Cross Curve $1.4M Implementation Bug [Explained]
How a simple implementation bug led to a $1.4M loss at Cross Curve, explained with clear security lessons for DeFi teams.
![Cross Curve $1.4M Implementation Bug [Explained]](/_next/image?url=https%3A%2F%2Fambitious-kindness-505c138052.media.strapiapp.com%2FCross_Curve_Implementation_Bug_Explained_a389386222.png&w=1080&q=75)
This report analyzes the $1.4M exploit affecting the CrossCurve protocol, caused by an implementation flaw in its cross-chain messaging logic. The attacker abused a publicly callable execution path combined with weak validation to inject a malicious payload and mint a large supply of EYWA tokens. By bypassing intended authentication checks, the exploit was successfully repeated across multiple chains, with the majority of losses occurring on Arbitrum. This write-up breaks down the attack flow, identifies the root cause, traces post-exploit fund movements, and outlines the mitigation steps taken by the CrossCurve team.
Hack Analysis
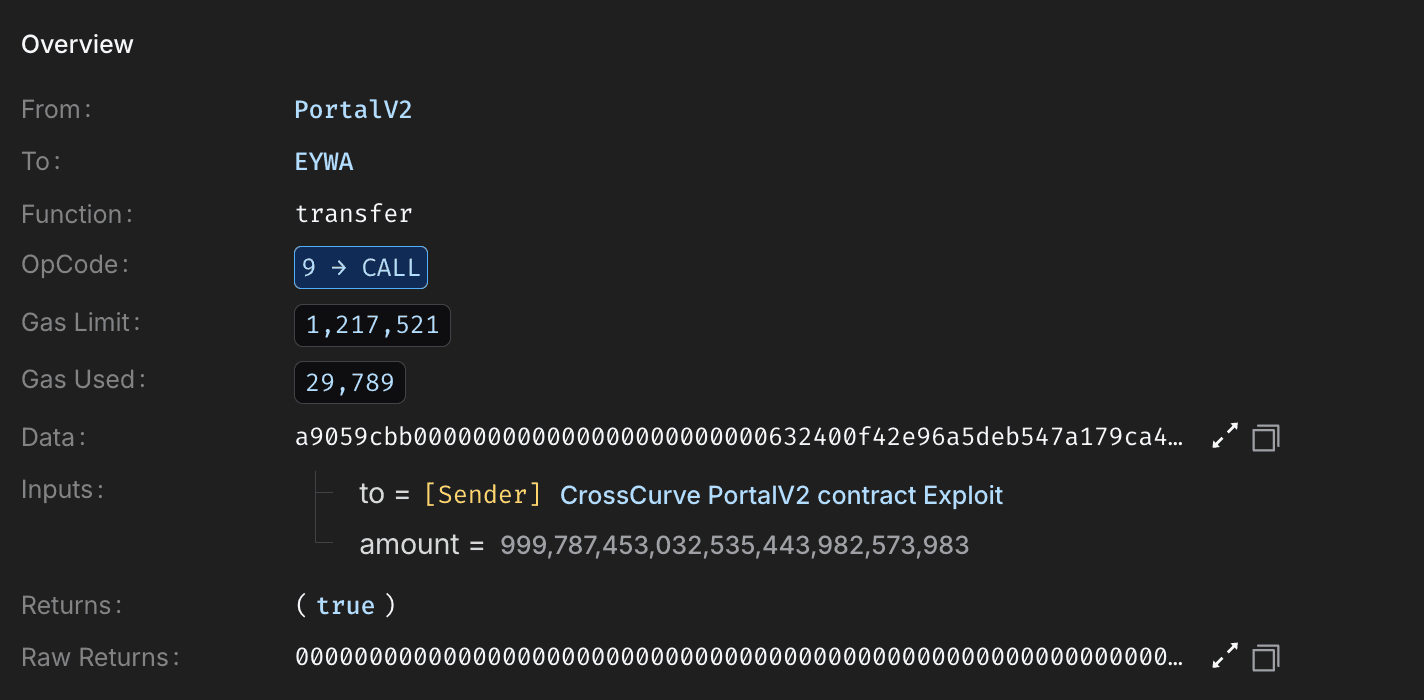
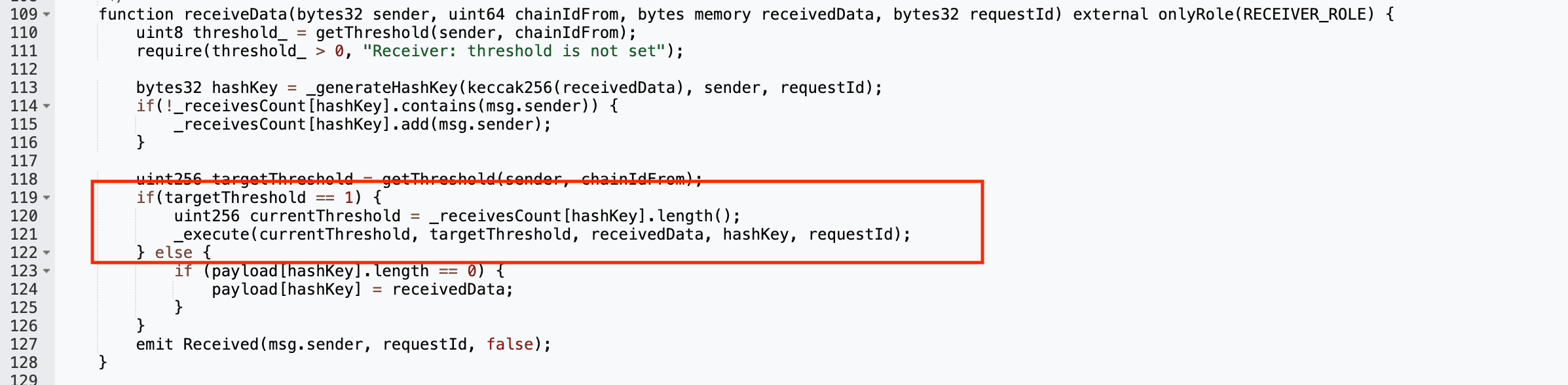
The attacker generated a fresh commandId and spoofed the sourceChain and sourceAddress to appear as a legitimate cross-chain message. They crafted a malicious ABI-encoded payload containing target contracts, token amounts including ~999.8M EYWA and instructions to transfer funds to their own wallet. This payload was executed by directly calling expressExecute.
