SwissBorg's $41M Exploit (Detailed Breakdown)
SwissBorg lost $41M in a Solana staking exploit via a compromised partner API. Learn how the hack happened and the recovery efforts underway.

On September 8, 2025, SwissBorg, a prominent crypto wealth management platform, fell victim to a sophisticated exploit that drained approximately 192,600 SOL valued at around $41M from its SOL Earn staking program. The attack targeted an external DeFi wallet managed through staking partner Kiln, exploiting a vulnerability in their API infrastructure rather than SwissBorg's core platform. This incident affected less than 1% of users and 2% of the platform's total assets, but it underscores the cascading risks of third-party dependencies in DeFi ecosystems.
Hack Analysis
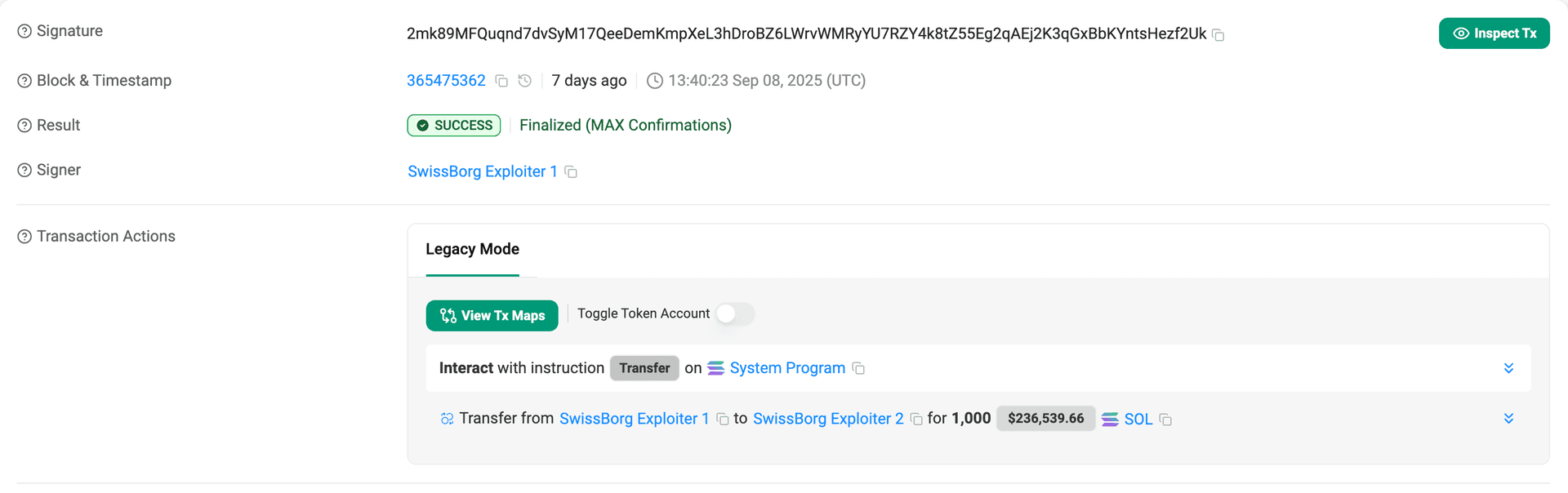
Starting on August 31st, in an unstaking transaction, the attacker embedded eight separate authorization instructions, transferring withdrawal authority across multiple SwissBorg/Kiln-managed stake accounts to the attacker's wallet (SwissBorg Exploiter 1). This operation masqueraded as a routine activity, avoiding immediate detection.
