Bunni V2 Exploit Drains $8.3M via Liquidity Flaw
A precision bug in BunniHook’s liquidity accounting led to a Bunni V2 exploit, draining $8.3M from Ethereum and UniChain pools.

On September 2, 2025, the Bunni V2 protocol suffered a major exploit resulting in the loss of $2.4M on Ethereum and $5.9M on UniChain. The attack targeted flaws in the liquidity accounting mechanisms of BunniHook, specifically exploiting a precision error by performing multiple carefully sized swaps that yielded more tokenOut than intended.
Bunni operates as a liquidity hook built on top of Uniswap V4. Unlike Uniswap V4’s native mechanism, Bunni introduces its own liquidity curve called the Liquidity Distribution Function (LDF). The system is designed so that after every trade, Bunni checks whether the LDF curve has shifted. If a change is detected, the protocol calculates the surplus liquidity and rebalances the pool to maintain the correct token ratio.
The attacker discovered that by executing trades of very specific sizes, they could manipulate this LDF mechanism. These trades caused the rebalancing calculation to produce incorrect results, distorting how much each LP share should represent. By repeating this process across multiple swaps, the exploiter was able to systematically withdraw more tokens than they were entitled to, ultimately draining significant funds from the pools.
Hack Analysis
On Ethereum, the attacker initiated the exploit by taking a 3M USDT flash loan from Uniswap v3.
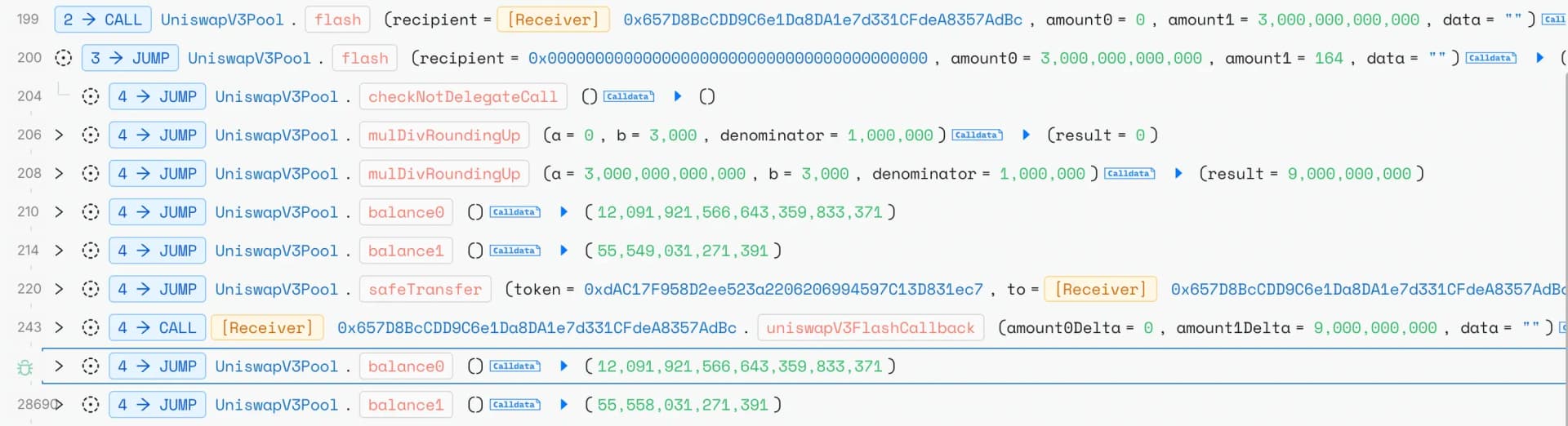
The attacker executed a series of exact-input swaps on the USDC/USDT pool through Uniswap v4’s PoolManager , deliberately using amountSpecified values to control trade sizing with precision.
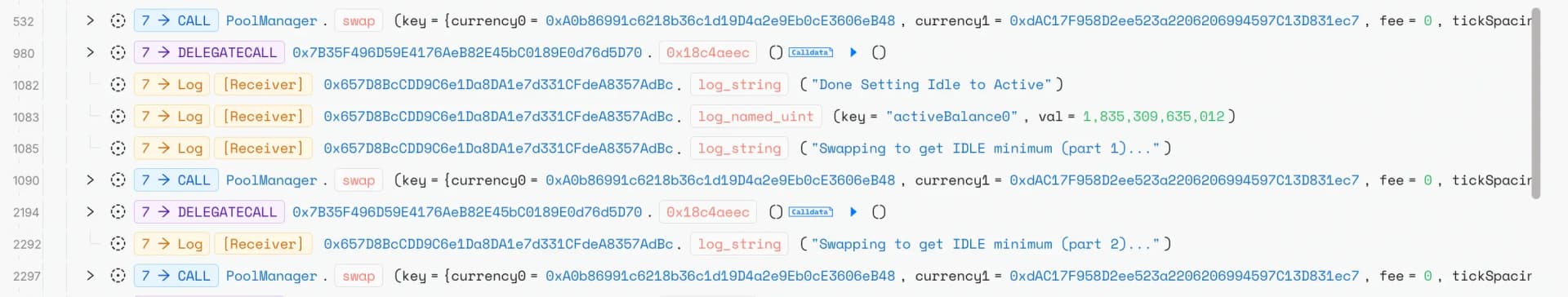
The attacker executed an initial series of swaps to manipulate the pool's price dynamics, followed by 44 tiny withdrawals that exploited a precision error in Bunni's withdrawal logic located in BunniHubLogic::withdraw(). These withdrawals leveraged rounding errors in the idle balance calculation (balance.mulDiv(shares, currentTotalSupply)) to disproportionately decrease the pool's active USDC balance from 28 wei to 4 wei an 85.7% reduction despite burning minimal liquidity shares.