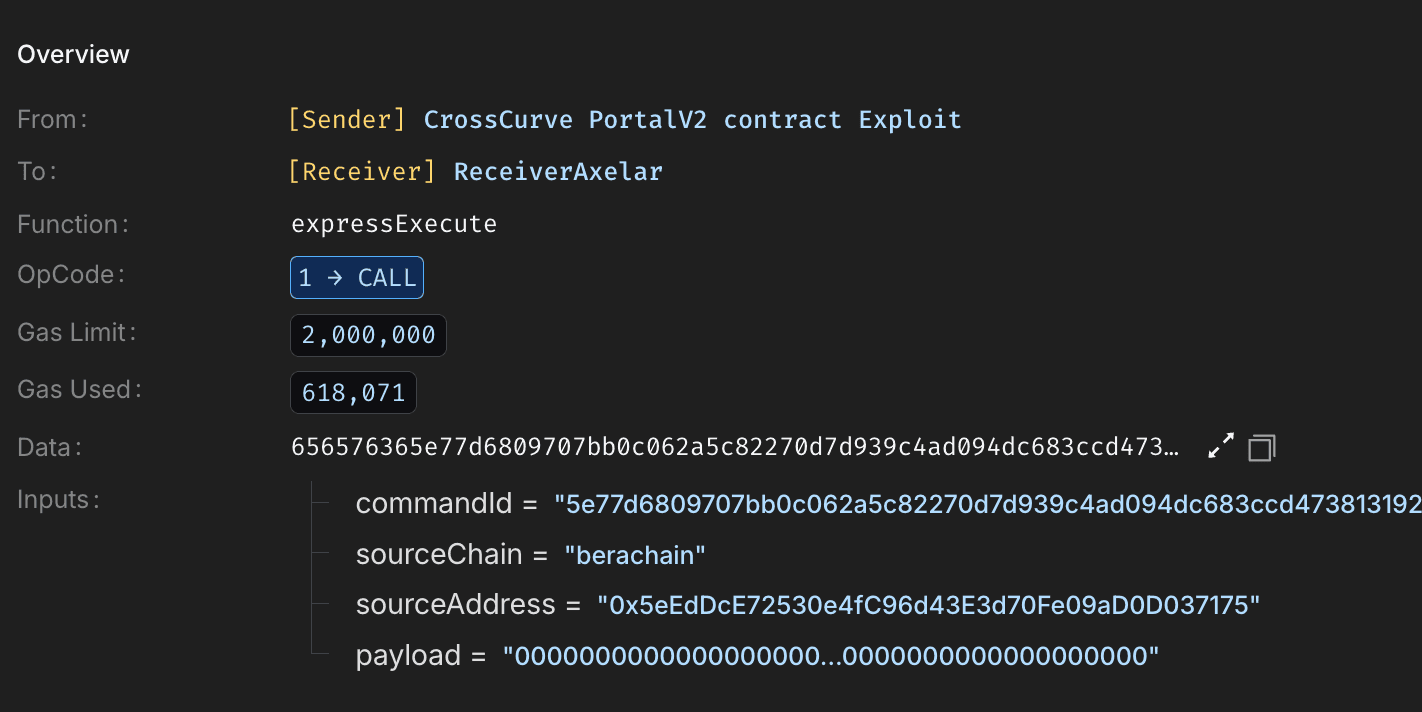
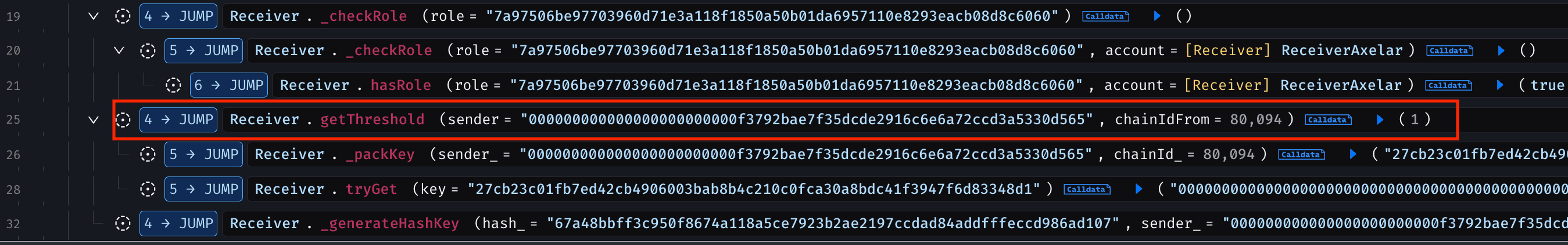
The contract only checked whether the commandId had been previously executed, which returned false. Due to the confirmation threshold being set to 1 , no additional guardian verification was required, allowing the malicious request to pass validation.
