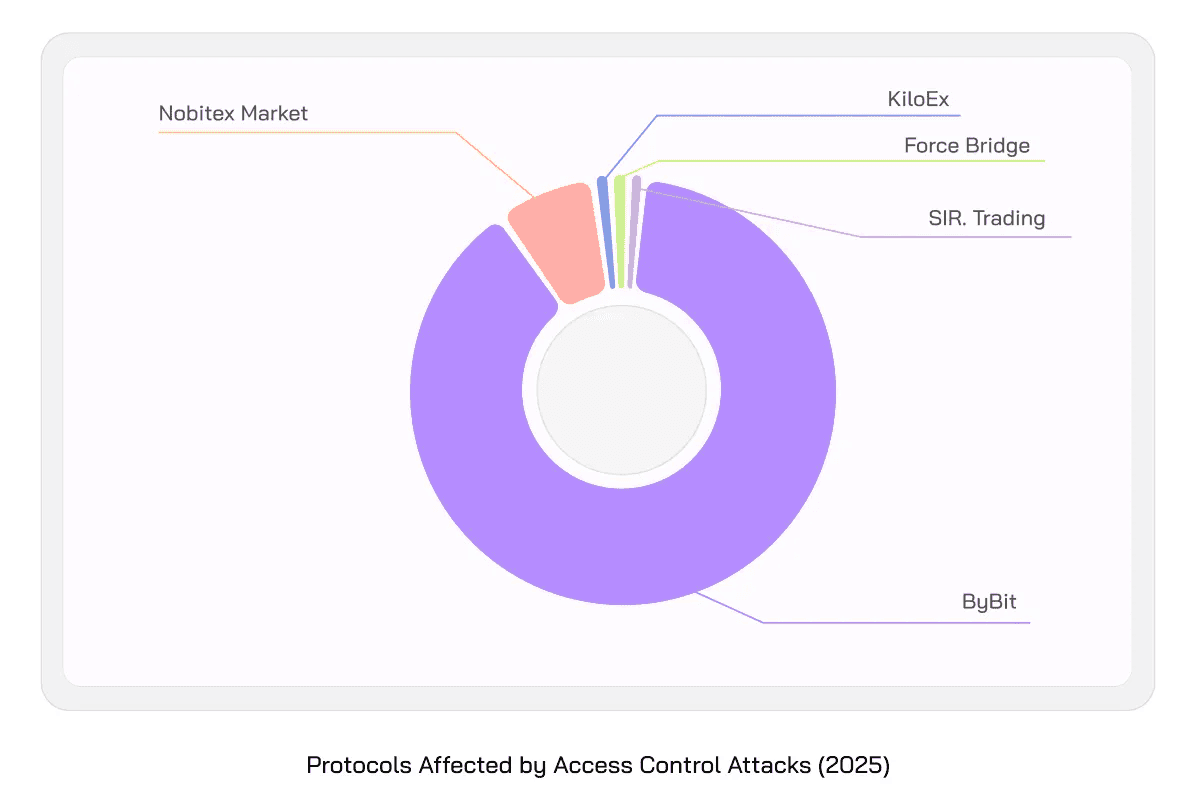
The attack vector holding the top place is still Access Control Attacks which was true for previous year as well. This attack vector is responsible for over $1.6 billion lost, representing 70% of the total loss of funds. This number comes from few major attacks across Bybit, Nobitex, KiloEx, and more.
What are Access Control Attacks?
Access control vulnerabilities occur when unauthorized actors can perform privileged actions actions due to missing or misconfigured permissions in smart contracts.
If functions meant only for admins, like contract upgrades, fund withdrawals, or parameter changes, lack proper restrictions (e.g., onlyOwner or Role-Based Access Control), attackers can exploit them to drain funds or alter contract behavior. Auditing and enforcing least-privilege principles are critical to mitigating this risk.
This year, the funds lost to Access Control vulnerabilities were $1.6 billion, and the protocols that lost funds include Bybit, Nobitex Market, KiloEx, Force Bridge, and SIR.trading.
Types of Access Control Issues
Access control vulnerabilities in smart contracts often arise from subtle implementation mistakes, misapplied permission models, or insecure integration patterns. Below are the key categories of access control issues observed in recent Web3 exploits, including those that led to some of the largest losses in H1 2025.
1. Missing Access Modifiers
One of the most basic yet common issues occurs when developers forget to apply access modifiers like onlyOwner, onlyAdmin, or custom role-based checks to sensitive functions. When high-privilege functions, such as withdraw(), mint(), or pause(), are left exposed, anyone can call them and perform unauthorized actions. These oversights are particularly dangerous because they can result in immediate, irreversible loss of funds.
