The Balancer Hack 2025 (Explained)
A complete technical breakdown of the Balancer Hack 2025, how the attack worked, what was exploited and security takeaways for DeFi teams.
On November 3, 2025, the Balancer V2 protocol fell victim to a devastating exploit in its Composable Stable Pools, draining approximately $125 million in user assets across Ethereum and multiple L2 chains. The attacker weaponized a subtle rounding inconsistency in the protocol's scaling math, artificially deflating pool invariants and enabling discounted BPT redemptions. This wasn't a brute force drain, it was a precision-engineered heist that exploited DeFi's mathematical underbelly, triggering copycat attacks on forks like Beets and Beethoven X before mitigations could catch up.
Hack Analysis
The attacker pulled off a two-stage, first, manipulate without cashing out, second, withdraw clean. All via batchSwap for atomicity, dodging single-swap guards. This execution targeted low-liquidity edges in pools like wstETH/rETH/cbETH, using micro-swaps to erode the invariant without triggering alarms.
In the preparation phase the attacker gathered pool state, token scaling factors, amplification (amp), fees, BPT rate, and current balances and computed a small trick amount tailored to the token decimals. They deployed a contract and repeatedly simulated swaps via a helper function 0x524c9e20 , passing arrays of balances, scaling factors, token indices, desired amountOut, amp and fee. The attacker used large iteration counts (initial value ≈ 100,000,000,000 and 25 loops to refine the swap sequence and find an amount that lands a target token on a wei-level rounding cliff.
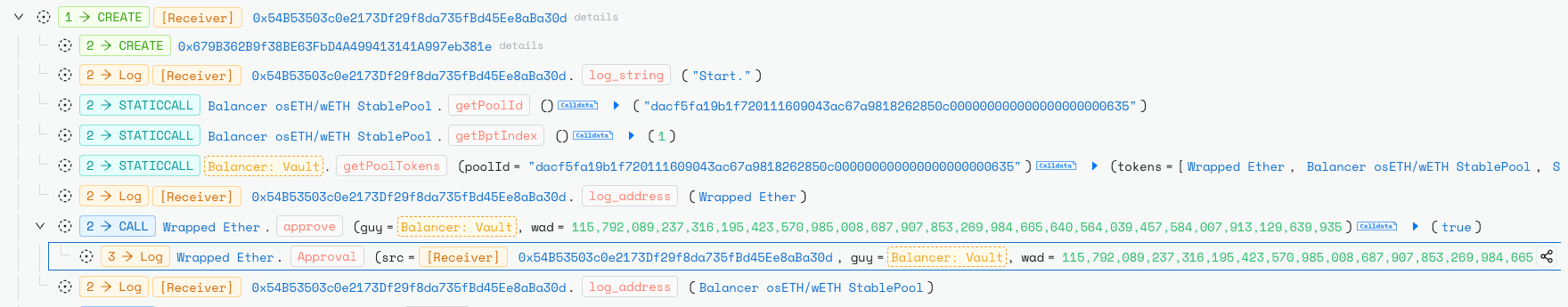
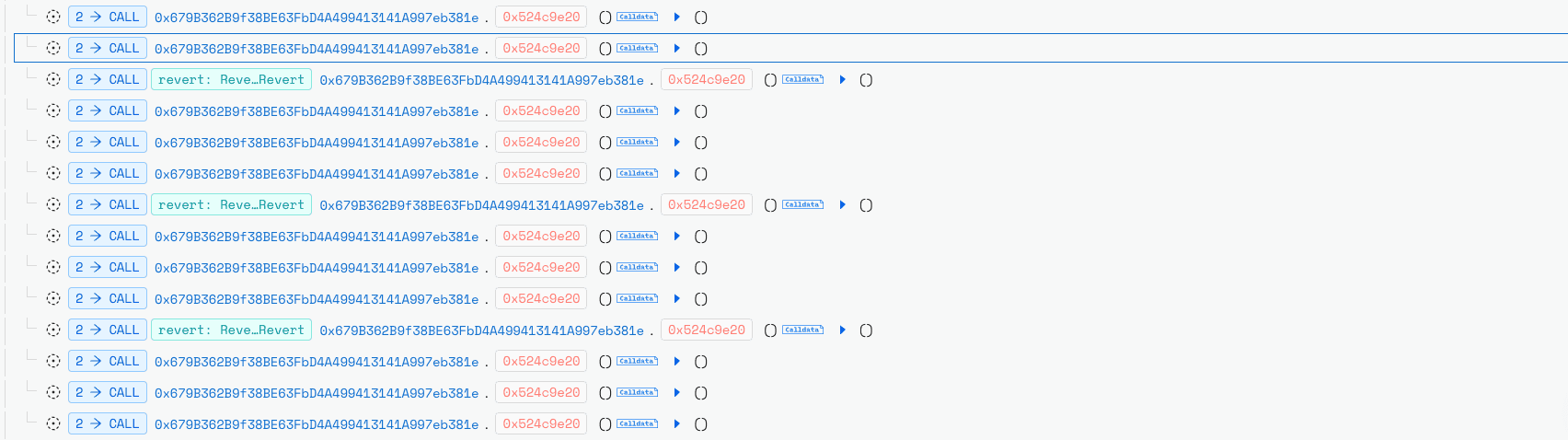
In the atomic batchSwap phase, the attacker executed the calibrated sequence on-chain. First they swapped BPT for underlyings to position one token (e.g., cbETH) at a rounding edge (e.g., balance = 9 wei). Next, they performed a crafted EXACT_OUT hop (e.g., swap amount = 8) that, due to the upscale/downscale rounding asymmetry, produced a smaller computed input/output than expected and silently reduced the pool invariant D .
Finally, they swapped the underlyings back into BPT at this deflated virtual price, pocketing excess BPT value. Repeating these swaps inside a single atomic transaction allowed the invariant to erode over many iterations without triggering typical sanity checks.
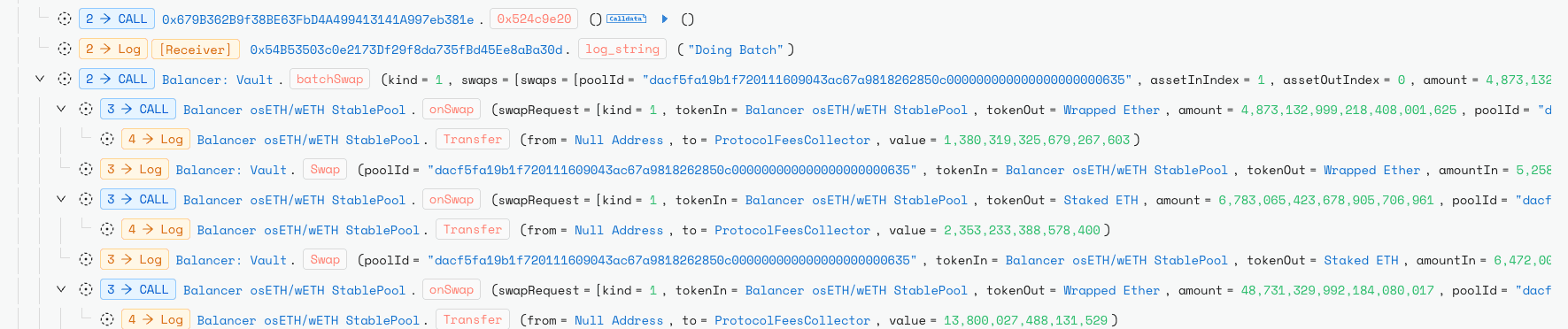
The attacker repeated the technique across multiple pools and chains (Arbitrum, Polygon, Base, Sonic, Opimism and forks), compounding the drain where pauses or protections were absent.