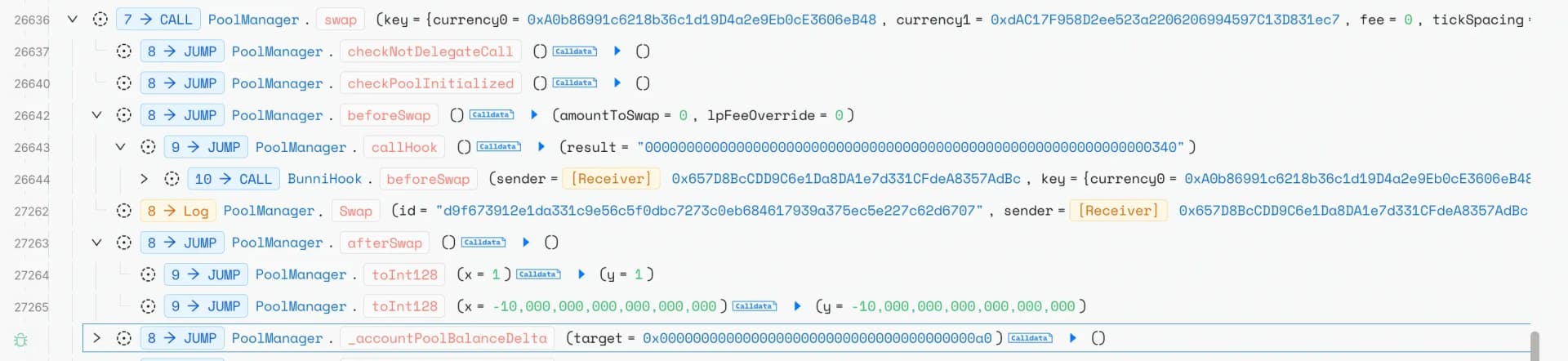
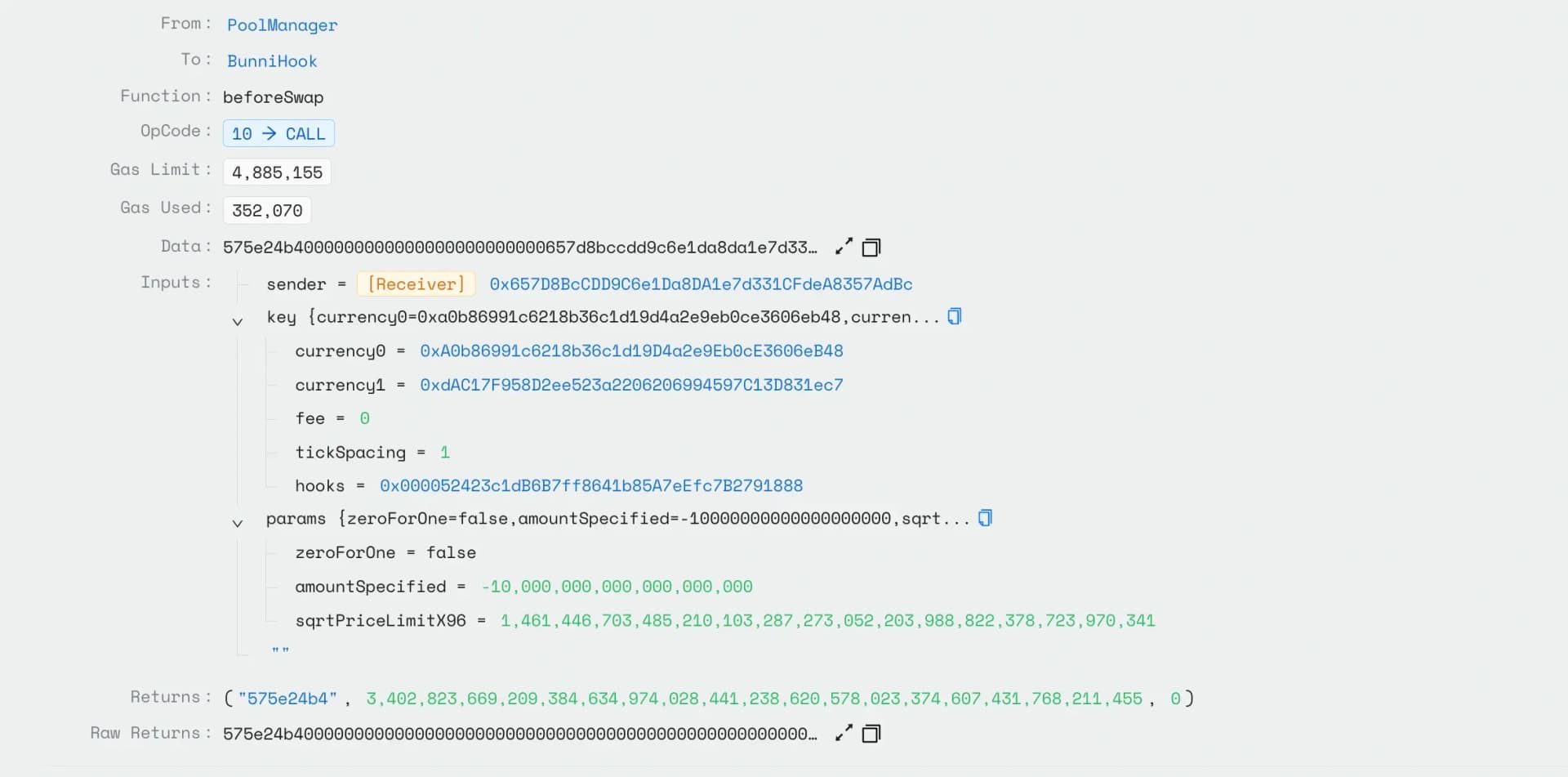
This manipulation caused the pool's total liquidity to erroneously decrease by 84.4%, creating an artificial liquidity shortage. The attacker then performed large