2. Insecure Role-Based Access Control (RBAC)
Some protocols implement custom role-based systems without fully validating or enforcing them. This can include assigning roles incorrectly, failing to check them consistently across functions, or allowing users to escalate privileges by interacting with unprotected role-management logic. Even when using libraries like OpenZeppelin’s AccessControl, improper use or misconfigured roles can create unintended access pathways.
3. Improper Initialization in Upgradeable Contracts
In contracts using proxy upgrade patterns, failing to protect or lock initialization functions can open the door to access control failures. If a logic contract’s initialize() function can be called more than once, attackers can reinitialize the contract and assign themselves ownership or other privileged roles. This type of vulnerability typically occurs when developers omit the initializer modifier or fail to deploy contracts through secure upgrade frameworks.
4. External Call Dependencies
Access control checks are sometimes delegated to external contracts or third-party systems without ensuring those systems are themselves secure or trustworthy. For example, if a contract allows calls from a forwarding contract (such as a meta-transaction relay), but does not properly validate the origin of the forwarded call, an attacker may be able to route unauthorized actions through the forwarder. This kind of issue contributed to the KiloEx exploit, where a publicly accessible TrustedForwarder contract allowed an attacker to bypass intended access restrictions and manipulate oracle prices.
5. Inconsistent Access Enforcement Across Modules
In complex protocols made up of multiple interacting contracts, it’s common for access control to be implemented inconsistently across modules. One contract may properly restrict a sensitive action, while another, responsible for forwarding, pricing, or administrative logic, fails to do so. Attackers exploit these inconsistencies to perform sensitive actions indirectly, such as using one module to call a privileged function in another without proper authorization checks in between.
Many Access Control Attacks overlap with Social Engineering Attacks and can be read here: https://www.quillaudits.com/blog/web3-security/social-engineering-drained-over-340M
Don’t Let One Misstep Cost Millions
Don’t Let One Misstep Cost Millions
Access control misconfigurations caused $1.6B in losses in H1 2025. Ensure your smart contracts aren’t next. Let QuillAudits help you stay secure.
Why Access Control Remains the Most Critical Attack Vector?
Access control flaws consistently result in some of the largest single-event losses in Web3, largely because they strike at the heart of operational control. Unlike other vulnerability classes that might require chaining multiple bugs or manipulating external conditions, access control attacks often require just one misconfigured function or improperly assigned role to succeed. They are typically cheap to execute, easy to automate, and offer total control of a protocol’s funds or logic once exploited.
Additionally, attackers are getting more sophisticated at finding these issues across complex permission hierarchies, especially in contracts that are modular, proxy-based, or that integrate with off-chain infrastructure.
Preventative Measures and Recommendations
The first step to preventing access control vulnerabilities is to adopt a least privilege model, ensuring that each role or address can only execute what is necessary. Developers should leverage standardized and battle-tested libraries such as OpenZeppelin’s AccessControl, Ownable, and Initializable, and avoid writing custom access control logic unless necessary.
Thorough audit practices are essential, especially for permissioned functions. Audit teams should validate that each privileged function is properly protected, that access rights are correctly assigned, and that initialization logic is locked down immediately after deployment. Simulation testing and role fuzzing can be valuable in identifying unexpected permission paths. Protocols using proxy upgrades must ensure that only a tightly controlled admin address—ideally a multisig or timelock—can trigger upgrades, and that the implementation contract cannot be initialized more than once.
Finally, access control should be viewed not just as a technical concern, but also as an operational and governance issue. Clear role documentation, on-chain monitoring of privileged function calls, and restricting upgrade capabilities to decentralized or multi-party governance mechanisms can reduce the likelihood of both accidental misconfigurations and intentional misuse.
Conclusion
Access control remains the most critical and costly vulnerability class in the Web3 ecosystem. As smart contracts grow more complex and modular, the risk of misconfigured or insufficient permission checks increases significantly. The $1.6 billion in losses attributed to access control issues in H1 2025 alone underscores how even a single oversight, whether in initialization, role assignment or inter-contract communication can have devastating consequences.
These exploits are not always the result of novel attack techniques but rather of known security best practices being overlooked or inconsistently applied. The prevalence of these attacks reflects a broader need for rigorous access design, consistent permission enforcement, and careful consideration of how contracts interact within larger ecosystems. A deeper dive into these patterns and other major incidents can be found in our 2025 H1 Crypto Exploits Report, which outlines how access control failures remain the #1 attack vector.
Contents