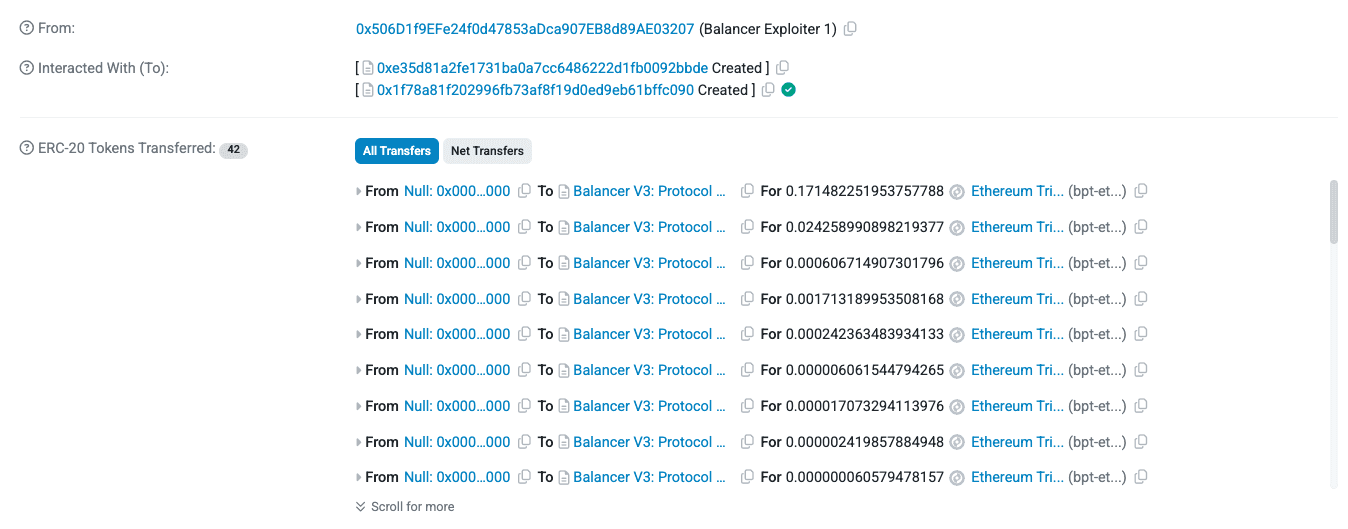
After accumulating underpriced BPT into the internalBalance the attacker later redeemed through managerUserBalancer to EOA 0xaa760d53541d8390074c61defeaba314675b8e3f
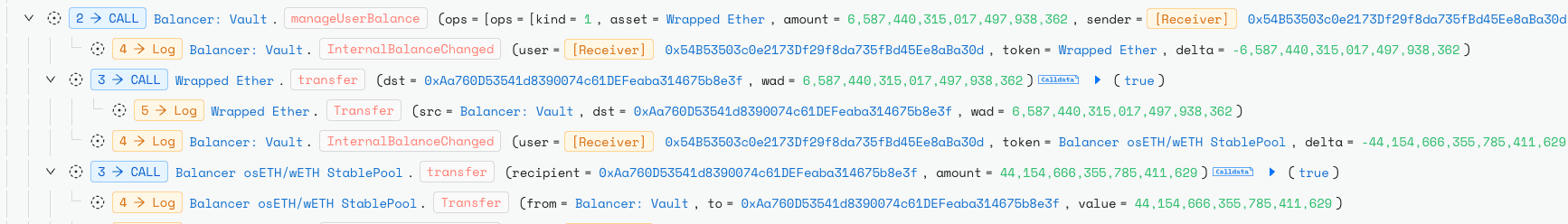
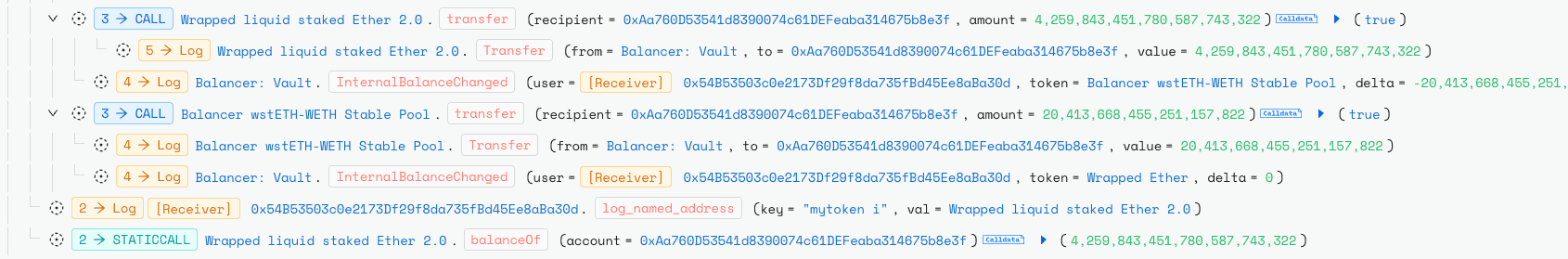
Root Cause
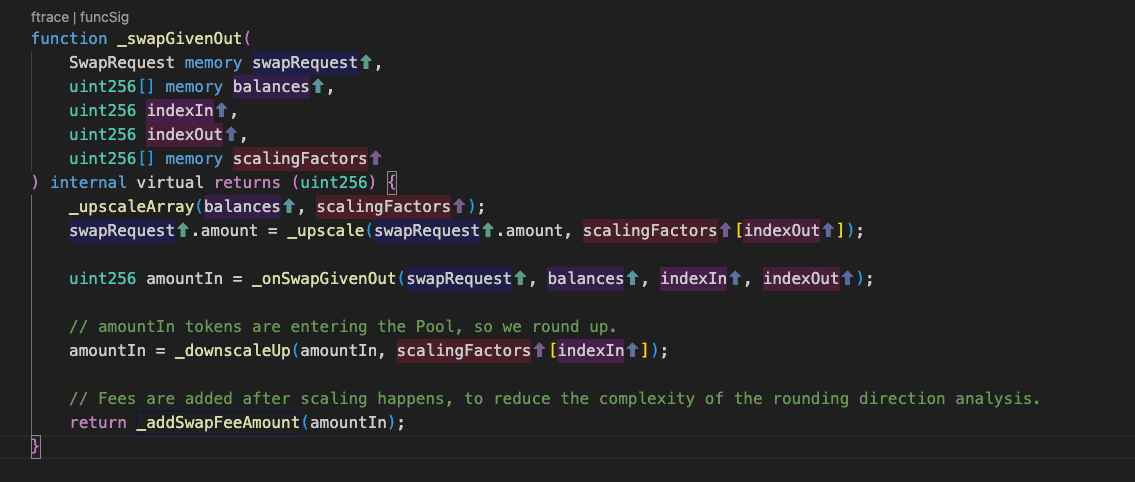
A rounding direction mismatch in Composable Stable Pools scaling logic allowed systematic precision loss to be weaponized against the pool invariant D. Upscaling used mulDown while downscaling used divUp/divDown, so an EXACT_OUT (_swapGivenOut) path could understate the required amountIn. Repeating carefully tuned micro swaps inside a single batchSwap() compounded tiny wei level truncations, quietly reducing D and thus BPT price ≈ D / totalSupply without triggering reverts or sanity checks. The attacker used simulations and an auxiliary StableMath replica to place swaps on rounding cliffs and maximize the leak, then monetized the depressed BPT in separate withdrawals. The vulnerability is therefore a deterministic precision-loss exploit caused by asymmetric rounding during scaling, amplified by batch atomicity and the protocol’s limited global pause capabilities.
Secure Your Protocol Against Precision-Based Exploits
Secure Your Protocol Against Precision-Based Exploits
A single rounding cliff drained Balancer across chains. Don’t wait for hidden math edges to get exploited. Get a precision-level security audit before mainnet!
Funds Flow After Attack
Following the withdrawal transaction, funds were forwarded to attacker EOA 0xAa760D53541d8390074c61DEFeaba314675b8e3f A portion remains on that address in ETH, WETH, and synthetic ETH.