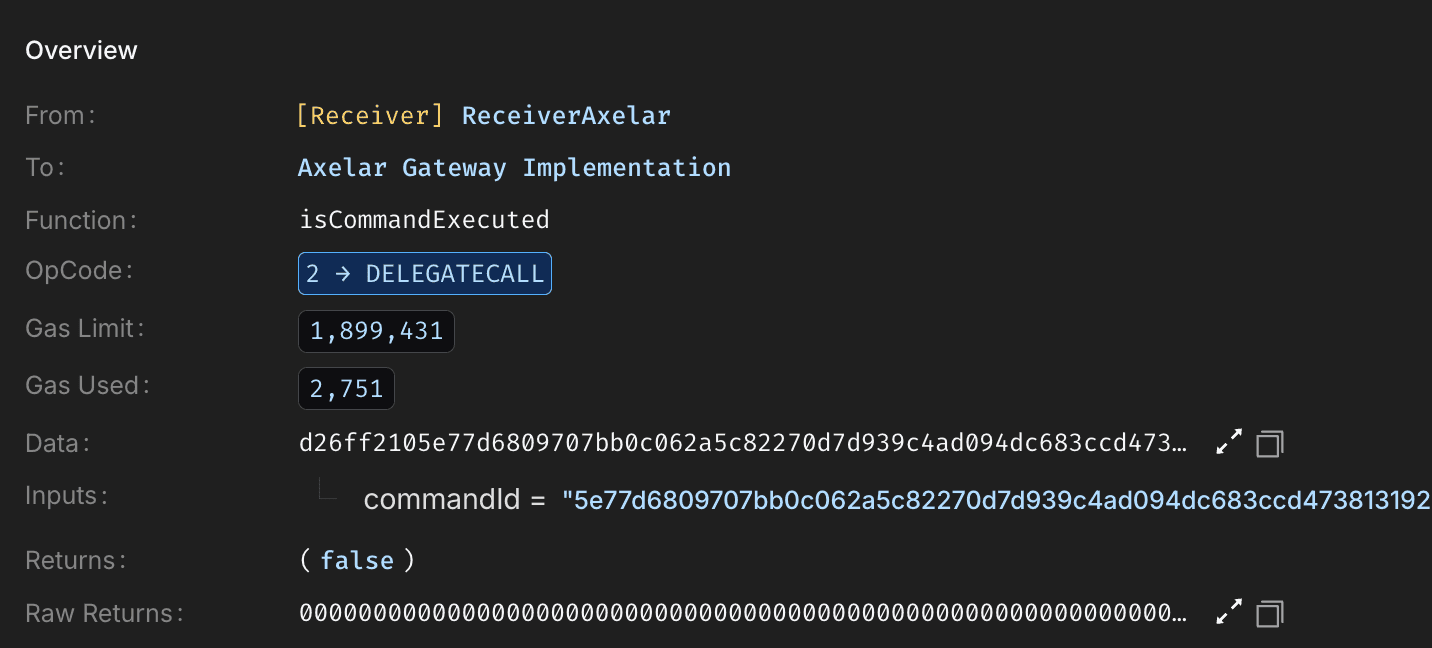
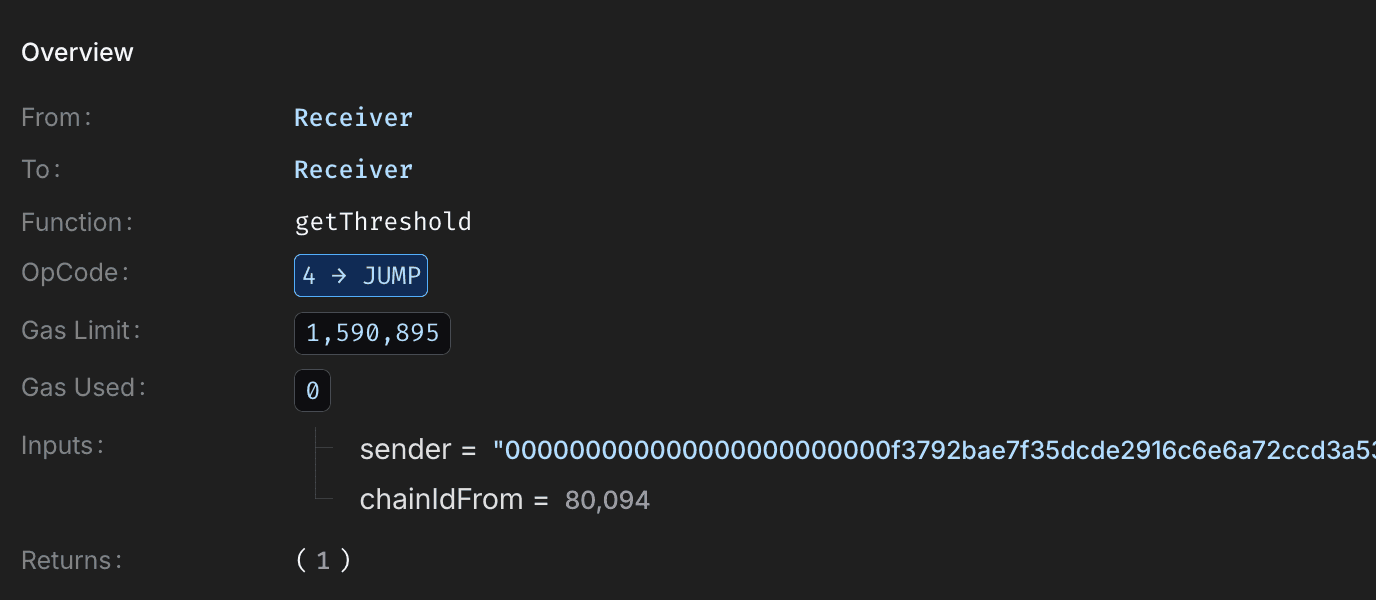
With validation bypassed, the contract decoded and executed the attacker controlled payload. Internal state was updated to mark the command as executed and reset receiver related mappings, simulating a valid cross-chain receipt.