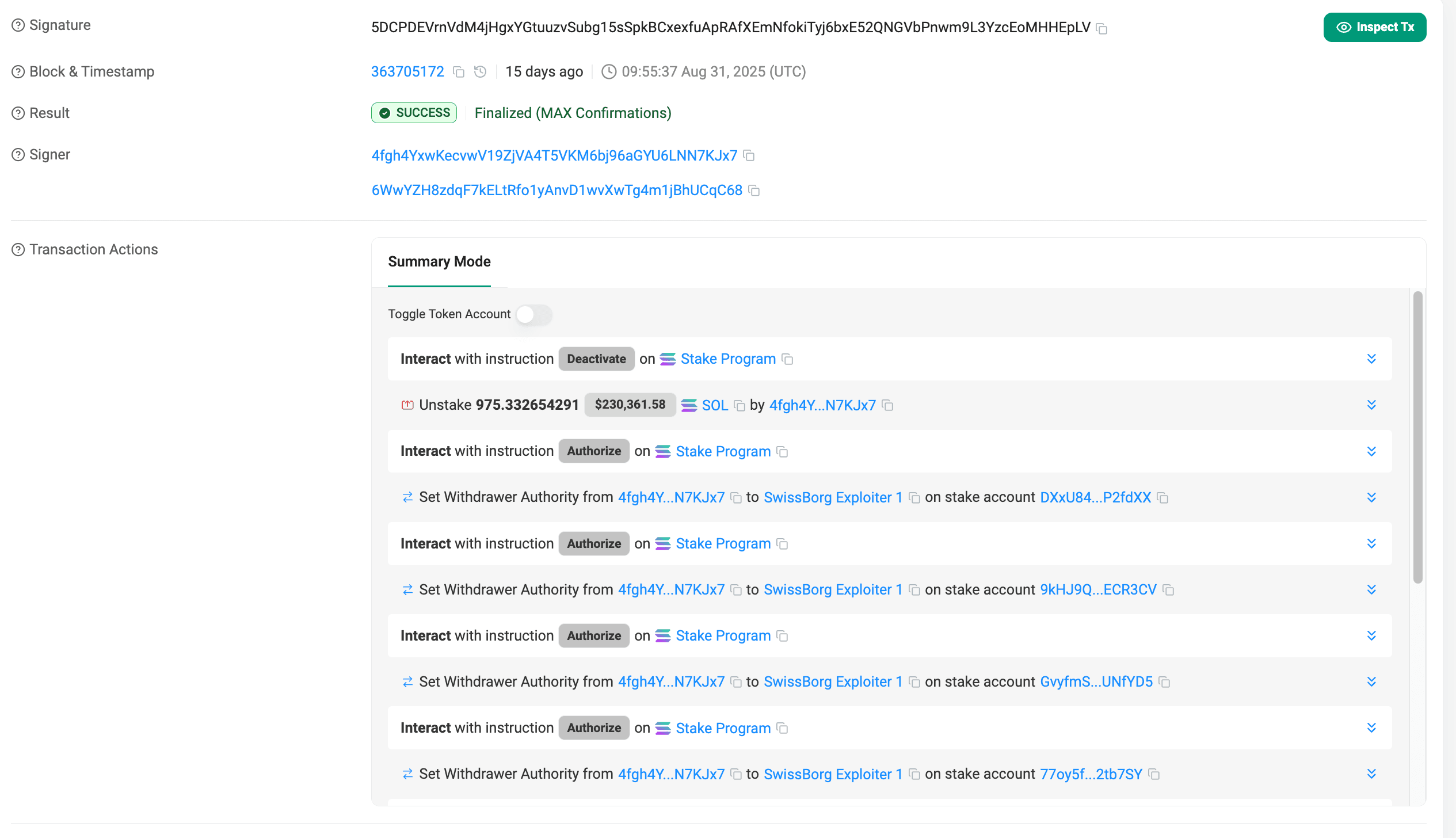
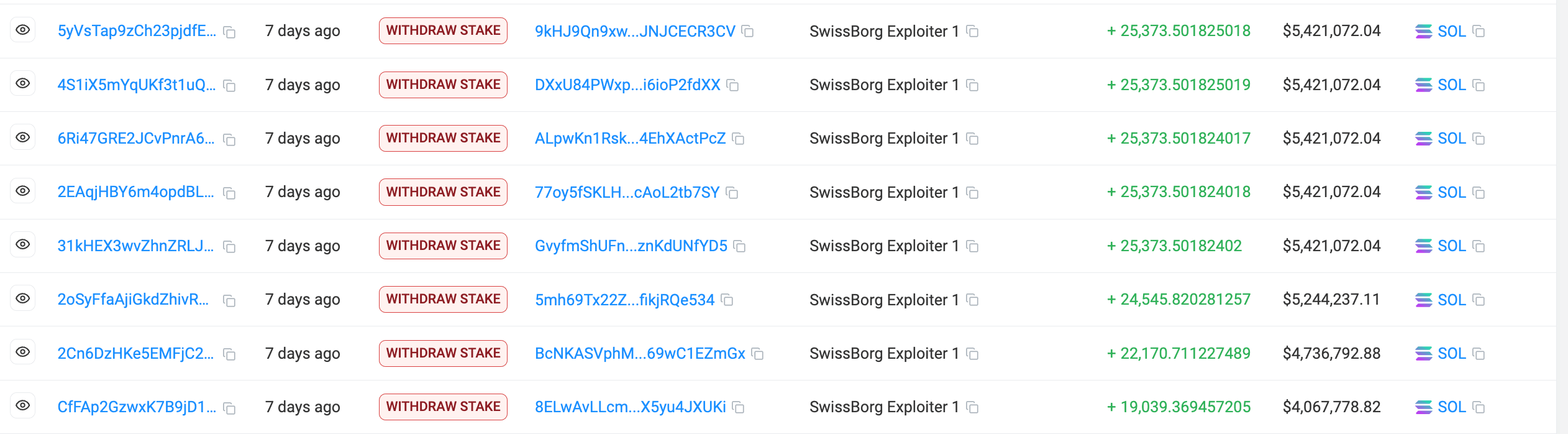
On September 8th, with withdrawal authority secured, the attacker activated the "skeleton key" setup, initiating unstaking and withdrawals from the compromised accounts. In mere minutes, 192,600 SOL was drained from the SOL Earn program via the exploited Kiln API.