swaps that triggered the liquidity calculation to switch from totalLiquidityEstimate0 to totalLiquidityEstimate1, creating a sudden artificial liquidity increase that the attacker profitably sandwiched to extract the stolen funds.
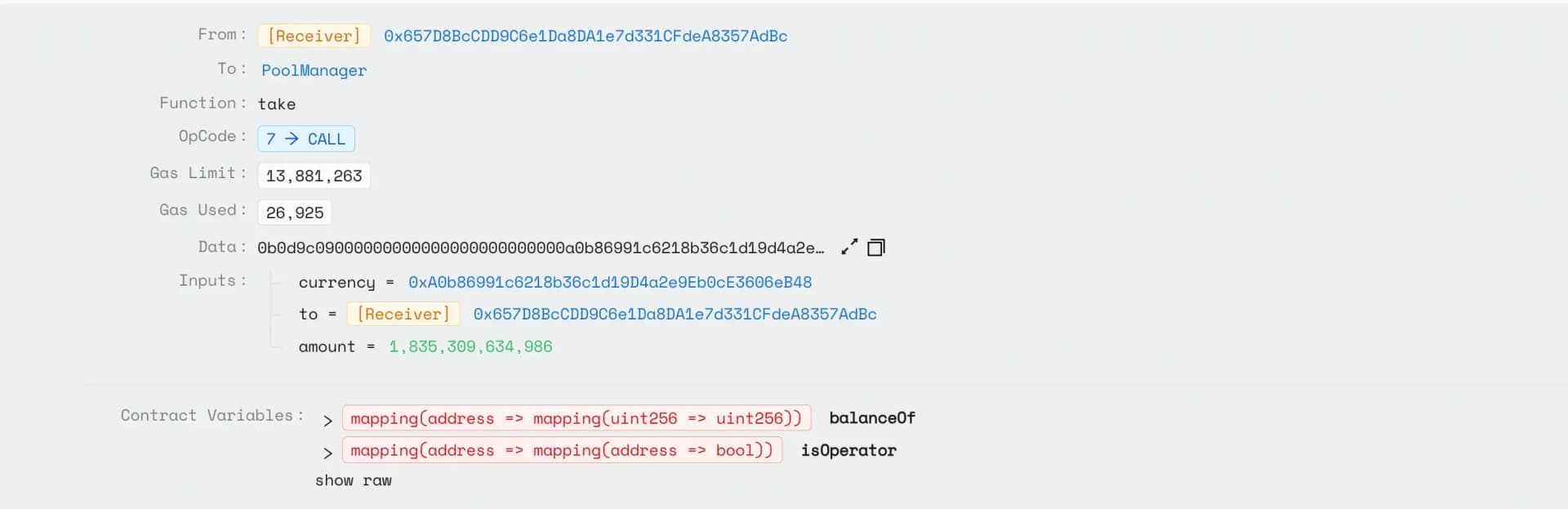
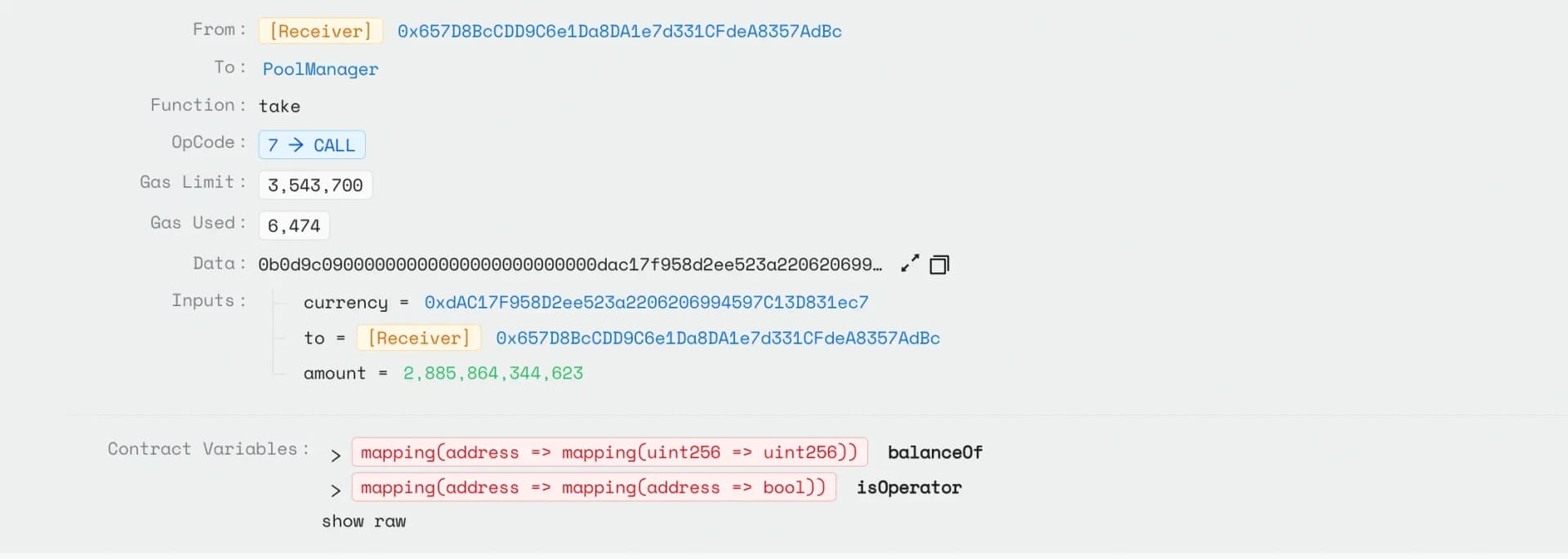
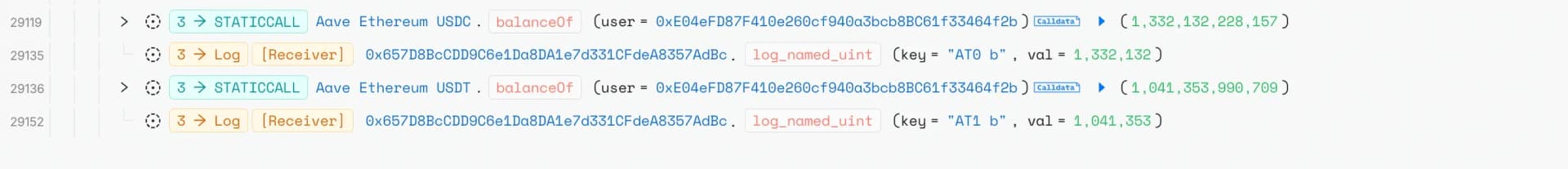
Attacker then repayed the flashloan + fee and deposited the stolen USDC and USDT into the Aave protocol, receiving synthetic aTokens in return.