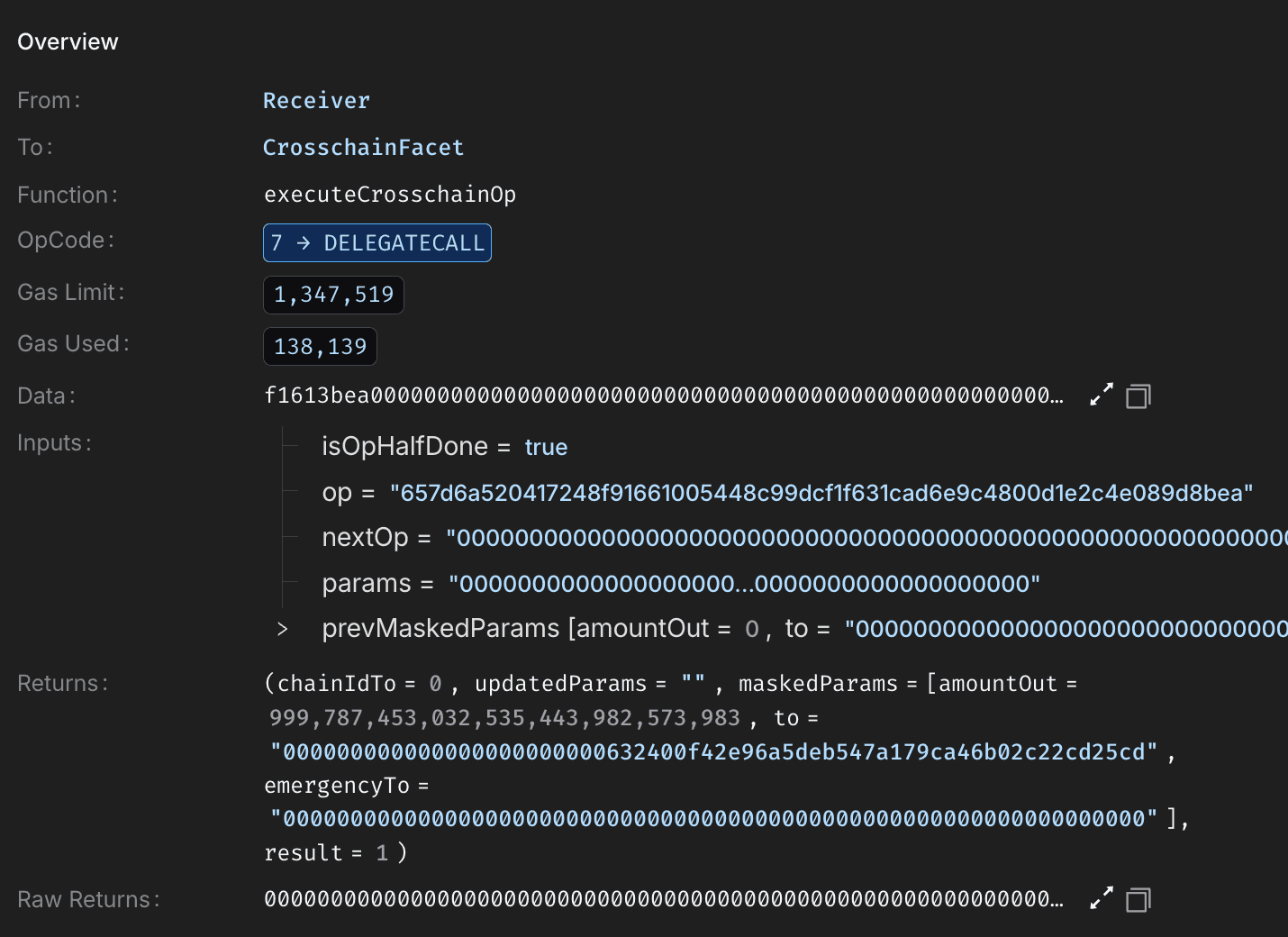
Masking the exploit as a legitimate operation, the payload resulted in the minting or transfer of 999,787,453 EYWA tokens directly to the attacker’s EOA.