Root Cause
The vulnerability stemmed from a compromise in Kiln's staking infrastructure, SwissBorg's third-party operator for SOL Earn deposits and withdrawals. Attackers gained unauthorized access to Kiln's API, enabling manipulation of stake account authorities (specifically the Staker role) without adequate anomaly detection or multi-signature confirmations. This allowed silent authority transfers while preserving the Withdrawer role, evading standard monitoring tools that prioritize withdrawal events. No evidence points to a smart contract flaw in SwissBorg's code, instead, it was an off-chain API breach exposing on-chain controls.
Relevant Address and Transactions
- Attacker EOAs -
- Setup Transaction: 5DCPDEVrnVdM4jHgxYGtuuzvSubg15sSpkBCxexfuApRAfXEmNfokiTyj6bxE52QNGVbPnwm9L3YzcEoMHHEpLV
- Bulk Transaction: 5Es6C4oT2SDXaE86P2KUCAJVfdRvfSv8oEMvtJtwsatJcFJ75BxYh4SbjBMEca6voKkc8Pc2Ja1wNE7CHmf3mUx5
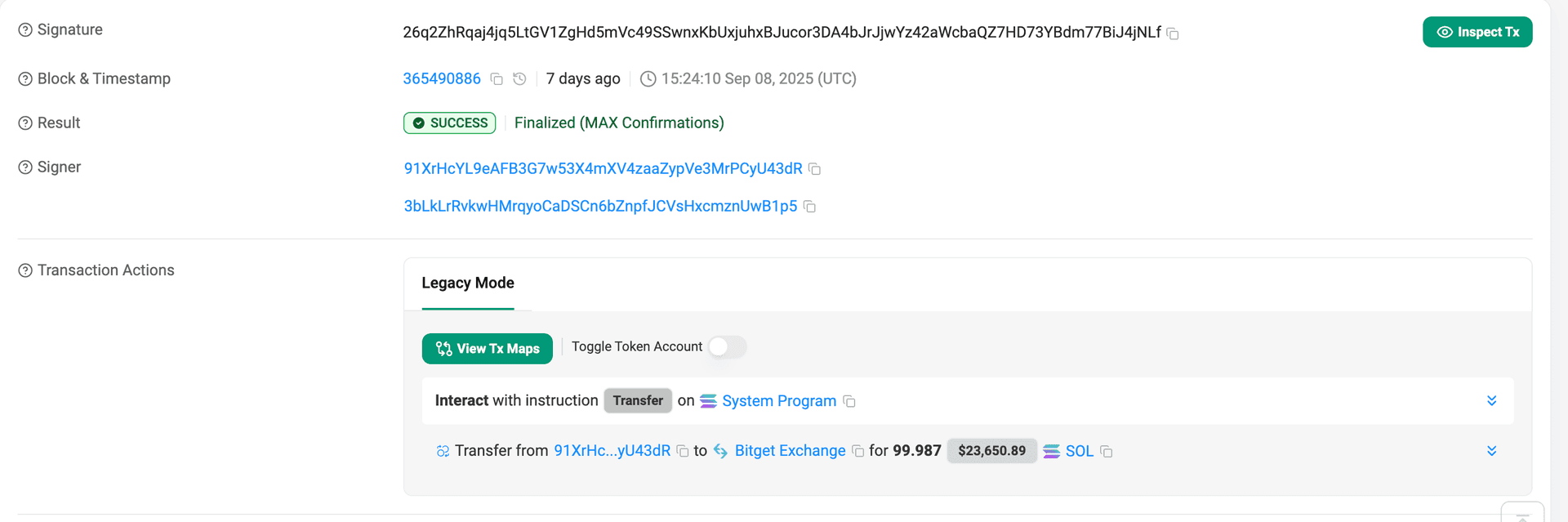
- Bitget Exchange Deposit Transaction: 26q2ZhRqaj4jq5LtGV1ZgHd5mVc49SSwnxKbUxjuhxBJucor3DA4bJrJjwYz42aWcbaQZ7HD73YBdm77BiJ4jNLf
Funds Flow After Attack
$40.7M (~189,524 SOL) was transferred in a single large transaction to a dormant holding wallet, likely intended for future mixing or conversion.