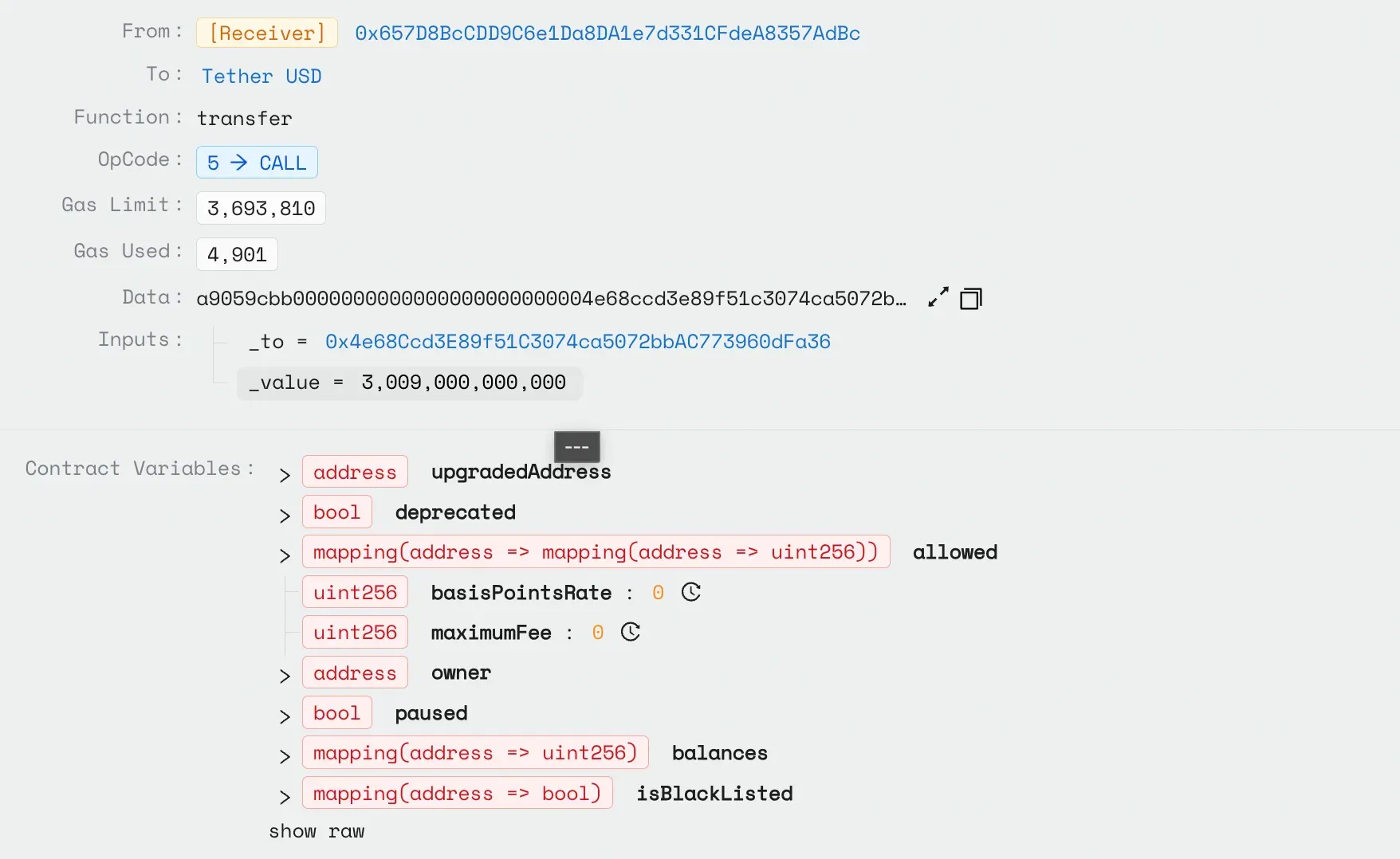
The attacker repeated the same strategy on Unichain, securing a 2000 WETH flash loan from Morpho and extracting 1366 WETH and the stolen WETH was then bridged from Unichain to Ethereum via the Across protocol.
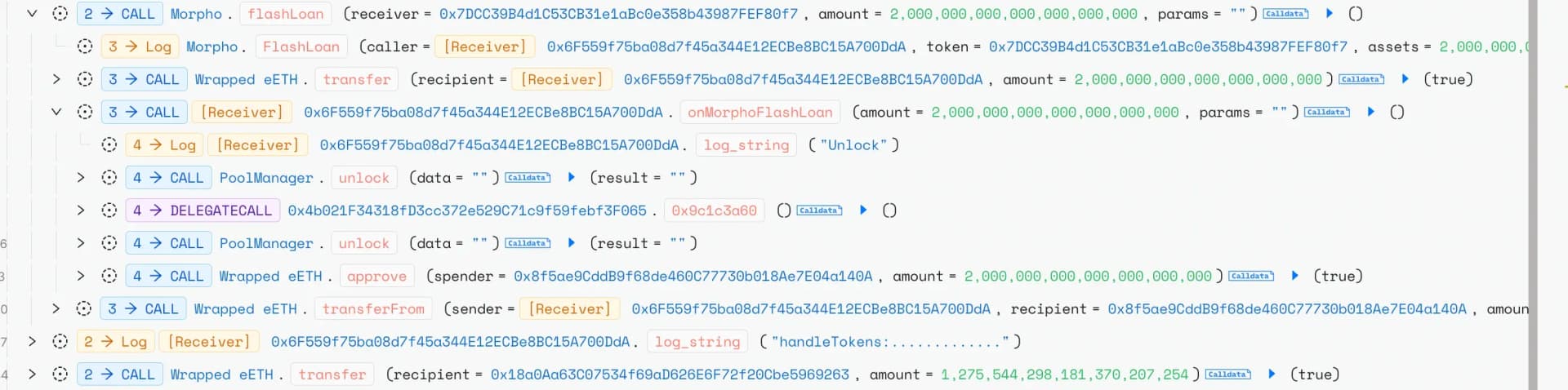
Root Cause
The exploit stemmed from a rounding direction vulnerability in Bunni's withdrawal mechanism, specifically in the BunniHubLogic::withdraw() function. The critical flaw was in the calculation balance - balance.mulDiv(shares, currentTotalSupply) where rounding down was intentionally implemented during development under the assumption that underestimating liquidity would be safer. However, when executed through 44 consecutive tiny withdrawals, these rounding errors accumulated disproportionately, reducing the pool's active USDC balance by 85.7% despite burning minimal shares. This created an artificial liquidity shortage that could be exploited through sandwich attacks on subsequent liquidity recalculations.