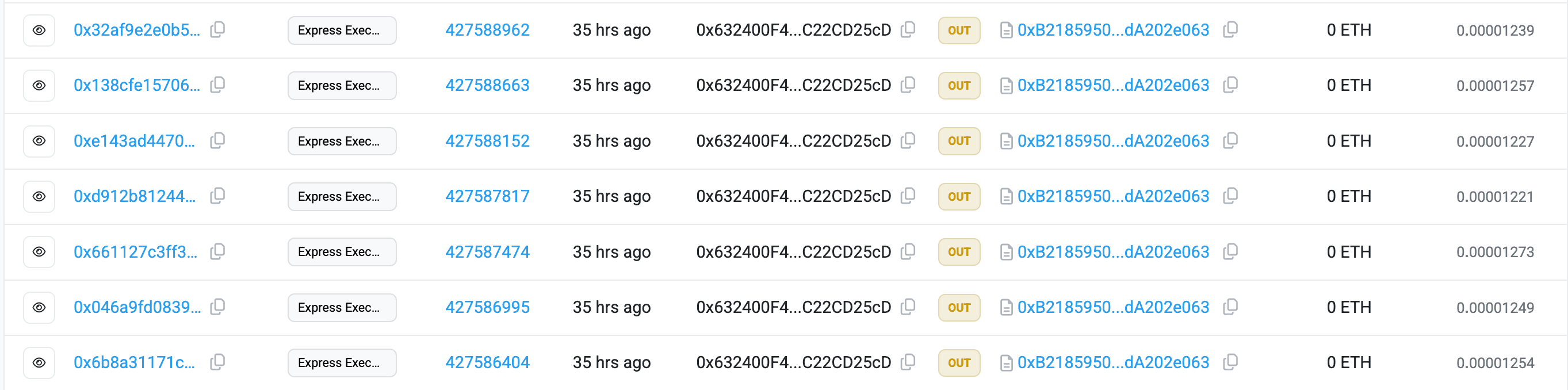
The attacker repeated the same exploit across multiple chains, with the majority of the funds stolen on Arbitrum.
The following flow diagram illustrates the sequence of actions taken by the attacker:

Root Cause
The exploit stems from a critical access control flaw in CrossCurve’s Axelar integration, specifically within the ReceiverAxelar contract. The expressExecute() function designed to allow expedited cross chain message execution in exchange for higher gas fees is publicly callable and lacks sufficient authentication. The only enforced check is whether a given commandId has already been executed, which can be trivially bypassed by supplying a fresh, unused identifier.
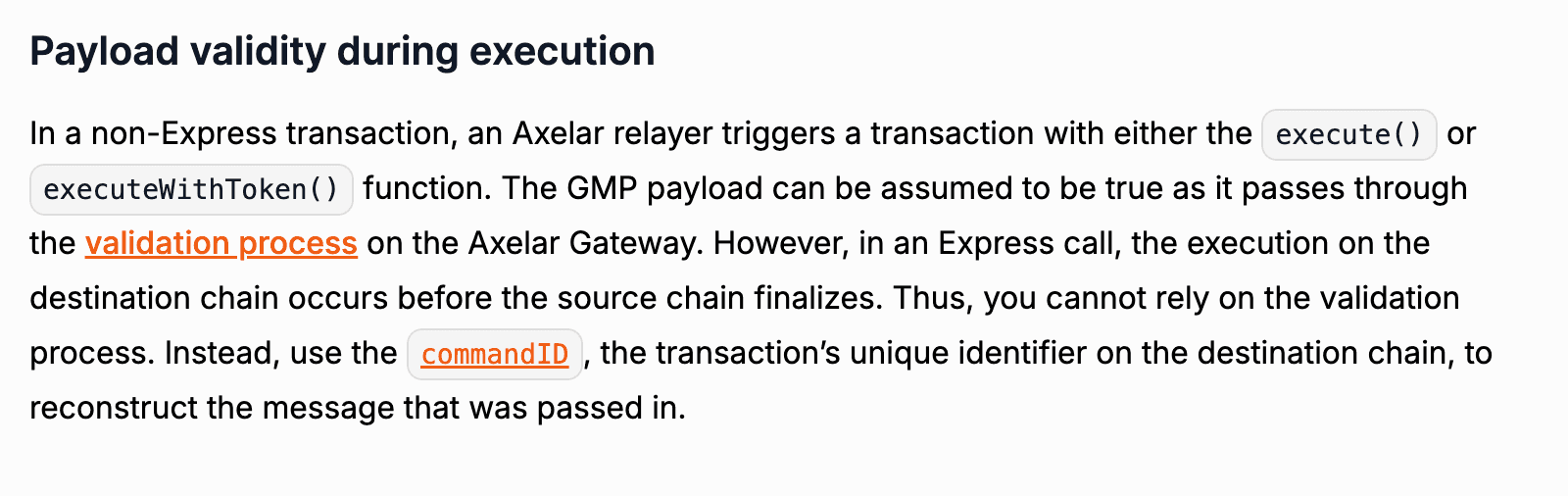
This issue is compounded by a misconfigured confirmation threshold of 1 , effectively disabling multi guardian validation. Together, these weaknesses allow arbitrary payload execution without legitimate cross-chain authorization.
Secure Your Cross-Chain Logic Before Attackers Do
Secure Your Cross-Chain Logic Before Attackers Do
Implementation bugs and weak cross-chain validation are top DeFi attack vectors. QuillAudits helps uncover hidden execution paths and access control risks before they cause major losses
Funds Flow After Attack
ost of the malicious activity took place on the Arbitrum network. After the exploit, the attacker gradually converted the stolen tokens into WETH using the CoW Protocol, highlighting why securing Arbitrum projects requires close attention to cross-chain execution paths and post-exploit fund movement patterns.