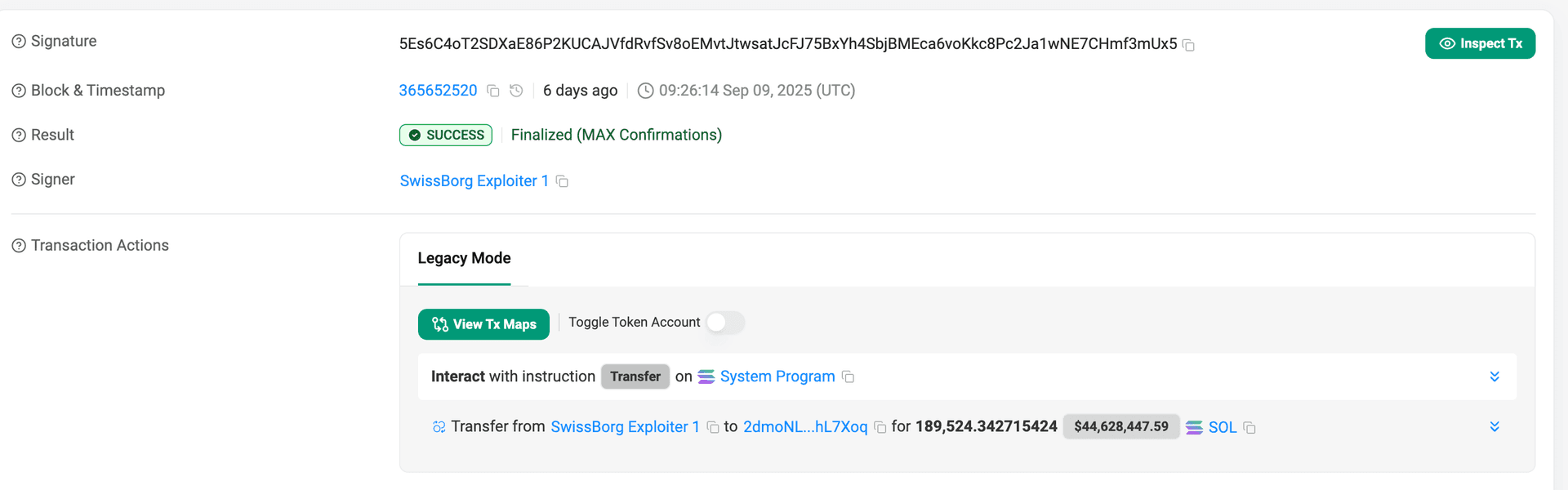
The funds remain unmoved and are still sitting in the attacker’s EOA.
1,000 SOL was routed through multiple hops, starting with an initial split, moving through intermediate wallets, and ultimately deposited to the Bitget exchange.
Secure Every Layer of Your DeFi Stack!
Secure Every Layer of Your DeFi Stack!
The SwissBorg exploit proves risks extend beyond smart contracts into APIs, integrations and partners. QuillAudits helps secure every layer, on-chain and off-chain, so hidden gaps don’t put your platform at risk.
Post Attack Mitigation
The exploit was traced to a compromised partner API, affecting less than 1% of users in the SOL Earn Program. SwissBorg confirmed its core app and other Earn strategies remained fully secure, while pausing Solana staking and allocating treasury funds to support recovery.
Cyrus Fazel stated that no user would incur losses, committing to cover any recovery shortfalls from the company treasury. He clarified that the breach was limited to an external wallet tied only to the SOL Earn strategy, with all other funds unaffected.
As the infrastructure partner, Kiln disabled its dashboard, widgets, and APIs during the investigation, initiating precautionary steps to safeguard validator operations and mitigate further risk.
Conclusion
The SwissBorg exploit is a stark reminder that DeFi security extends beyond code, third-party APIs and staking operators are high-risk vectors demanding rigorous vetting and continuous monitoring. Attackers exploited a four-day preparation window with on-chain signals that went undetected, draining millions in minutes. Implement defense-in-depth with tools like real-time authority alerts and simulation checks to catch threats early. For protocols relying on partners, regular penetration testing of integrations is non-negotiable. This "bad day" for SwissBorg highlights resilience in response but reinforces the need for proactive audits to prevent the next one.
Contents