Protect Your Protocols from Hidden Logic Flaws
Protect Your Protocols from Hidden Logic Flaws
The Bunni v2 hack drained $8M+ due to a tiny logic flaw. Our expert audits safeguard your smart contracts, DeFi hooks, and liquidity mechanisms against hidden risks.
Relevant Address and Transactions
- Primary Attacker EOA: 0x0c3d8fa7762ca5225260039ab2d3990c035b458d
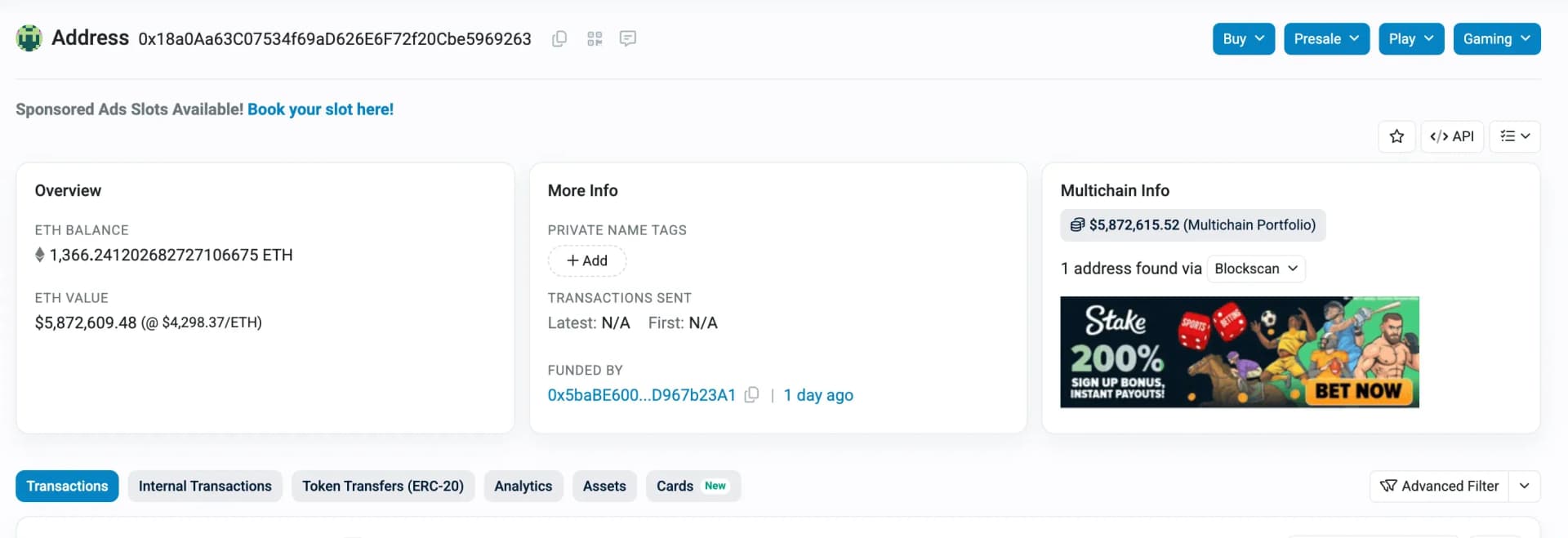