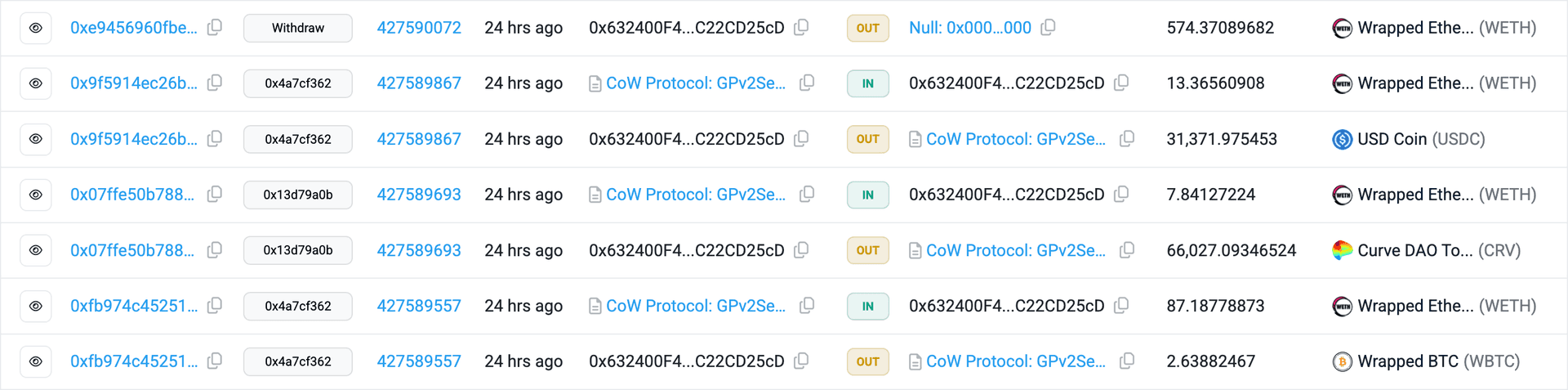
Once the assets were consolidated into WETH, they were bridged from Arbitrum to the Ethereum mainnet via the Across Protocol.
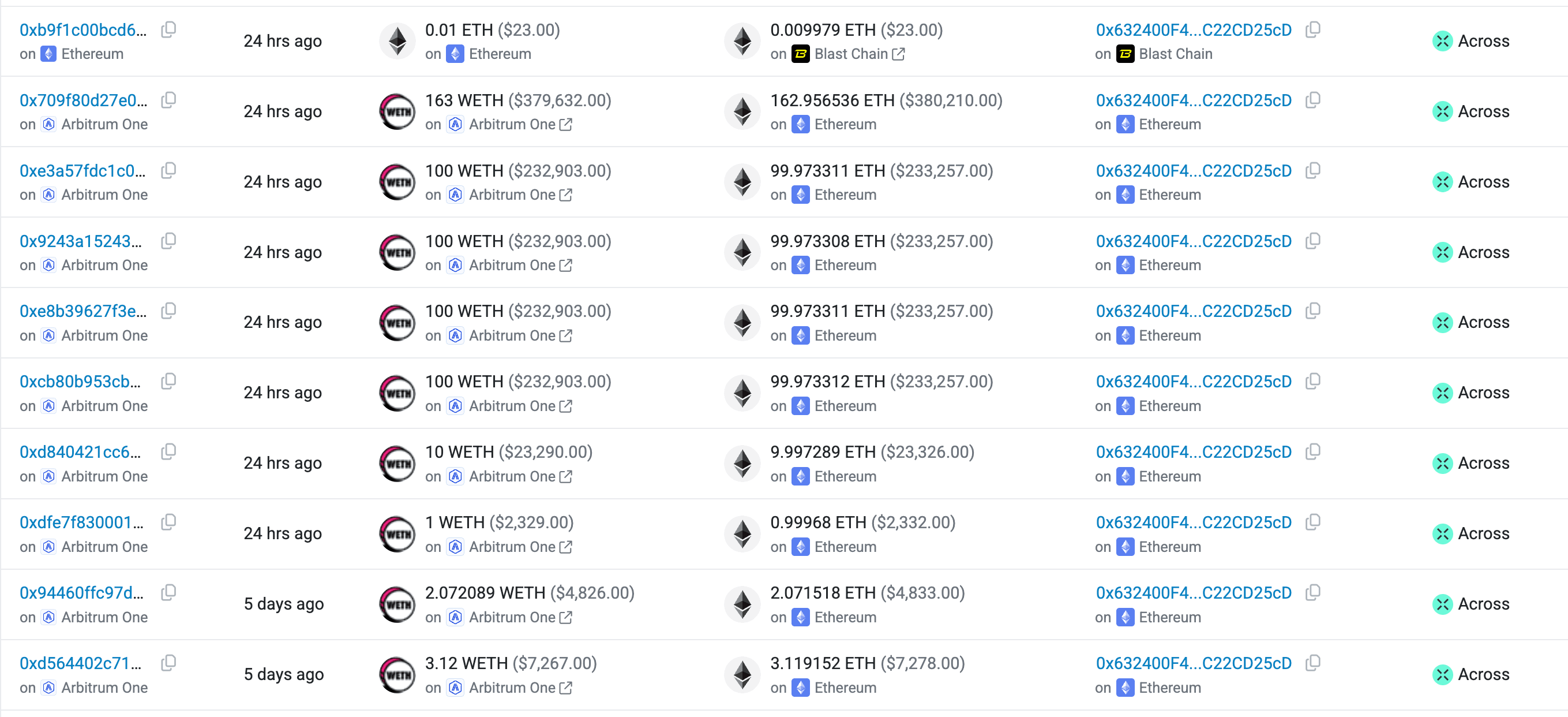
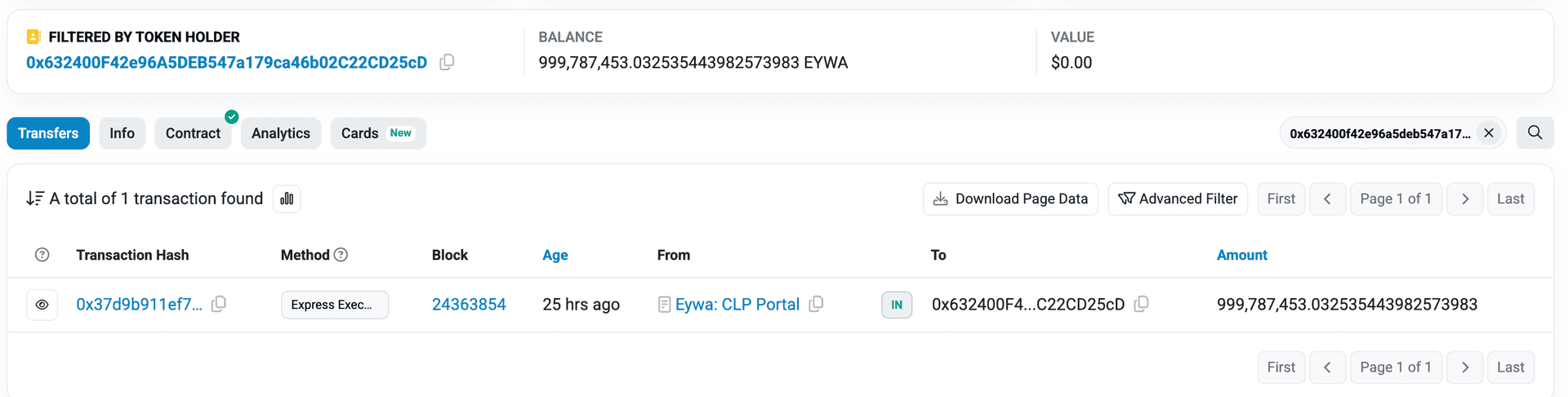
On Ethereum, the attacker carried out the same exploit and was able to extract 999,787,453 EYWA tokens, the native token of the CrossCurve protocol. However, due to the absence of any on-chain liquidity pools for EYWA on Ethereum and with the only available CEX later freezing deposits of the token the attacker was unable to liquidate the assets. As a result, the EYWA tokens remain held in the attacker’s EOA 0x632400f42e96a5deb547a179ca46b02c22cd25cd at the time of writing.