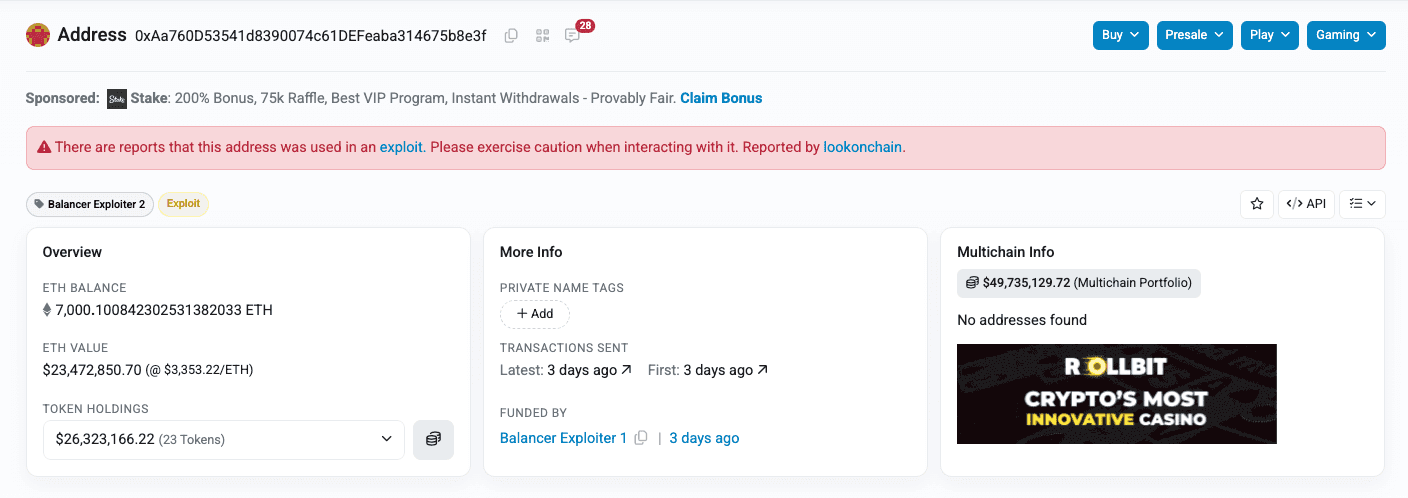
From Keyber Swap, the attacker converted synthetic ETH into native ETH and funded EOA
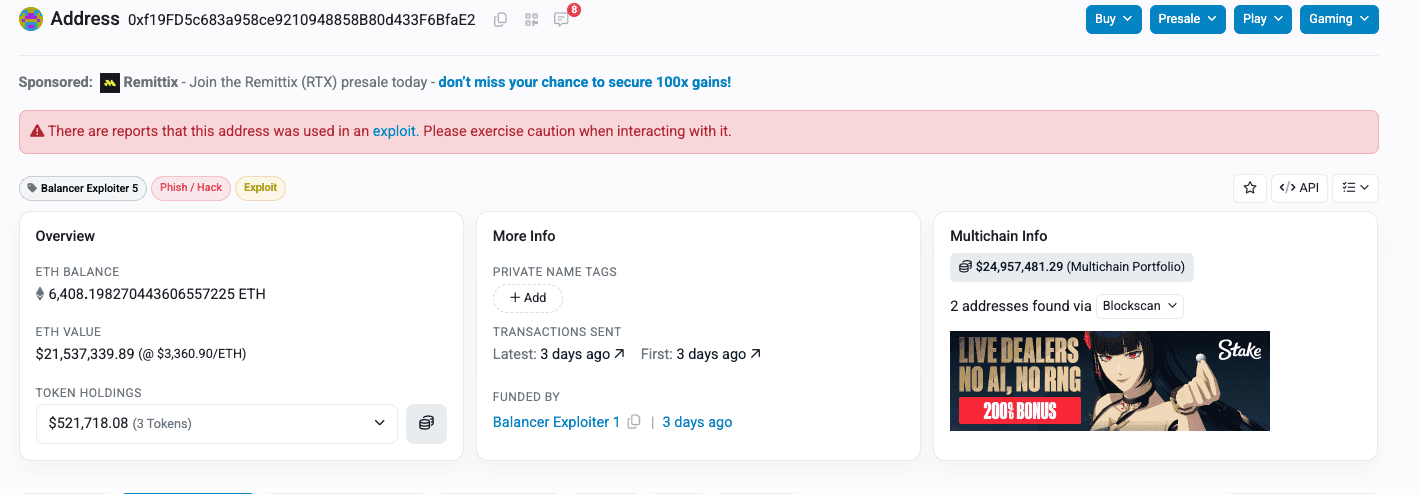
Meanwhile most of the funds are still siting in the attacker EOAs on different chains
Post Attack Mitigation
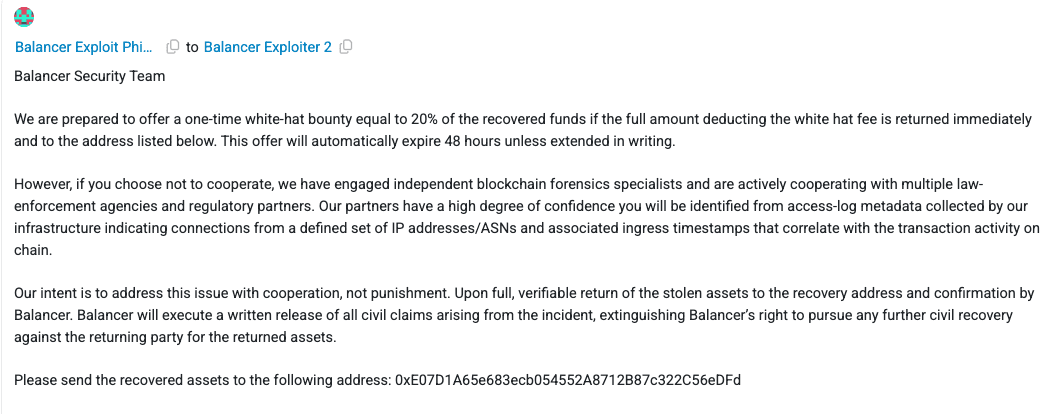
Balancer offers a one-time 20% white-hat bounty for immediate return to the recovery address, warns of active forensics and law-enforcement cooperation, and sets a 48-hour expiry.
Several rapid mitigation measures, ranging from automatic CSPv6 pauses, factory shutdowns, and gauge deactivations to coordinated partner freezes and major whitehat recoveries, significantly limited further losses and enabled large-scale asset retrieval across affected networks.

Users are advised to withdraw only from Recovery Mode pools, avoid impacted CSPv5 pools, and rely solely on Balancer’s official channels for confirmed guidance.
Relevant Address and Transactions
- Attack Transaction
- Ethereum: 0x6ed07db1a9fe5c0794d44cd36081d6a6df103fab868cdd75d581e3bd23bc9742
- Arbitrium: 0xe4dfc8b8b54eb7e101d59cd9f87f389186b2e8f6e188557ae9dfdbea2b12e703
- Polygon: 0x167993d4cc39771923a6cd11d2d6e73a1b68c7464ea3c76ba41fbd32df7a96da
- Sonic: 0xd7996c8e187b9bd539a04a4f39de4d8c7c1670c601134329937738b4dfa6f8ad