- Secondary Attacker EOA: 0x18a0Aa63C07534f69aD626E6F72f20Cbe5969263
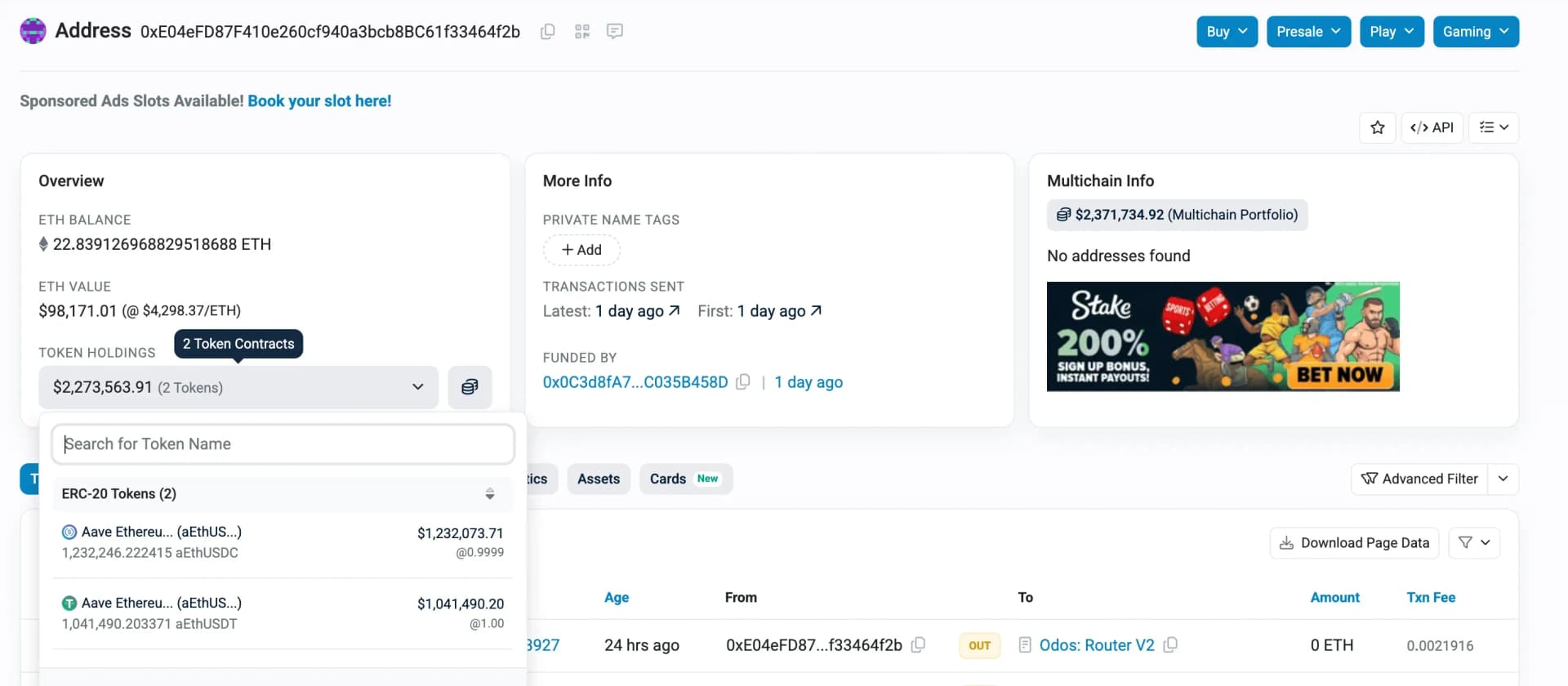
- Tertiary Attacker EOA: 0xe04efd87f410e260cf940a3bcb8bc61f33464f2b
- Attack Transaction (Ethereum): 0x1c27c4d625429acfc0f97e466eda725fd09ebdc77550e529ba4cbdbc33beb97b
- Attack Transaction (UniChain): 0x4776f31156501dd456664cd3c91662ac8acc78358b9d4fd79337211eb6a1d451
Funds Flow After Attack
Around $2.2M remains in the attacker’s EOA.