As of the time of writing this report, the majority of the stolen funds remain in the attacker’s wallet 0x851c01d014b1ad2b1266ca48a4b5578b67194834 on the Ethereum network, with no significant further movement observed.
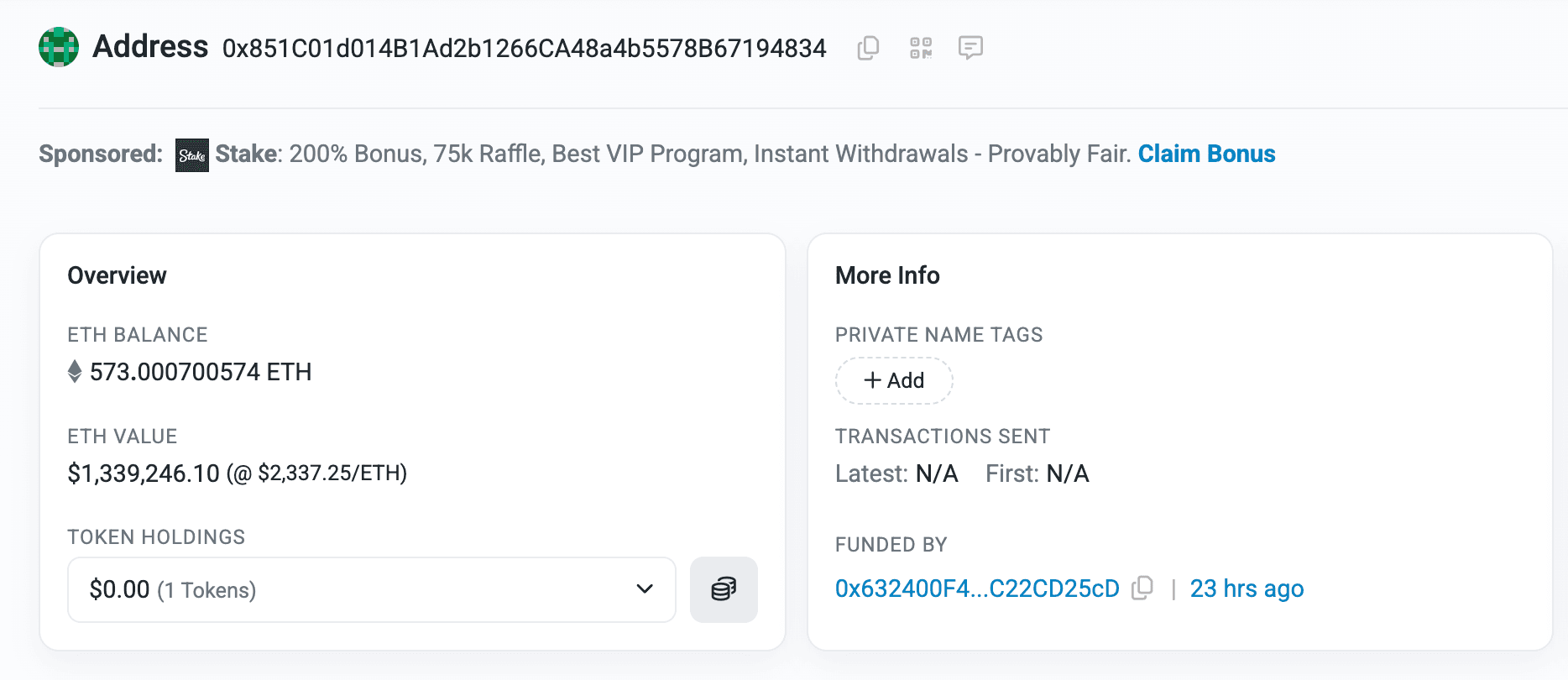
Post Attack Mitigation
CrossCurve team acknowledged the incident and initiated coordination with law enforcement and cybersecurity teams to mitigate the impact, and paused the contracts. The team has also been providing ongoing updates to the community through official posts on X.