- Base: 0x29135f912d67db38478d0be70b9f2a1fab3b121b74d776f835ac66d6df134ec5
- Opitmism: 0x3c9d2d16404a79feed9876a79f168af334726ad3ee1371f581d50ebebfe6b8c6
- Withdraw Transaction
- Ethereum: 0xd155207261712c35fa3d472ed1e51bfcd816e616dd4f517fa5959836f5b48569
- Arbitrum: 0x4e5be713d986bcf4afb2ba7362525622acf9c95310bd77cd5911e7ef12d871a9
- Base: 0xa10459f63cac74d573c2f5445e13befa5b6a661d61103e786a7f6d3213b48aef
- Sonic: 0xc0cc599fa5c1ec2a43a96b018fd653783cf8dd3e6f670f94961c89b61ce8c0f9
- Optimism: 0xbd417633433e45c1dddf9fac7680f86dfde832c07b93f4de5ce69c6312d19381
- Polygon: 0x9630b26a49c451365989cbd2d9696ea3bdf02505bcb297b6239f330f114c9673
- Attacker EOAs:
- Balancer Vault: 0xce88686553686da562ce7cea497ce749da109f9f
Conclusion
The Balancer V2 exploit shows how a tiny rounding flaw can cascade into a $125M loss, proving that DeFi math breaks at its weakest decimal. Security now means defending against economic engineering, not just coding bugs. Protocols must enforce biased rounding, strengthen invariant checks, and include emergency pause mechanisms to stop precision-related failures before they spread. Batch swaps and composability amplify rounding risks, and forks inherit every upstream weakness. In short, harden your math, test adversarial edges, and secure your DeFi or your TVL can disappear overnight.
Contents