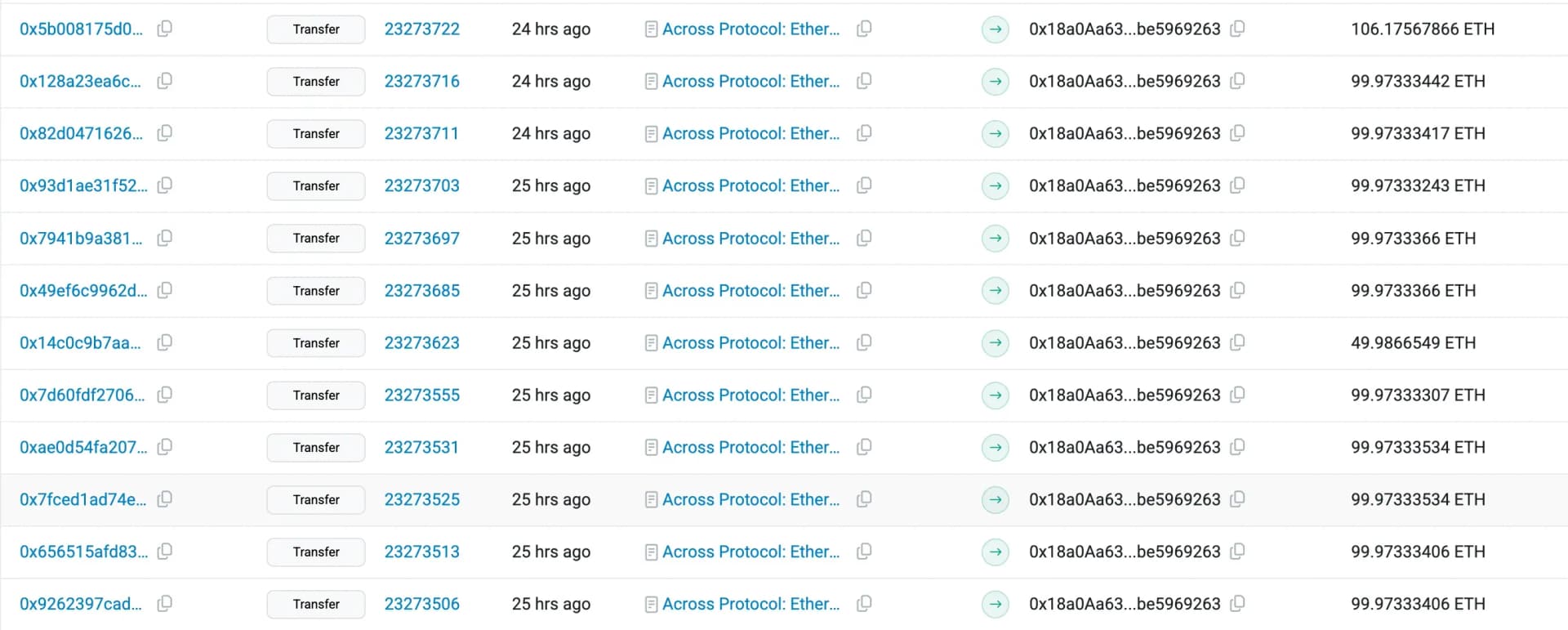
The attacker has also bridged 1,366 ETH from Unichain to Ethereum, which is currently held in their EOA.
Post Attack Mitigation
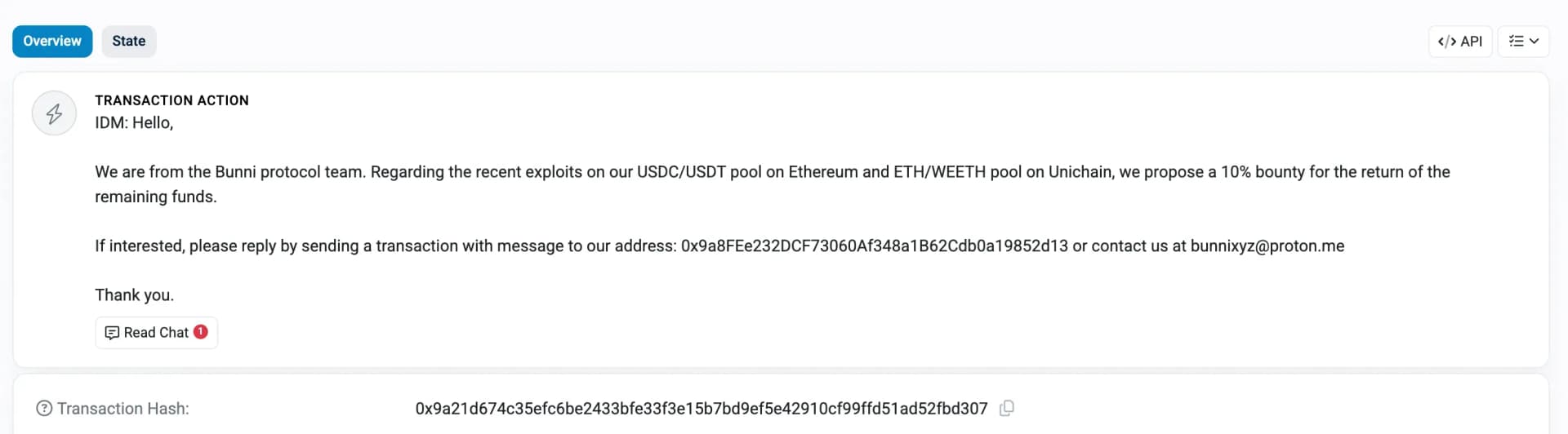
The Bunni protocol team responded promptly by halting withdrawals across all deployed chains.
Additionally, they reached out to the attacker and offered a 10% bounty reward Etherscan Transaction
Conclusion
The Bunni v2 exploit highlights the risks of introducing custom liquidity logic on top of Uniswap v4. A subtle precision error in the Liquidity Distribution Function (LDF) was exploited through carefully structured swaps to systematically drain funds. In total, the attacker extracted over $8M+ across Ethereum and Unichain, with portions already bridged back to Ethereum. This incident reinforces the need for thorough testing and careful design when implementing new hooks and accounting mechanisms in DeFi protocols.
Contents