The team attempted to contact the attacker and offered a 10% bounty for the return of the funds within a 72hour window.
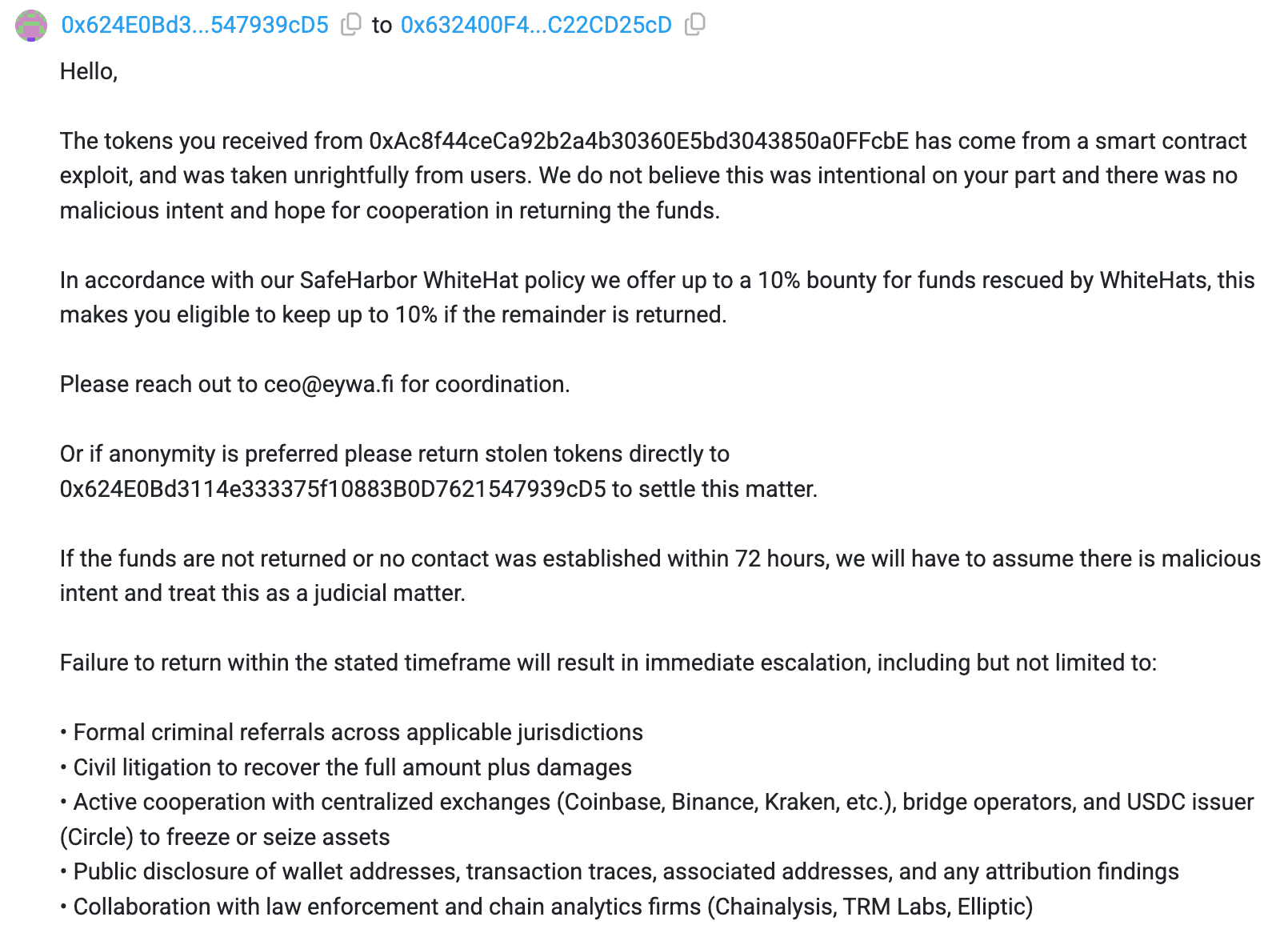
In addition, the team shared a detailed breakdown outlining the tokens impacted and the estimated value of the stolen assets.
The team attempted to contact the attacker and offered a 10% bounty for the return of the funds within a 72hour window.

In addition, the team shared a detailed breakdown outlining the tokens impacted and the estimated value of the stolen assets.
Relevant Address and Transactions
Attacker EOAs:
Attack Transaction:
0x37d9b911ef710be851a2e08e1cfc61c2544db0f208faeade29ee98cc7506ccc2
Victim Contract:
0xb2185950f5a0a46687ac331916508aada202e063
Bounty Offer Transaction:
0x53050b4bec3eb540741720e59f2b028d68179c36a56dabc005b2736f6152e7c6
ReceiveAxelar Contract:
0xb2185950f5a0a46687ac331916508aada202e063
Conclusion
The CrossCurve exploit demonstrates how weak access controls and misconfigured cross-chain validation can lead to critical failures. A publicly callable execution path and a confirmation threshold of one enabled arbitrary payload execution and large-scale token minting. While the team responded swiftly with mitigations and coordination efforts, the incident reinforces the need for strict authentication, proper quorum enforcement, and hardened cross-chain execution logic to prevent similar exploits.
Contents



